
SystemBC 是一个代理僵尸网络,通过感染存在漏洞的商业虚拟服务器(VPS)维持约 1500 个僵尸程序,为恶意流量提供通道。其客户包括勒索软件团伙和其他网络犯罪服务提供商。该网络利用未修补的安全漏洞长期控制被感染服务器,并隐藏恶意活动以规避检测。 2025-9-18 14:45:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:15 收藏
The operators of the SystemBC proxy botnet are hunting for vulnerable commercial virtual private servers (VPS) and maintain an average of 1,500 bots every day that provide a highway for malicious traffic.
Compromised servers are located all over the world and have at least one unpatched critical vulnerability, some of them being plagued by tens of security issues.
SystemBC has been around since at least 2019 and has been used by various threat actors, including several ransomware gangs, to deliver payloads.
It lets attackers route malicious traffic through the infected host and hide command-and-control (C2) activity to make detection more difficult.
SystemBC’s customers
According to researchers at Lumen Technology’s Black Lotus Labs, the SystemBC proxy network is built for volume with little concern for stealth. It also powers other criminal proxy networks and has “extremely long average infection lifetimes.”
Based on the researchers’ findings, neither customers nor operators of SystemBC care about keeping a low profile, since the bots’ IP addresses are not protected in any way (e.g. through obfuscation or rotation).
SystemBC has more than 80 command-and-control (C2) servers, which connect clients to an infected proxy server, and it fuels other proxy network services.
One malicious service called REM Proxy relies on around 80% of SystemBC’s bots, providing tiered services to its customers, depending on the required proxy quality.
A large Russian web-scraping service is another significant SystemBC customer, along with a Vietnamese-based proxy network called VN5Socks or Shopsocks5.
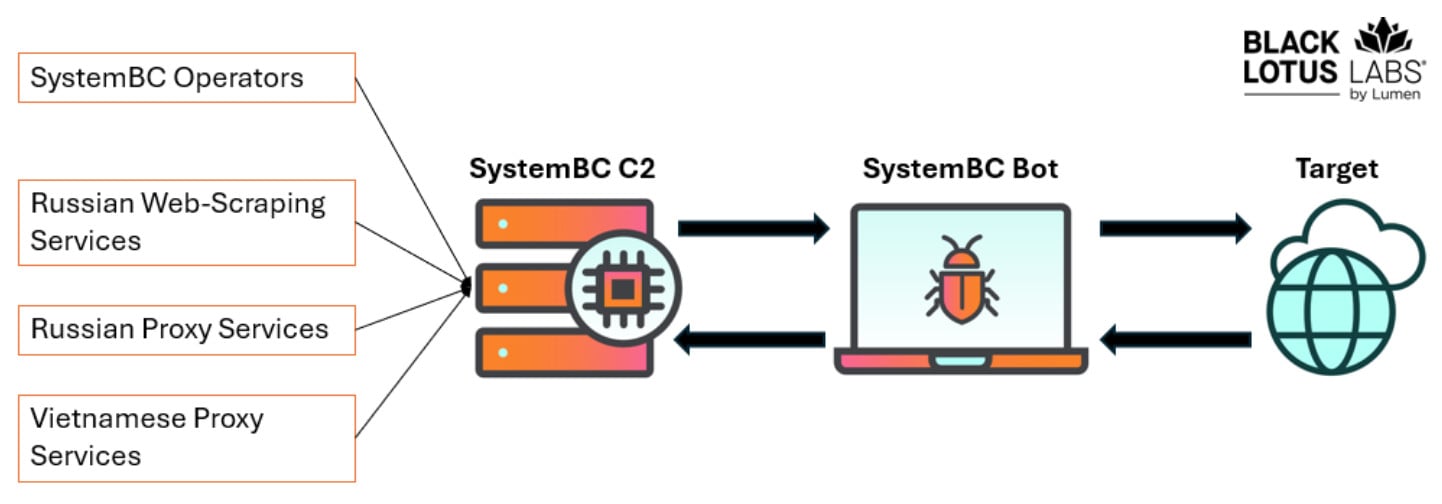
source: Black Lotus Labs
However, the researchers say that SystemBC operators make the most use of it to brute-force WordPress credentials that are likely sold to brokers who inject sites with malicious code.
Targeting vulnerable VPSs
Almost 80% of the SystemBC network of 1,500 daily bots consists of compromised VPS systems from multiple “large commercial providers.”
Black Lotus Labs says that this allows for a longer-than-average infection lifespan, with nearly 40% of the systems staying compromised for more than a month.
