文章指出CISA频繁发布已知漏洞(KEV)警告,但攻击者还滥用身份控制、弱凭证和配置错误。NodeZero的威胁行为者情报功能将验证的攻击路径与真实对手战术关联,帮助组织识别风险并优先处理关键问题。 2025-9-12 13:0:0 Author: horizon3.ai(查看原文) 阅读量:52 收藏
Nearly every week, CISA issues new KEV advisories — warning that attackers are actively exploiting known vulnerabilities that should’ve been patched months ago. From VMware zero-days to lateral movement in cloud environments, the threats are public, well-documented, and preventable.
But KEVs are only part of the picture. Attackers routinely abuse identity-based controls, weak credentials, and security misconfigurations, which are techniques that do not show up in KEV lists, but are just as dangerous.
And yet, organizations still struggle to answer the critical question: would those attacker TTPs actually work in our environment? Too often, they’re not connecting the dots between threat actors, weaknesses, technical impacts, and the business risk that follows.
That’s where Threat Actor Intelligence comes in.
Introducing Threat Actor Intelligence
Threat Actor Intelligence is a capability inside the NodeZero® Offensive Security Platform that correlates validated attack paths in your environment with the tactics used by real adversaries, including APT groups, ransomware affiliates, and state-sponsored actors.
This is more than generic cyber threat intelligence. It’s adversary-aligned risk intelligence that connects known weaknesses with the real attackers exploiting them today.
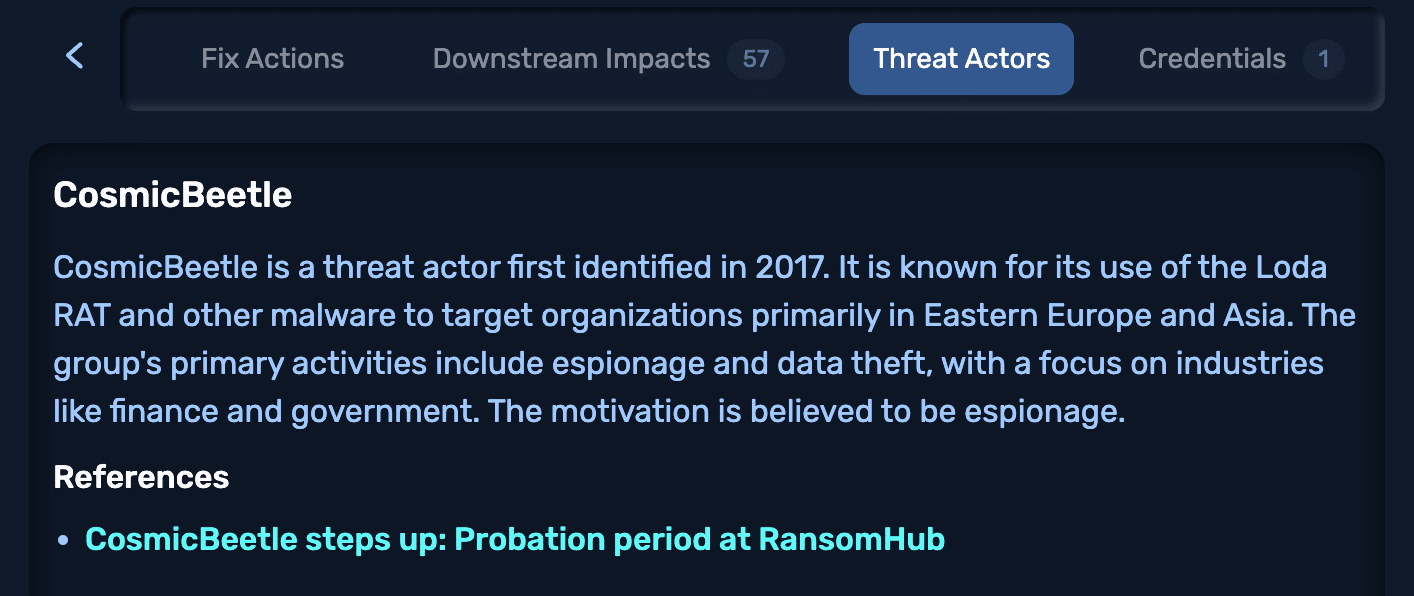
- If NodeZero discovers a path that mimics Scattered Spider’s Snowflake compromise or LockBit’s ESXi lateral movement, Threat Actor Intelligence flags it.
- If NodeZero escalates domain privileges using Cozy Bear’s tradecraft, or detects APT29 and FIN7 techniques in use, you’ll see it mapped automatically, with no tuning required.
- When NodeZero discovers an exploitable CISA KEV in your environment that aligns with an active attacker technique, or identifies a weakness tied to an identity-based TTP, it surfaces directly in the NodeZero interface.
This isn’t intel for the sake of awareness. It’s threat actor profiling and tracking tied directly to your exploitable attack surface.
You’re Not a Target: You’re an Opportunity
Many organizations still believe: “Why would anyone attack us? We don’t have anything they want.” That mindset isn’t just outdated — it’s dangerous. Attackers don’t care about the value of your data. They only care if they can reach it.
