
文章指出组织在快速采用云和AI技术时面临重大安全风险,因身份管理不善和被动策略导致漏洞。建议采取预防性安全措施并整合风险管理以降低风险。 2025-9-10 12:50:0 Author: www.tenable.com(查看原文) 阅读量:9 收藏
September 10, 2025
5 Min Read

This survey, commissioned by Tenable and developed in collaboration with the Cloud Security Alliance, warns that rapid cloud and AI adoption, combined with insecure identities and a reactive posture, leave organizations exposed. The report urges a strategic shift to preventive security with a unified view of risk and mature identity governance.
Key takeaways
- Organizations are quickly adopting cloud and AI technologies without adequate security, creating significant exposure to preventable breaches.
- Identity now drives most breaches, yet many organizations rely on basic controls, overlooking deeper governance gaps.
- A strategic shift from a reactive, incident-based security posture to a proactive, unified and preventive approach is necessary to manage cloud and AI risks effectively.
Bad news first: While eagerly embracing cloud and AI, many organizations lack proper cybersecurity guardrails, creating a dangerous gap.
The good news? These organizations can tame AI and cloud threats by shifting toward preventive security and gaining a clear, integrated visibility across their environment.
That’s the main takeaway from the new research report “The State of Cloud and AI Security 2025,” commissioned by Tenable and developed in collaboration with the Cloud Security Alliance.
Let's break down the report’s main findings and what you can do about it.
The modern attack surface is wide and fragmented
Here’s security teams’ new reality: They must protect a sprawling, complicated environment that’s partly on premises and partly across multiple cloud providers, with new AI tools sprouting up all over the place.
The report, based on a survey of 1,025 IT and security professionals worldwide, found that:
- 82% work in hybrid environments
- 63% juggle two or more cloud providers
- 55% already use AI, while another 34% are testing it
In short, organizations are going gaga over all things cloud and AI – but in many cases their cloud security plans fall short at protecting this extended and splintered attack surface.
Let’s look at some of the key obstacles.
Weak identity and access management
Many organizations use rudimentary identity and access management (IAM) protection methods. This is a problem, because identities make up the security perimeter in these borderless, heterogeneous environments.
For a whopping 59% of respondents, insecure identities and risky permissions ranked as their biggest security risk. They listed three identity-related issues among the top four causes for their cloud breaches:
- Excessive permissions, such as overprivileged accounts or roles (31%)
- Inconsistent access controls across cloud environments (27%)
- Weak identity hygiene, such as lack of multi-factor authentication (27%)
In addition, when asked about their top cloud security challenges, they said their cloud and IAM teams aren’t on the same page (28%); and they’re struggling to enforce least privilege access (21%).
Another problem: Organizations’ methods for monitoring identity risk are basic, with few tracking metrics for issues such as privilege misuse and access anomalies.
“The data paints a picture of identity as both a well-recognized threat and a still-maturing discipline in secure management,” the report reads.
To enhance IAM security, the report’s recommendations include:
- Restructuring IAM programs and systems
- Improving coordination between cloud and IAM teams
- Shifting to more dynamic indicators of identity risk and resilience
Look Ma, no hands! Racing ahead with AI without sufficient security controls
With 89% of organizations either using AI (55%) or piloting it (34%), cybersecurity teams are scrambling to secure these systems: Already, 34% have suffered an AI-related breach.
“Organizations are moving fast to deploy AI, but their understanding of where the risks lie – and how to mitigate them – still appears immature,” the report reads.
For starters, security teams are worrying about the wrong things. They’re focused on emerging threats like AI model manipulation. But their attention should be on cyber’s usual suspects: unpatched software, insider threats, misconfigured settings and weak credential authentication.
“This misalignment suggests that many security programs are still treating AI as fundamentally novel, rather than applying proven cloud and identity security principles to these new systems,” the report reads.
