
Morpheus通过自动化工具帮助安全团队实现NIST和MITRE框架的应用,覆盖识别、保护、检测、响应和恢复五个核心领域,并支持MITRE ATT&CK和D3FEND框架,提供动态playbook生成、主动响应策略及高管报告功能。 2025-9-18 16:36:44 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Security teams don’t need to reinvent how to run operations — they just need tools that let them implement what’s already proven to work. The NIST Cybersecurity Framework (CSF) and MITRE ATT&CK/D3FEND are foundational models for how mature organizations prevent, detect, respond, and recover from threats.
Unfortunately, many platforms make aligning to these frameworks manual, static, or overly rigid.
It gives organizations a way to build, visualize, and evolve their SOC processes, using NIST and MITRE as operational scaffolding, but without being locked into brittle playbooks or abstract policies. And it does this while enabling full automation of Tier 1 and Tier 2 tasks, proactive response strategies, and executive-level reporting.
Morpheus + NIST: Operationalizing the Core Functions
The NIST CSF breaks security operations into five domains: Identify, Protect, Detect, Respond, and Recover. Morpheus enables teams to address all five, not in policy alone, but through live, automated action:
- Identify: Aggregates asset data and exposure context from integrated tools to inform risk posture.
- Protect: Enforces configuration and identity policies across systems automatically.
- Detect: Ingests and investigates alerts from SIEM, EDR, XDR, and cloud sources with no human required.
- Respond: Autonomously contains threats through orchestrated actions across endpoints, identity systems, email, and more.
- Recover: Documents the full investigation and mitigation path for post-mortem reviews and compliance.
Morpheus gives teams the ability to go from framework on paper to functionality in production.

Built-In Support for MITRE ATT&CK and D3FEND
D3 Security has supported the MITRE ATT&CK framework since 2018, long before it became a de facto industry standard. That’s more than lip service. Morpheus includes:
- A full ATT&CK dashboard to visualize tactics and techniques seen in your environment
- Automated mapping of incoming alerts and investigations to MITRE TTPs
- The ability to pivot from detection patterns to automated responses based on observed behavior
- Correlation of adversary behavior across tools, data sources, and tenants (for MSSPs/MDRs)
Additionally, Morpheus supports MITRE D3FEND techniques for hardening, detection, deception, and eviction, making it possible to proactively build playbooks that mirror modern defensive strategy.
Framework-Based Reporting That Actually Shows ROI
The ATT&CK dashboard isn’t just for SOC analysts, it’s for CISOs and security leaders too.
SOC managers and CISOs use it to:
- Show which stages of the attack chain were blocked, investigated, or responded to
- Provide hard numbers on the techniques being seen, and more importantly, stopped
- Communicate the value of autonomous investigation in preventing escalation
- Justify spend on automation or prove the effectiveness of an in-house or outsourced SOC
Instead of just showing volume, you’re showing impact.
“Here are the lateral movement attempts we stopped last month. Here are the credential misuse patterns we resolved autonomously. Here’s how many attacks were stopped before they became breaches.”
This turns security from a cost center to a measurable business enabler.
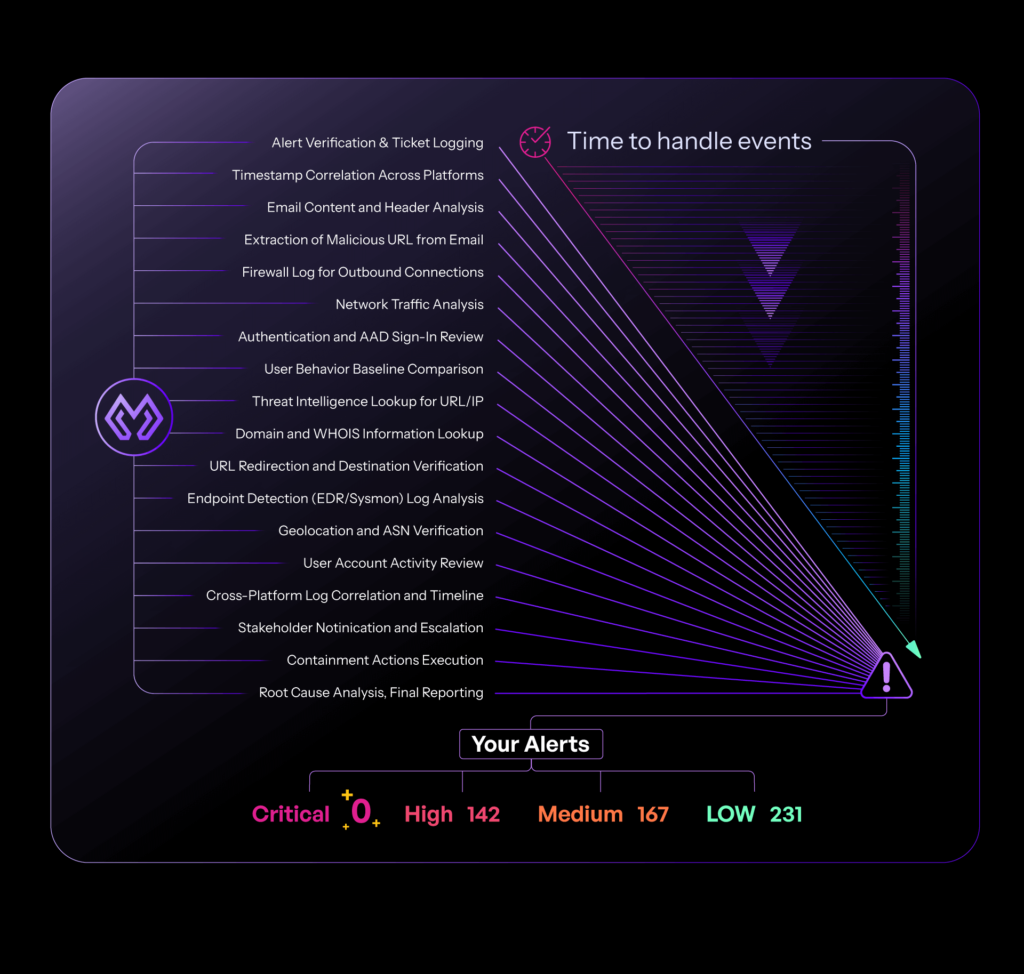
Morpheus Enables Framework-Inspired Playbook Creation: With or Without Live Alerts
Security teams using Morpheus don’t have to choose between prebuilding brittle playbooks or waiting passively for alerts.
They get the best of both worlds:
 Truly Autonomous, Context-Aware Investigations
Truly Autonomous, Context-Aware Investigations
When alerts or events flow into Morpheus, from sources like CrowdStrike, SentinelOne, Defender, SIEMs, or cloud platforms, the platform can:
- Autonomously generate a dynamic playbook on the spot
- Tailor investigation steps to the alert’s origin, type, and threat context
- Enrich with internal and external data sources
- Adapt in real time as new evidence is uncovered
- Make containment or escalation decisions based on policy and IRPS scoring
This is not a static YAML flow or drag-and-drop diagram. It’s a live, self-adjusting investigation engine that builds workflows based on real input, behavior, and environment.
 Proactive Playbook Creation with Morpheus PlayMaker
Proactive Playbook Creation with Morpheus PlayMaker
Alternatively, teams can use the PlayMaker module to prebuild playbooks for likely scenarios, inspired by frameworks like MITRE D3FEND or NIST CSF.
These proactive playbooks are:
- Built using natural-language conditions and logic
- Tied to the organization’s actual stack and policies
- Modular, easy to update, and easy to clone for customer-specific variations (for MSSPs/MDRs)
- Fully simulated before deployment. No guesswork, no breakpoints
 Better Than SOAR. Better Than Hyperautomation.
Better Than SOAR. Better Than Hyperautomation.
Traditional SOAR and hyperautomation systems are often:
- Over-engineered and difficult to debug
- Dependent on rigid conditions and hand-authored scripts
- Time-consuming to maintain as environments change
In contrast, Morpheus enables:
- Faster deployment: hours or days, not weeks or months
- Smarter execution: playbooks that adjust themselves
- Less engineering burden: and fewer playbook “breaks” when upstream tools evolve
Whether you’re designing ahead of time or reacting in real time, Morpheus gives you a faster, more flexible, and more reliable path to automation, deeply aligned with your frameworks and environment.
Frameworks as the Blueprint, Morpheus as the Builder
Security frameworks like NIST and MITRE are the blueprint. They help teams know what to aim for. But having the blueprint isn’t enough — you need a system that:
- Works across your specific tools, environments, and roles
- Automates what can be automated, and guides what can’t
- Documents outcomes clearly for internal and external audiences
- Scales as your operations grow
That’s what Morpheus delivers, not as a feature layer, but as infrastructure for intelligent, autonomous operations.
A SOC That Adapts to You, and to Adversaries
Frameworks give you structure. Morpheus gives you motion.
When combined, you get a SecOps function that:
- Detects real threats
- Responds at machine speed
- Documents what happened and why
- Improves over time
- And clearly communicates its value, both to the business and to external regulators
If you’re looking to build or modernize your SOC around a trusted, outcome-oriented model, start with NIST and MITRE, and scale it with Morpheus.
Want to see how Morpheus maps to MITRE ATT&CK and automates response at every stage? Book a demo here.
The post Operationalizing NIST and MITRE with Autonomous SecOps appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Alex MacLachlan. Read the original post at: https://d3security.com/blog/operationalizing-nist-and-mitre-autonomous-secops/
如有侵权请联系:admin#unsafe.sh