A misconfigured identity, a forgotten credential, a vulnerable ESXi host or VPN appliance, or an endpoint where EDR fails to detect malicious activity — any one of these can be enough. You don’t have to be a target to be a victim. You just have to be exploitable.
CISA’s Job Is to Warn. Your Job Is to Verify.
CISA and its global partners have done a remarkable job issuing KEV advisories and urgent threat actor guidance. But the hard truth is this:
Awareness doesn’t equal defense.
- CISA flagged critical VMware zero-days in March 2025 — and they’re still being exploited today.
- Interlock ransomware actors are compromising identity systems and backups across multiple sectors.
- Scattered Spider, LockBit, and Lazarus continue to chain well-known vulnerabilities into full domain compromise.
- And geopolitical threat actors are quietly pre-positioning in critical infrastructure, waiting for the right moment.
Threat Actor Intelligence helps you go beyond the headline:
“Are these attackers using techniques that would actually work in our environment?”
Visualizing Risk from Adversary to Boardroom
Threat Actor Intelligence doesn’t just flag attacker techniques. It connects them to real weaknesses, technical impact, and business consequences in your environments.
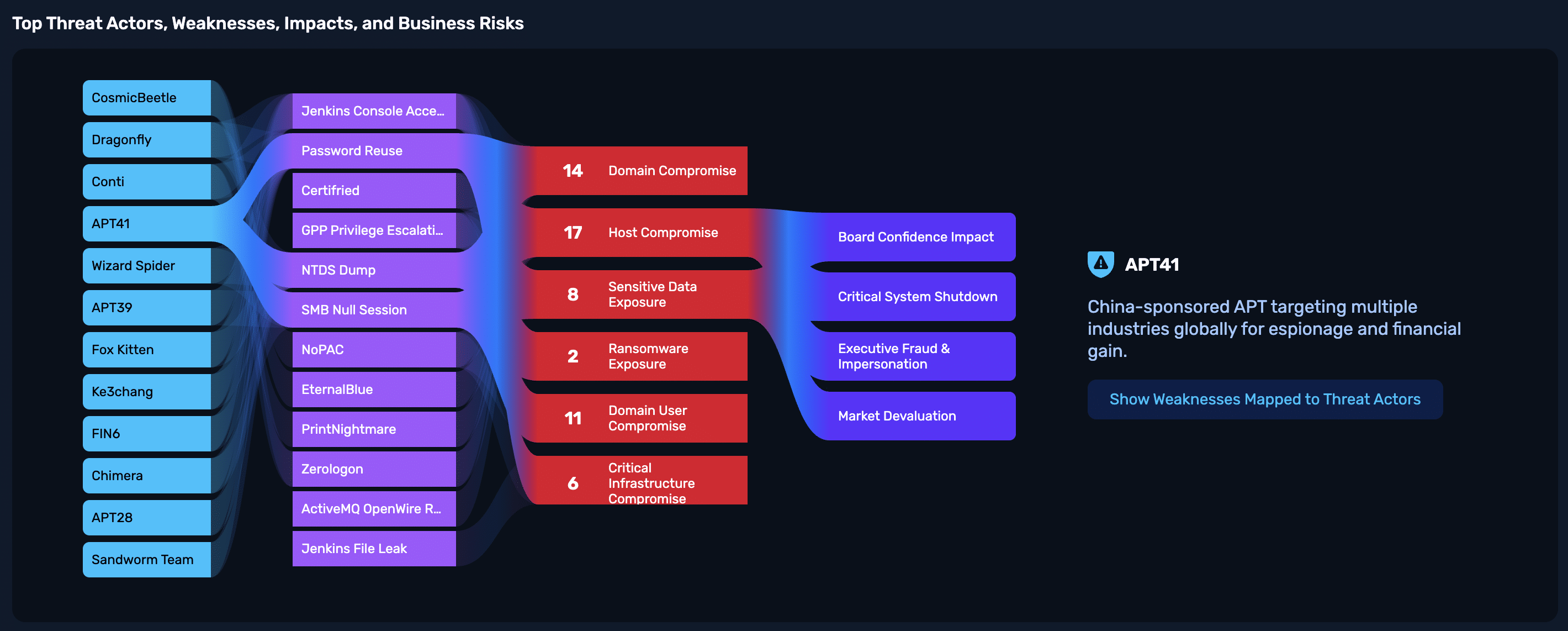
Take the example below. This NodeZero Sankey diagram traces the path from known threat actors like Salt Typhoon and FIN7, through the validated weaknesses they exploit, to the business impact weaknesses cause, all the way to business risks like financial fraud, operational disruption, and data breach exposure they represent.
This is how we turn noisy cyber threat intelligence into something every stakeholder understands:
- SOC teams see the TTPs that were executed.
- IT teams know what to fix and why.
- Executives understand the business impact.
- Auditors see a clear, validated chain from threat to resolution.
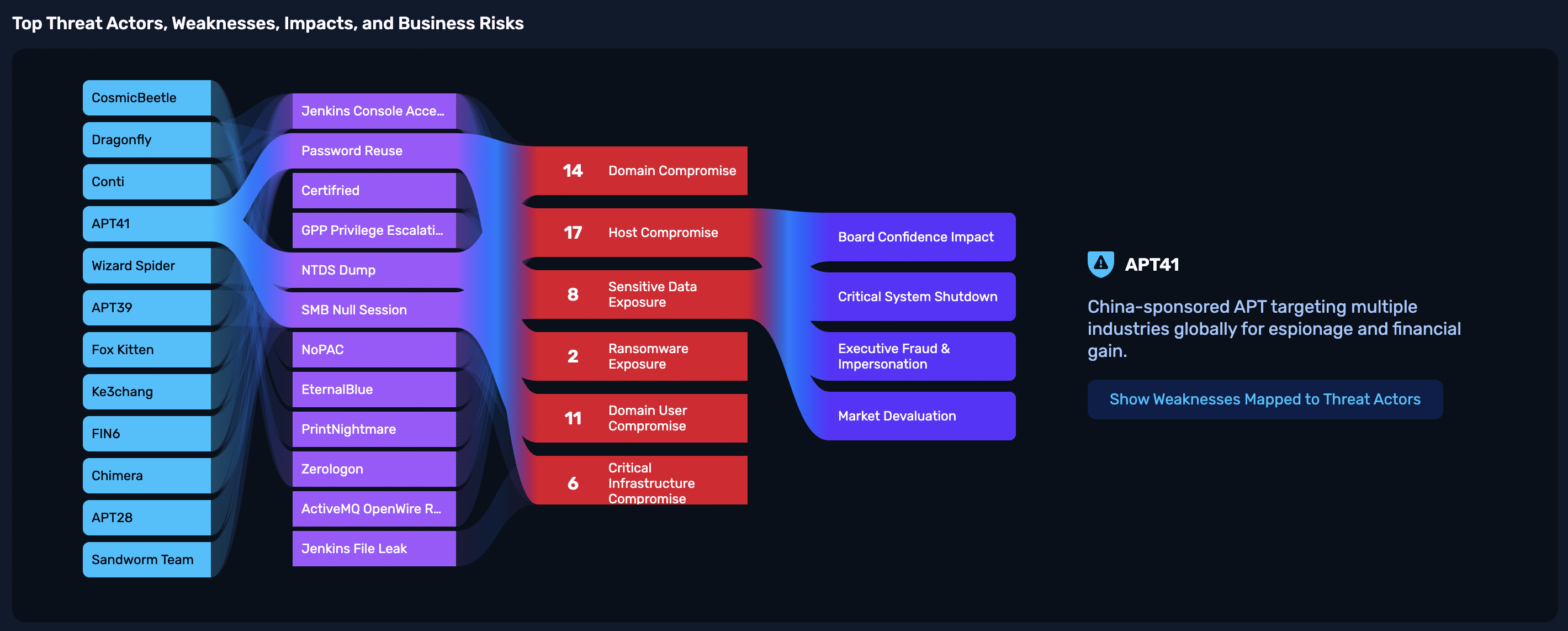
With Threat Actor Intelligence in NodeZero, it’s possible to prioritize not just what’s exploitable, but what actually matters.
Turning Intel into Impact
Threat Actor Intelligence correlates what NodeZero validates in your environment to who’s using those techniques in the wild. This includes:
- Mapped to Horizon3.ai weaknesses like credential reuse
- Known exploited CVEs
- Attribution to actors like Salt Typhoon (APT41), FIN7, Carbanak, AKIRA, RTM, Thrip, and others
- Campaign context pulled from open sources and curated threat intelligence
- GenAI-powered summaries for executive and audit consumption
Embedded Where You Need It. No Tuning Required.
Threat Actor Intelligence is automatically activated during NodeZero operations. You’ll see it:
- In attack graphs, highlighting actor-aligned chains.
- In Weakness Details, mapping CVEs and tactics to known actors.
- In Pentest Summaries, showing campaign-level mapping with real-world context.
- In Audit Logs, offering a full record of who could have done what, and what was done to stop it.
Why This Changes the Game
Traditional vulnerability management tools prioritize findings by CVSS scores, but Threat Actor Intelligence shifts the focus to adversary pressure and validated exploitability. In practice, that changes how every team works. For CISOs, it means being able to say, “This isn’t just a severe vulnerability. It’s a tactic actively used by ransomware groups, and we proved it works here.”
For SOCs, it delivers mapped TTPs that expose missed detections or EDR gaps. For vulnerability teams, it redirects effort away from what’s possibly vulnerable, toward what’s most likely to be exploited. And for auditors and regulators, it provides proof of alignment to threat frameworks, attacker TTPs, and successful mitigation.
No extra feeds. No manual correlation. No tuning. Just actionable adversary-aligned risk intelligence baked into every assessment.
You Don’t Need More Alerts. You Need Proof.
Threat Actor Intelligence delivers proof that real adversary behavior is viable in your network and shows you exactly what to fix first. This is how organizations move beyond reactive triage and toward true real-world readiness.
Threat Actor Intelligence is how you shift from reactive triage to real-world readiness.
如有侵权请联系:admin#unsafe.sh