
VoidProxy 是一个针对 Microsoft 365 和 Google 账户(包括 Okta 等 SSO 服务)的网络钓鱼即服务 (PhaaS) 平台,利用中间人技术实时窃取凭证、MFA 代码和会话 cookie。研究人员发现其具备高隐蔽性和复杂性。攻击始于被入侵邮件账户发送的钓鱼邮件,链接跳转至伪装网站,并利用 Cloudflare 隐藏 IP 和验证码过滤机器人。会话 cookie 被复制供攻击者使用。建议采用抗钓鱼认证和限制敏感应用访问等措施以增强防护。 2025-9-14 20:45:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:37 收藏

A newly discovered phishing-as-a-service (PhaaS) platform, named VoidProxy, targets Microsoft 365 and Google accounts, including those protected by third-party single sign-on (SSO) providers such as Okta.
The platform uses adversary-in-the-middle (AitM) tactics to steal credentials, multi-factor authentication (MFA) codes, and session cookies in real time.
VoidProxy was discovered by Okta Threat Intelligence researchers, who describe it as scalable, evasive, and sophisticated.
The attack begins with emails from a compromised accounts at email service providers, like Constant Contact, Active Campaign, and NotifyVisitors, whicch include shortened links that send recipients to phishing sites after a multiple redirections.
The malicious sites are hosted on disposable low-cost domains on .icu, .sbs, .cfd, .xyz, .top, and .home, which are protected by Cloudflare to hide their real IPs.