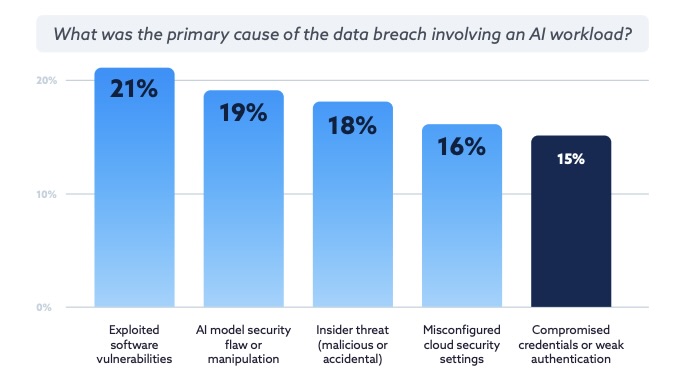
(Source: "State of Cloud and AI Security 2025" report, commissioned by Tenable and developed in collaboration with the Cloud Security Alliance)
Other weak spots: Reactive security, skills gap
The report goes on to unpack other cloud and AI security obstacles, including:
- The skills gap: About one-third of respondents cited lack of expertise as their top challenge, which leads to fuzzy strategies; insufficient budgets; and misunderstanding of cloud risks by executive leaders.
- A reactive security posture: Respondents’ most commonly tracked key performance indicator (KPI) is the frequency and severity of security incidents (43%). This signals a rearview-mirror approach that prioritizes crisis response over proactive risk reduction – a misguided strategy because most cloud and AI breaches are preventable.
How do we fix this?
The report offers a wake-up call for teams tasked with cloud and AI security, pressing for a strategic shift away from fragmented tools, immature identity practices and a reactive mindset.
Already, some respondents are taking steps in the right direction by, for example, adopting exposure management (58%) for unified security monitoring and risk prioritization; and cloud security posture management (57%).
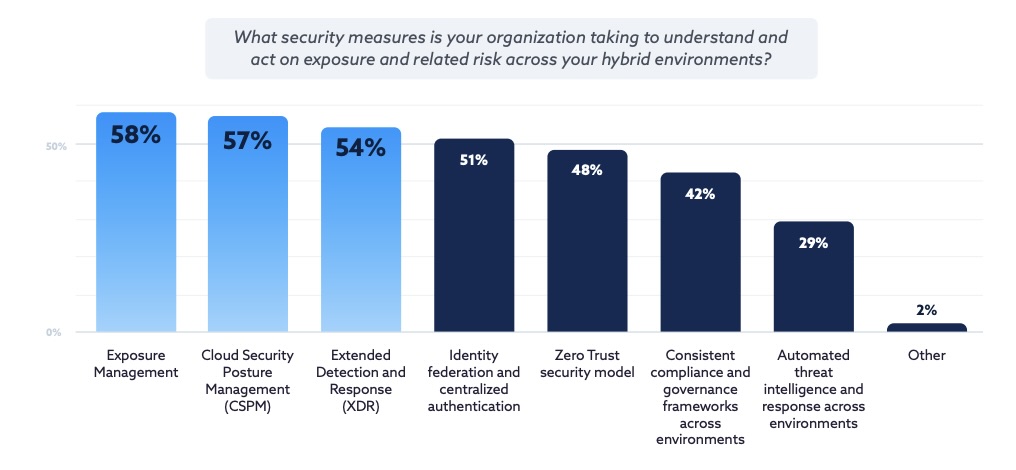
(Source: "State of Cloud and AI Security 2025" report, commissioned by Tenable and developed in collaboration with the Cloud Security Alliance)
The report’s recommendations include:
- Get a single view of everything: Integrated visibility and controls are foundational for managing complexity across on-prem, cloud and AI workloads.
- Beef up your identity security: Enhance identity governance for all human and non-human identities that need access.
- Focus on prevention, not just reaction: Moving from reactive to proactive security is key to staying ahead of evolving threats.
“Security maturity depends on strategic alignment and risk-driven planning. Organizations that move beyond point solutions and reactive operations will be better equipped to secure evolving cloud and AI environments,” the report reads.
To get all the AI and cloud security insights, download the "State of Cloud and AI Security 2025" report today!

Thomas Nuth
Head of Product Marketing - Cloud, Tenable
Thomas Nuth is a seasoned cybersecurity executive with over 15 years of experience driving global go-to-market strategy, brand development, and market adoption for some of the world’s most innovative security companies. With a deep understanding of the evolving threat landscape—from cloud-native risk to AI-powered attacks—Thomas has played a pivotal role in shaping industry narratives and positioning next-gen technologies at the forefront of the cybersecurity conversation. Before joining Tenable, Thomas held positions at Wiz, Qualys, Fortinet, Forescout, and other innovative leaders in cybersecurity.
- Cloud
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh