赌场作为关键基础设施面临高风险,内部渗透测试揭示756个弱点和143个攻击路径,涉及敏感数据泄露、勒索软件暴露等严重威胁。通过修复SMB签名、禁用多播DNS等措施,显著提升安全性。 2025-9-17 13:0:0 Author: horizon3.ai(查看原文) 阅读量:18 收藏
A Pentest Wednesday® Story
Casinos aren’t just entertainment hubs — they operate like banks and critical infrastructure rolled into one. Behind every slot machine and sportsbook is a complex IT environment that processes millions of transactions, safeguards patron identities, and ensures compliance with federal oversight and financial regulations. The stakes are high: a single breach can cascade into operational outages, regulatory violations, and multimillion-dollar fines.
High-profile incidents have shown that casino cybersecurity gaps carry immediate, tangible consequences. In 2023, MGM Resorts suffered a ransomware attack that disrupted operations across Las Vegas properties, costing over $100 million in lost revenue and remediation expenses. That same year, Caesars Entertainment disclosed that attackers stole loyalty program data and demanded a ransom — highlighting the risk of regulatory scrutiny and class-action fallout.
And it’s not just the giants on the Strip. In April 2025, Jackpot Junction Casino in Minnesota was hit with ransomware that forced slot machines offline and disrupted tribal government operations. For gaming operators of all sizes, the risks are real — and the consequences immediate.
For one U.S. casino, the wake-up call didn’t come from regulators or an incident — it came from their first NodeZero® pentest. Within hours, they discovered that despite segmentation, modern tools, and a mature stack, simple, repeatable weaknesses could be chained into full-scale compromise.
Impact
On June 12, 2025, the casino launched its first autonomous internal pentest. NodeZero ran for 12 hours and 4 minutes, completing the next morning. The results were sobering:
- 756 weaknesses uncovered
- 143 attack paths exploited
- 342 credentials compromised (51 rated critical)
- 41 hosts compromised across production systems
These weaknesses led directly to confirmed business impacts:
- Sensitive Data Exposure (46 instances) — access to PII, financial account data, and other regulated information
- Ransomware Exposure (11 instances) — compromised credentials with write access to SQL and application servers that could have been encrypted for extortion
- Host Compromise (82 instances) — persistence and lateral movement proven across critical infrastructure
- Domain User Compromise (4 instances) — demonstrating privilege escalation and identity misuse
Mapped against MITRE ATT&CK®, the operation triggered 16,000+ discovery events, 4,200 credential access events, and nearly 3,000 lateral movement events, proving how an attacker could move from reconnaissance to domain compromise in a single campaign.
Internal Pentest At A Glance
Duration:
12h 4m
Hosts Assessed:
1,700+
Weaknesses Found:
756
Credentials Compromised:
342 (51 critical)
Hosts Compromised:
41
Attack Paths Exploited:
143
Background
The casino had invested in endpoint defenses, segmentation, and vulnerability scanning. Security leadership asked the question every CISO eventually faces: “Are we actually secure?” For years, vulnerability reports suggested progress, but none could prove whether defenses would withstand a real-world attack. The first NodeZero pentest provided that proof, and it was a reality check.
We did our first major test and it was like a massive disaster…“
Manager, Information Security
Mitigation
NodeZero revealed that common but systemic weaknesses were behind most of the 137 attack paths exploited — issues that looked minor in isolation but, when chained together, created catastrophic risk.
To reduce the blast radius of future attacks, Horizon3.ai’s Customer Success team recommended that the casino focus on the following:
- Require SMB signing — enforcing SMB signing across hundreds of services would block impersonation attacks and cut off a major pathway to domain compromise.
- Disable multicast DNS — turning off legacy name resolution protocols would prevent credential capture and replay, breaking more than 130 potential attack paths.
- Eliminate local admin credential reuse — enforcing unique local administrator passwords would ensure that one stolen password couldn’t unlock entire network segments.
- Harden endpoint controls — deploying and tuning defenses to prevent LSASS and SAM dumping would stop attackers from harvesting identities directly from memory.