Visitors are first served a Cloudflare CAPTCHA challenge to filter out bots and increase the sense of legitimacy, while a Cloudflare Worker environment is used to filter traffic and load pages.
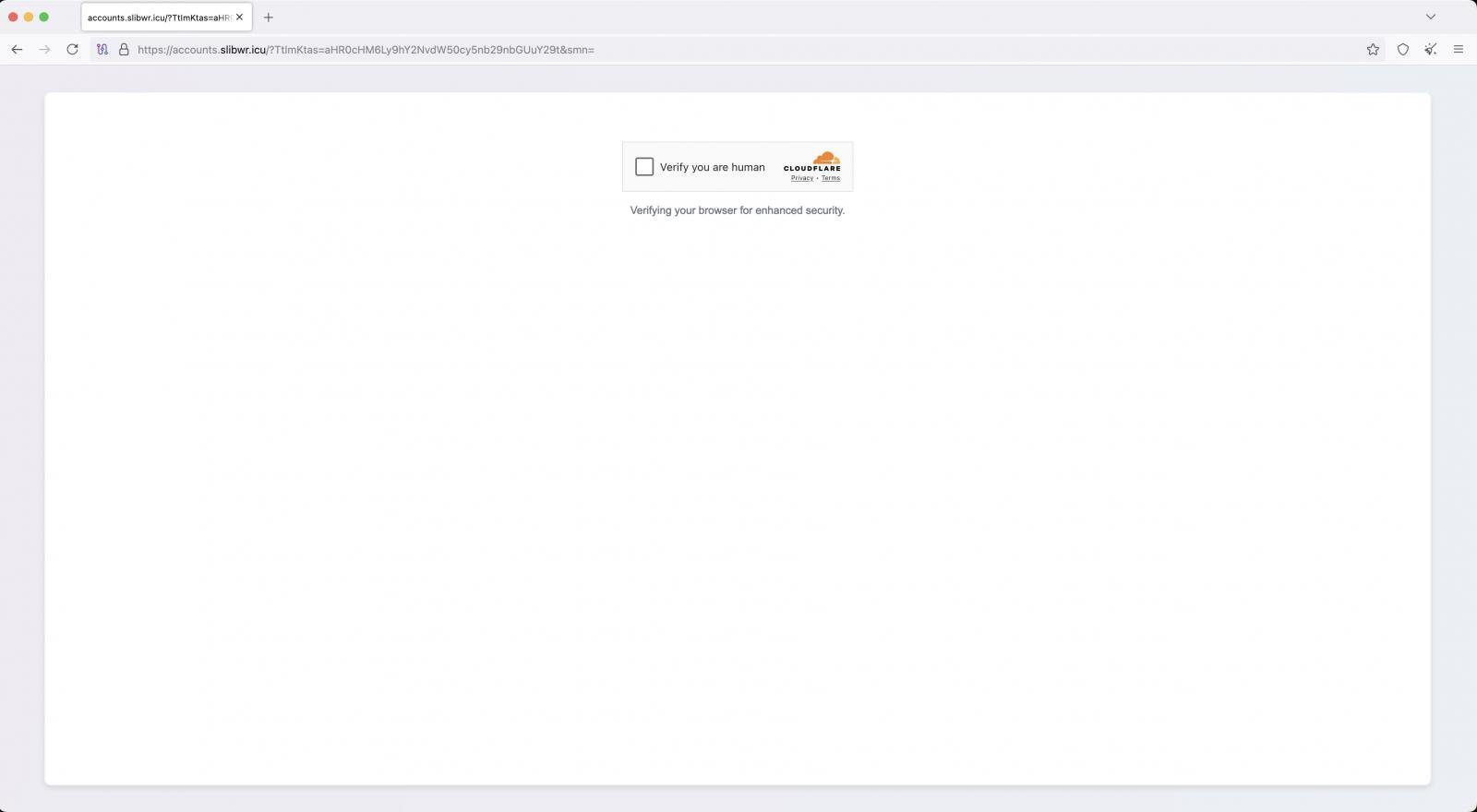
Source: Okta
Selected targets revceive a page that mimics a Microsoft or Google login, while the rest are funneled to a generic and “Welcome” page that presents no threat.
If credentials are typed into the phishing form, requests are proxied through VoidProxy’s adversary-in-the-middle (AitM) to Google or Microsoft servers.
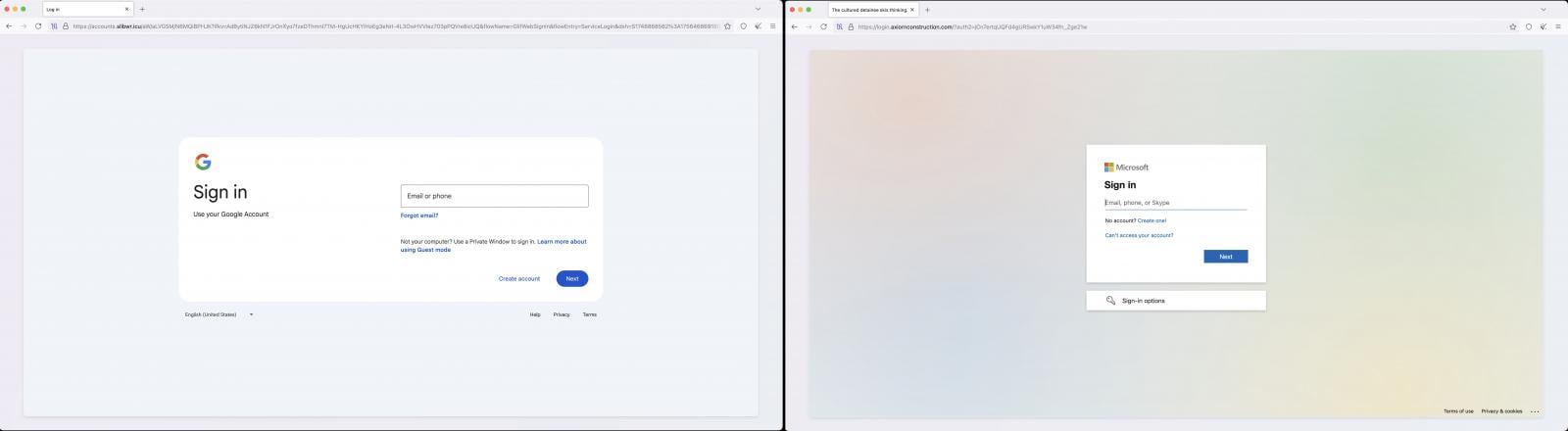
Source: Okta
Federated accounts like those using Okta for SSO are redirected to a second-stage phishing page impersonating Microsoft 365 or Google SSO flows with Okta. These requests were proxied to Okta servers.
The service’s proxy server relays traffic between the victim and the legitimate service while capturing usernames, passwords, and MFA codes in transit.
When the legitimate service issues a session cookie, VoidProxy intercepts it and creates a copy that is made available to the attackers right on the platform’s admin panel.