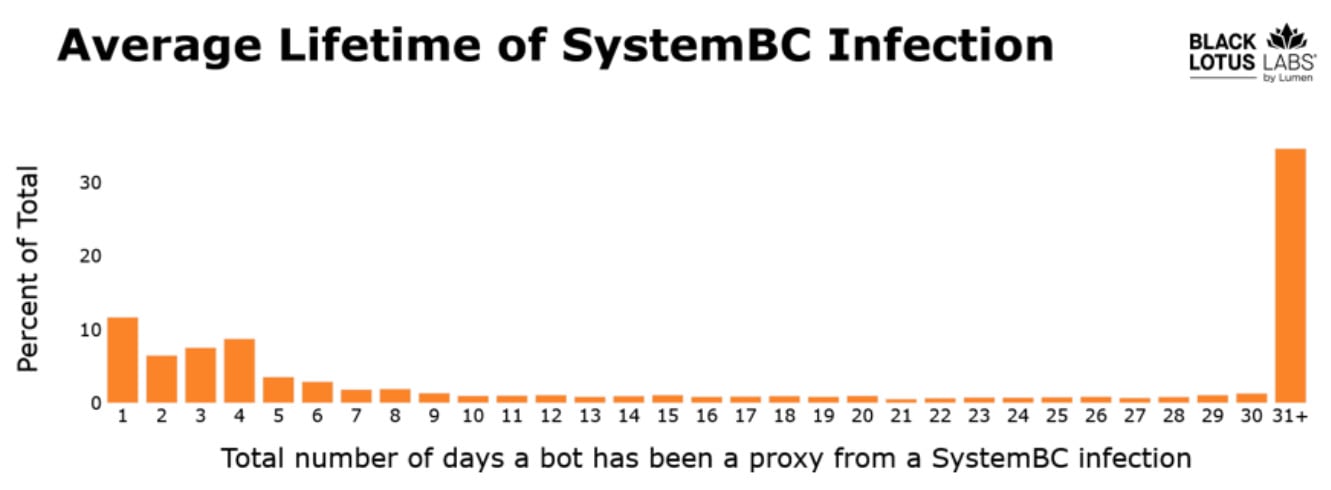
All the infected servers have multiple “easy-to-exploit” vulnerabilities, the average being 20 unpatched security issues, and at least one critical-severity one.
The researchers also found one system in Alabama, which the Censys internet intelligence platform and search engine listed as having 161 security vulnerabilities.
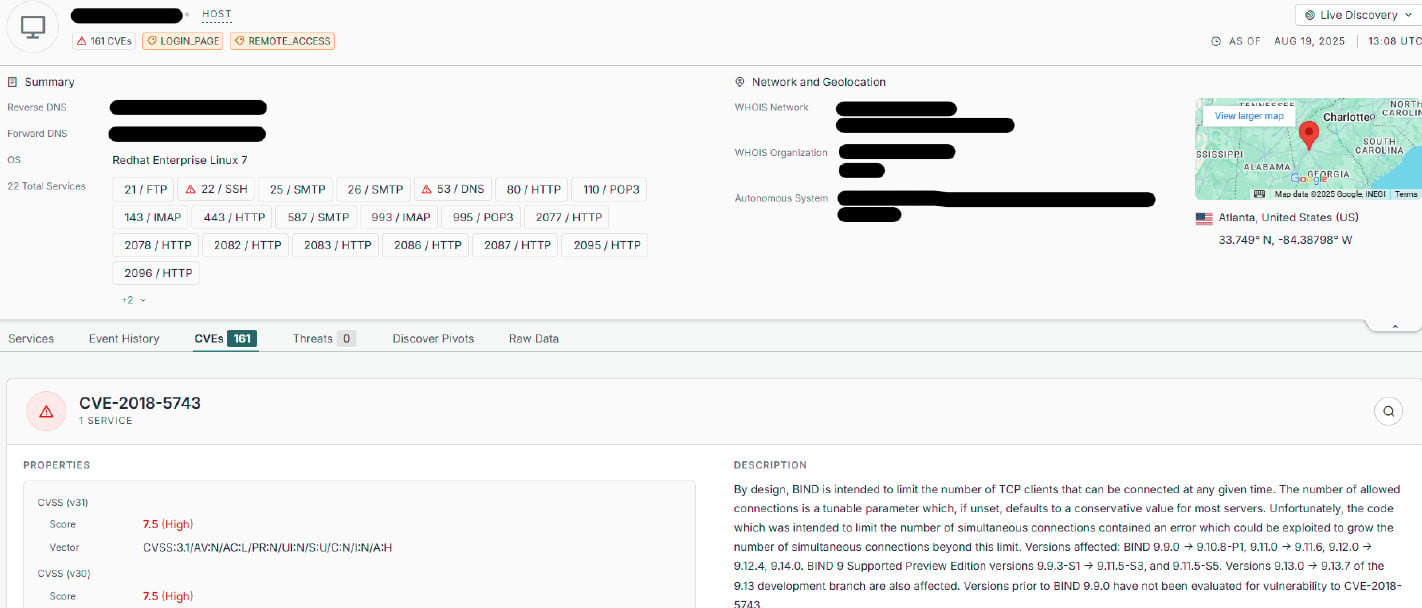
source: Black Lotus Labs
By compromising VPS systems, SystemBC enables high-volume, stable traffic for its customers, which is not possible with residential proxy networks based on SOHO devices.
By running the SystemBC malware in a simulated environment, the researchers observed “a particular IP address generate an excess of 16 gigabytes of proxy data” in just 24 hours.
“This amount of data is an order of magnitude greater than what is commonly observed in typical proxy networks,” said Black Lotus Labs researchers in a report shared with BleepingComputer.
Based on the company’s global IP telemetry, one address, 104.250.164[.]214, appears to be at the core of victim recruiting activity and also hosts all 180 SystemBC malware samples.
According to the researchers’ analysis, a newly infected server downloads a shell script, which has comments in Russian and directs the bot to run every SystemBC sample at the same time.
The proxy network has been active for a long time and has resisted even law enforcement operations, such as Endgame, which targeted the malware droppers for multiple botnets, including SystemBC.
Black Lotus Labs provides a detailed technical analysis of the SystemBC proxy malware, along with indicators of compromise, to help organizations identify compromise attempts or disrupt the operation.
如有侵权请联系:admin#unsafe.sh