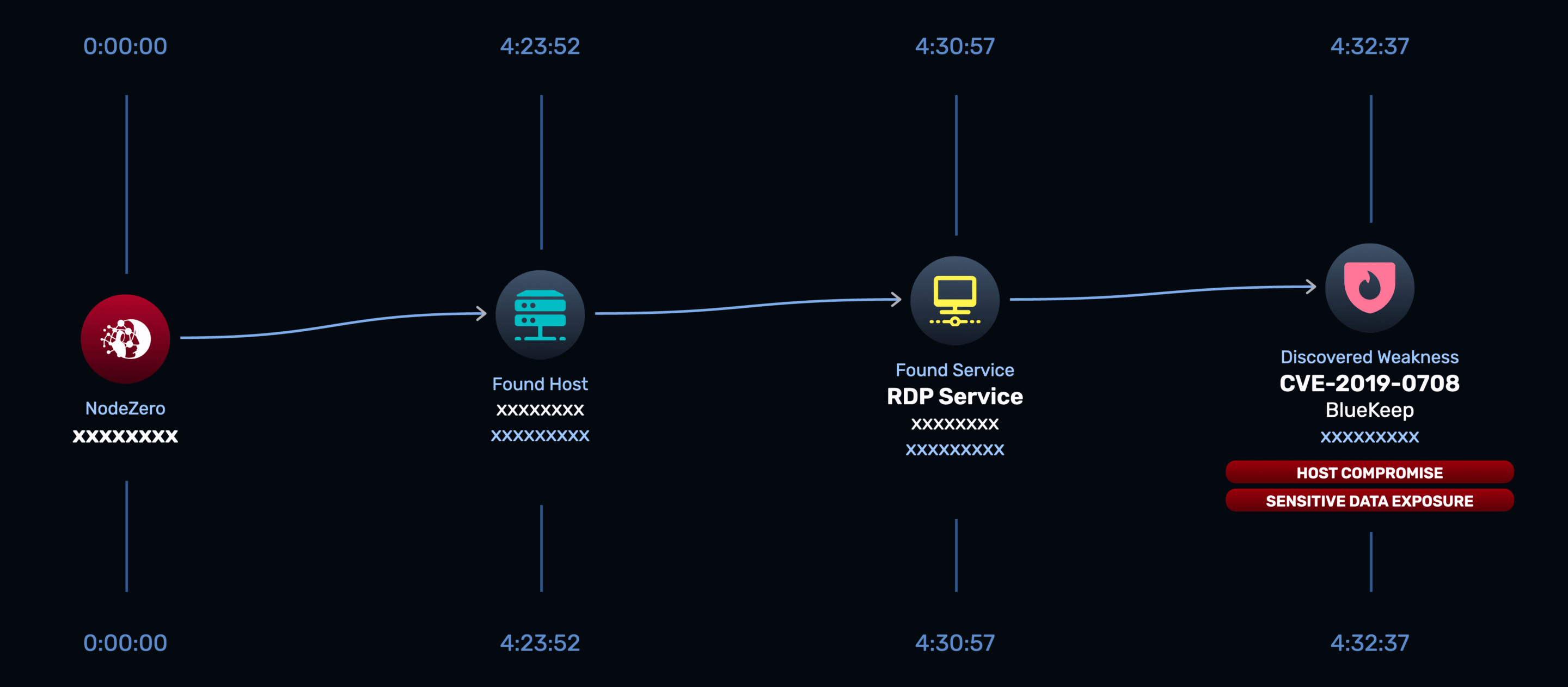
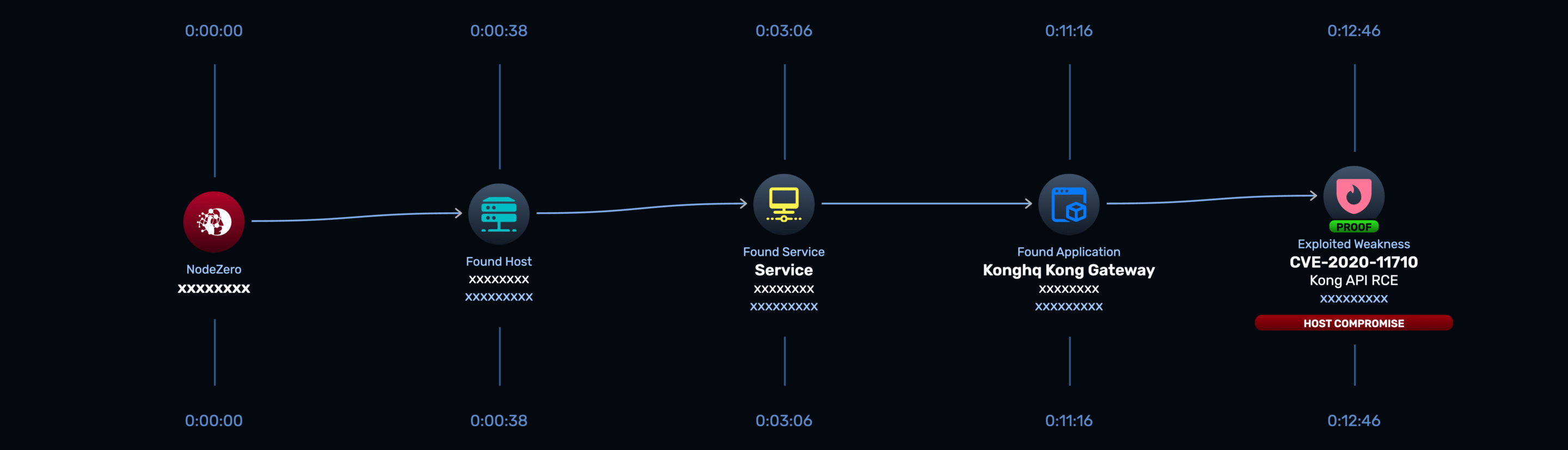
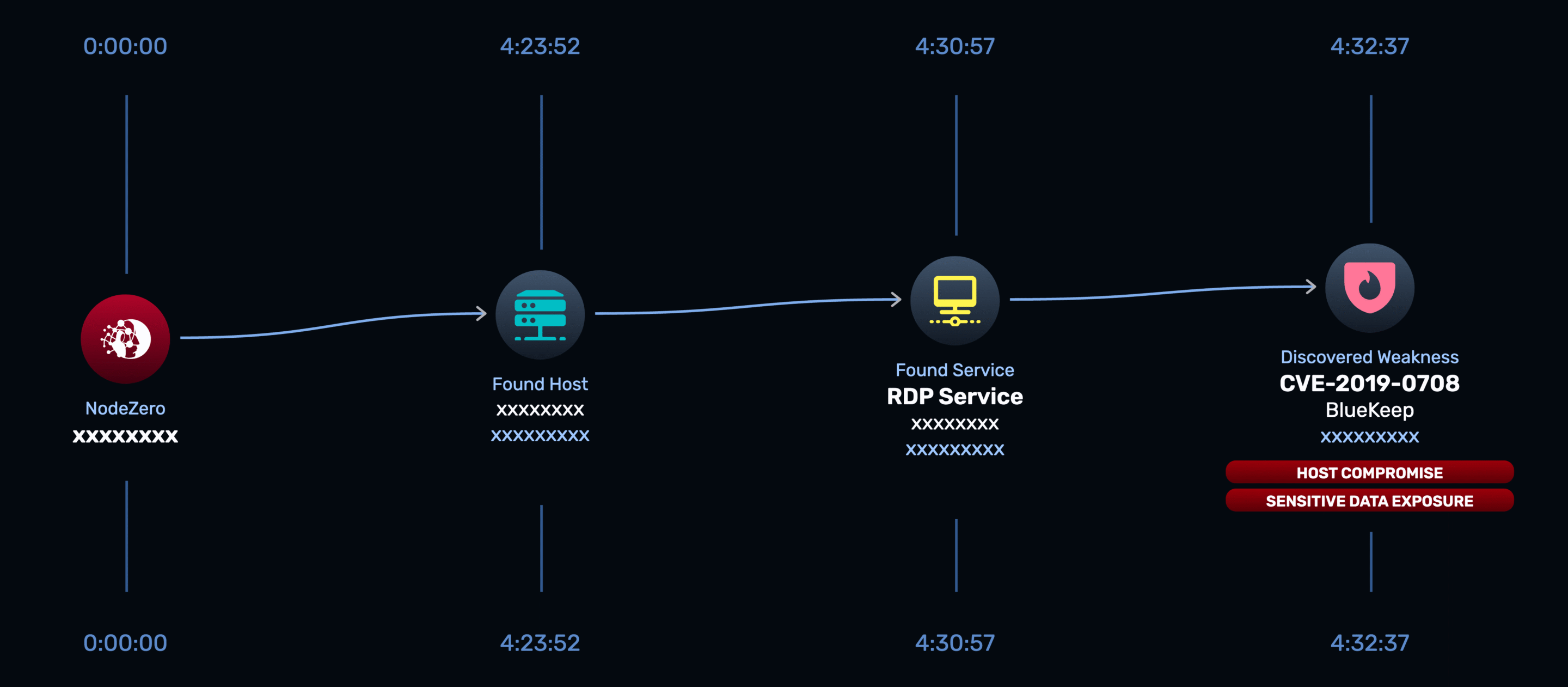
Just as alarming were the other exploitable vulnerabilities uncovered: BlueKeep, PrintNightmare, and a Kong API RCE. These aren’t obscure CVEs — they’re infamous vulnerabilities that have been weaponized in the wild for years. Combined with a pattern of weak or default credentials across services, the findings made clear that attackers wouldn’t need advanced techniques to compromise the environment — common methods would have been enough.