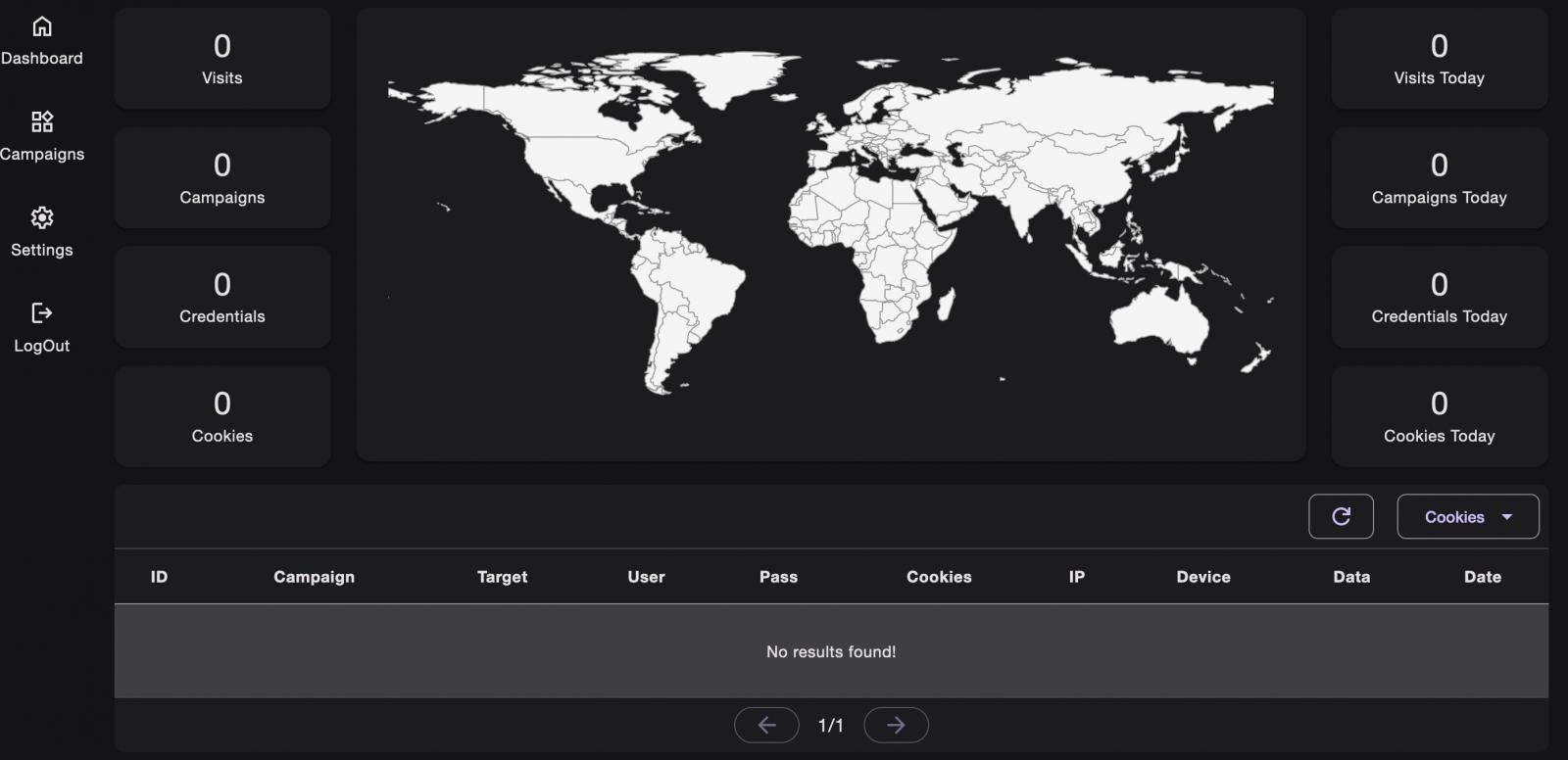
Source: Okta
Okta noted that users who had enrolled in phishing-resistant authentications like Okta FastPass were protected from VoidProxy’s attack flow and received warnings about their account being under attack.
The researchers recommendations include restricting access of sensitive apps only to managed devices, enforcing risk-based access controls, using IP session binding for administrative apps, and forcing re-authentication for admins attempting sensitive actions.
如有侵权请联系:admin#unsafe.sh
