研究人员开发了一种名为BitlockMove的新概念工具,利用BitLocker的DCOM接口和COM劫持技术,在已登录用户的会话中远程执行代码,无需窃取凭证或模拟账户。该工具通过劫持特定的BitLocker相关COM类,在目标用户上下文中运行恶意代码,具有较强的隐蔽性。该技术主要针对Windows客户端系统中的工作站而非服务器,并可通过监控特定行为进行检测。 2025-9-15 04:28:42 Author: cybersecuritynews.com(查看原文) 阅读量:1 收藏
A new proof-of-concept (PoC) tool named BitlockMove demonstrates a novel lateral movement technique that leverages BitLocker’s Distributed Component Object Model (DCOM) interfaces and COM hijacking.
Released by security researcher Fabian Mosch of r-tec Cyber Security, the tool enables attackers to execute code on remote systems within the session of an already logged-on user, bypassing the need to steal credentials or impersonate accounts.
The BitlockMove tool exploits how certain COM classes, when configured as “INTERACTIVE USER,” can spawn a process in the context of the current user’s session.
Suppose these processes are also susceptible to COM hijacking. In that case, an attacker can remotely modify the registry, deliver a malicious DLL via Server Message Block (SMB), and trigger its execution through DCOM.
This technique is particularly stealthy because the malicious code runs directly within the target user’s context, generating fewer indicators of compromise compared to traditional methods like credential theft from LSASS.
The PoC specifically targets the BDEUILauncher Class (CLSID ab93b6f1-be76-4185-a488-a9001b105b94), which can launch several processes. One of these, BaaUpdate.exe, is vulnerable to COM hijacking when started with specific parameters.
The tool hijacks a related BitLocker CLSID (A7A63E5C-3877-4840-8727-C1EA9D7A4D50) from the remote system. Since BitLocker is most commonly enabled on Windows client operating systems, this lateral movement technique is primarily effective against workstations rather than servers.
BitlockMove’s Modes of Operation
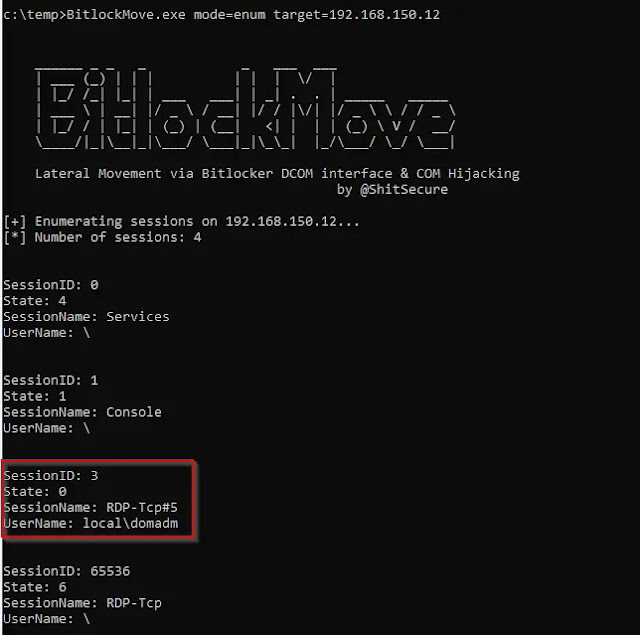
The tool, written in C#, operates in two distinct modes: enumeration and attack.
- Enum Mode: An attacker can use this mode to identify active user sessions on a target host. This allows the threat actor to select a high-privilege user, such as a domain administrator, for the attack.

- Attack Mode: In this mode, the tool executes the attack. The attacker specifies the target host, the username of the active session, a path to drop the malicious DLL, and the command to be executed. The tool then performs the remote COM hijack, triggers the payload, and cleans up by removing the hijack from the registry and deleting the DLL.

Defenders can detect this technique by monitoring for specific behaviors. Key indicators include the remote COM hijacking of the targeted BitLocker-related CLSID, followed by the BaaUpdate.exe process loading a newly dropped DLL from the hijack location.
Suspicious subprocesses spawning from BaaUpdate.exe or BdeUISrv.exe are also strong signs of compromise. Security teams can build threat hunting queries to look for the presence of the BdeUISrv.exe process, as its legitimate use is rare.
The PoC uses a hardcoded DLL, making signature-based detection straightforward; however, attackers can easily create custom DLLs to evade such defenses.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
如有侵权请联系:admin#unsafe.sh