Most blue teams know they’re vulnerable — what they don’t know is where. Traditional tools give probabilities, not proof. Until NodeZero, they had no way to test like an attacker would. They really appreciate being able to spin it up quickly to test specific areas or run targeted operations on demand.”
Horizon3.ai Customer Success
As part of a layered defense strategy, the Customer Success team also recommended deploying NodeZero Tripwires™ — fake credentials and fake data that, if accessed, would trigger SOC alerts. These compensating controls would provide immediate detection value while systemic issues are being remediated, ensuring that if an adversary attempted the same techniques in production, the SOC could respond quickly.
By addressing systemic weaknesses and considering deception-based detection, the casino can shrink its attack surface and contain adversary movement — limiting the damage any single compromise could cause.
Remediation
With guidance from our Customer Success team and the flexibility of the NodeZero platform, the casino adopted a crawl–walk–run approach.
Crawl: The first priority was fixing the most critical problems first. That meant methodically enabling SMB signing across the environment, shutting off legacy protocols, and enforcing unique local admin passwords with LAPS. The work required careful coordination with applications and vendor dependencies to ensure nothing broke, but it closed off the most systemic weaknesses.
Walk: Once those critical fixes were in place, the team re-baselined. They ran scheduled NodeZero pentests to confirm the “front door” was locked and defenses held against a broad, external-style attack. Findings came with clear Fix Actions and 1-Click Verify, making remediation “super easy” and allowing the team to close the loop in hours instead of weeks.
Run: With a baseline established, attention shifted to worst-case scenarios. Multiple NodeZero hosts were deployed across segmented environments like Finance, HR, and Operations to model what an attacker could do if they started inside. Instead of proving single fixes, the team validated whether micro-segmentation actually stopped lateral movement — proving resilience across business-critical domains.
Within 24 hours the casino remediated its highest-risk issues and moved to weekly testing cycles, reducing exposures and building the muscle to validate future changes at the speed of business.

Rethinking Vulnerability Scanners
After using Horizon, I don’t know why I would use a vulnerability scanner to be really honest. I just don’t see a lot of value in a vulnerability scanner if it’s showing you vulnerabilities that can’t be used.”
Manager, Information Security
For the casino, this wasn’t just about tool efficacy — it was about reclaiming focus. Instead of wasting cycles chasing theoretical issues, they redirected effort toward the weaknesses that posed real business risk. That shift turned security spend into measurable ROI, with every fix tied directly to closing an attack path that NodeZero had already proven an adversary could exploit.
Conclusion
Even mature, well-funded organizations can be blindsided by simple, systemic weaknesses that add up to catastrophic risk. In this case, the first NodeZero pentest was so impactful it forced automated containment, paused operations, and redefined priorities.
What could have been seen as a setback became a catalyst. The casino embraced a pragmatic, proof-driven strategy: fix what attackers can actually exploit, validate it, and then move on to advanced control validation like micro-segmentation.
Many of the recent casino breaches leaned heavily on credential theft and privilege escalation rather than exotic CVEs. The same techniques — credential dumping, NTLM/SMB abuse, and password reuse — were uncovered here. By patching and hardening around those specific weaknesses, the casino meaningfully reduced its exposure to the very tactics adversaries have used in the wild.
Pentest Wednesday reframed their security program. What began with a single “massive disaster” now drives continuous improvement, measurable risk reduction, and executive confidence that defenses are not just assumed, but proven.
Ready to Prove It?
In casinos, the smallest weakness can have outsized consequences — a single flaw can ripple across financial systems, guest data, and regulatory standing. Security cannot be left to chance.
Pentest Wednesday gives casinos proof that defenses hold up, evidence to drive priorities, and confidence that the odds are stacked in their favor.
Each week, I’ll be sharing new stories from the field — real-world examples of how organizations are using Pentest Wednesday to turn assumptions into evidence, and uncertainty into confidence.
如有侵权请联系:admin#unsafe.sh