文章全面概述了信息安全领域的研究、框架和方法论,涵盖威胁建模、Web应用安全、密码学及AI安全等内容,并分析了攻击与防御动态、职业发展路径及未来趋势。 2025-8-30 12:0:0 Author: danielmiessler.com(查看原文) 阅读量:3 收藏
A comprehensive collection of security research, frameworks, and methodologies developed over two decades in information security, covering assessment types, threat modeling, web application security, and the evolving security landscape.

Information Security Definitions
Authoritative taxonomy of security terminology and operational definitions

Comprehensive field analysis: attack/defense dynamics, career paths, and operational requirements

Threats, Vulnerabilities, and Risks
Formal classification system for security primitives

Secrecy (Obscurity) is a Valid Security Layer
Empirical analysis of obscurity as legitimate security control when properly implemented

Efficient Security Principle (ESP)
Game-theoretic model explaining persistent low security baselines through economic incentives

We Can't Really Affect AI Security
Application of ESP to AI security adoption dynamics

Information Security Assessment Types
Comprehensive taxonomy: vulnerability assessments, penetration tests, red teams, audits, threat modeling

Vulnerability Assessment vs. Penetration Test
Goal-oriented vs. list-oriented security testing methodologies
When to Use Different Assessment Types
Decision framework for assessment type selection

Team structures, operational roles, and interaction patterns
SOC terminology and operational classification

Password vs. TouchID vs. FaceID Threat Model
Quantitative threat modeling for authentication methods
Threat Modeling Against Apple's TouchID
Biometric authentication vulnerability analysis
Account recovery vulnerability assessment
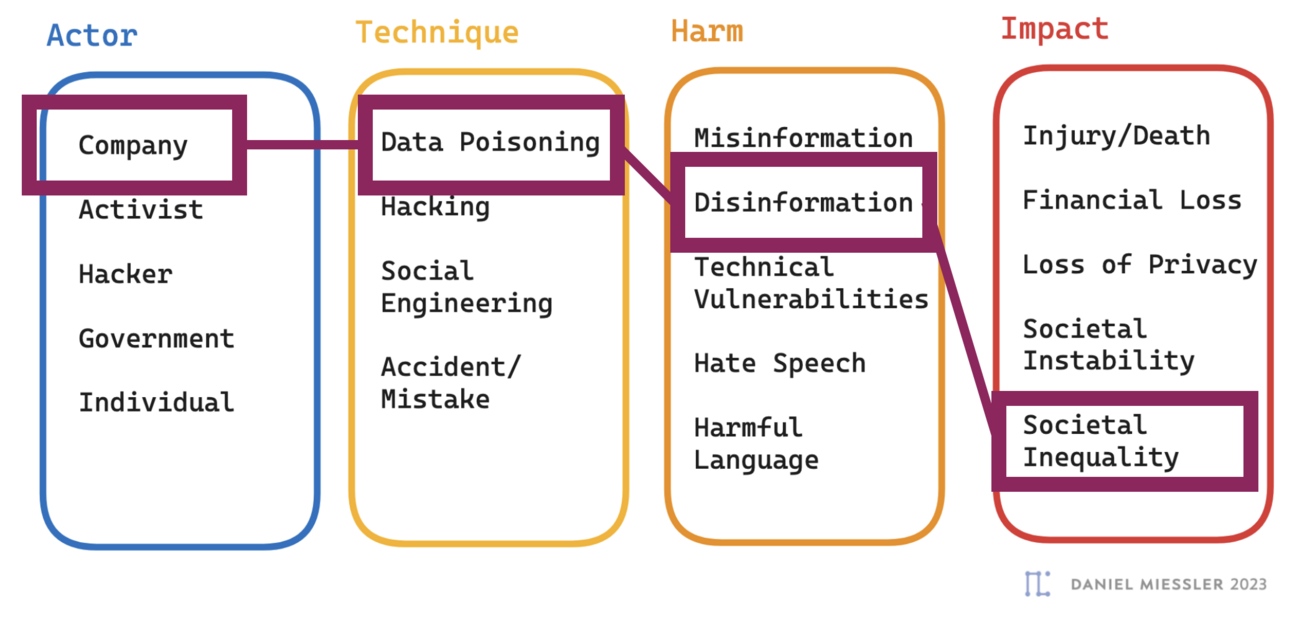
ATHI — AI Threat Modeling Framework
Structured framework: Actor, Technique, Harm, Impact analysis
The AI Attack Surface Map v1.0
Comprehensive AI system vulnerability taxonomy

How to Explain SQL Injection to Anyone
Pedagogical approach to SQL injection mechanics
Standard vs. Blind SQL Injection
Comparative analysis of injection techniques
Skill requirement analysis for web security
Attack vector classification and prevention
Cross-site request forgery exploitation patterns
The Sleepy Puppy XSS Framework
XSS payload orchestration system
IoT + SSRF: A New Attack Vector?
Server-side request forgery in IoT environments
Browser security model fundamentals

High-performance web fuzzing methodology
Advanced payload generation techniques

amass — Attack Surface Mapping
Comprehensive reconnaissance automation
High-speed port scanning techniques

Packet capture and analysis fundamentals
Advanced reconnaissance methodology
Firewall architecture and implementation patterns
Demilitarized zone design principles
Port security fundamentals
Intrusion detection implementation
ML in Cyber Attack and Defense
ML application patterns in security operations

Labor market structural analysis
Security rating service critique
Build a Successful InfoSec Career
Career trajectory optimization strategies
Technical interview preparation framework
More Security Research
Additional security content includes:
- Everyday Threat Modeling — Practical threat modeling approaches
- My Problem With Threat Intelligence — Critical analysis
- Analysis of the 2021 Verizon DBIR — Breach statistics
- Bypassing WAF Anti-automation — Evasion techniques
- Capturing Out-of-Band Interactions — Advanced testing
- Shodan — Internet-wide scanning techniques
- Getting IP Location in Wireshark — Network forensics
- Purple Team — Collaborative security testing
- The Difference Between Security and Privacy — Core concepts
- Dead Drops and Security Through Obscurity — Operational security
- The Difference Between a Penetration Test and a Red Team Engagement — Testing methodology distinctions
- Security and Privacy Are Not Actually That Different — Unified framework
- More Confusion on Data Security vs Privacy — Industry terminology
如有侵权请联系:admin#unsafe.sh