SaaS供应链攻击通过OAuth令牌和集成漏洞进行,如UNC6395和UNC6040案例所示。传统安全工具难以检测这些跨平台攻击。建议企业发现攻击面、管理权限并分析行为以防御。 2025-9-9 20:40:3 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Your business risk isn’t limited to the apps you buy, but also the integrations you trust.
Data theft via exploitation of SaaS apps is becoming more widespread. Recent attacks by UNC6395 (which abused the Drift integration with Salesforce) and UNC6040 (which leveraged a rogue Salesforce Data Loader app) highlight a dangerous new reality: Attackers are no longer just targeting your users or your network. They are exploiting the trusted connections between your SaaS applications (your SaaS supply chain) to steal data, and most security tools can’t see it happening.
These incidents are not isolated misconfigurations. They are an exploitation of the SaaS to SaaS connections. Attackers are abusing the web of trust between platforms like Salesforce, Microsoft 365, and Google Workspace to infiltrate systems and breach sensitive data. And it’s not just connections from Salesforce to other applications; these integrations include connections to other tenants. An organization may have hundreds or even thousands of Microsoft or Salesforce tenants that all need to be managed and maintained with different connections for different purposes.
As organizations rely on a growing number of SaaS applications, each integration becomes part of the attack surface. The complexity is staggering, and most security stacks today aren’t equipped to monitor or defend against this type of threat.
Case study 1: UNC6395 and the Salesforce Drift attack
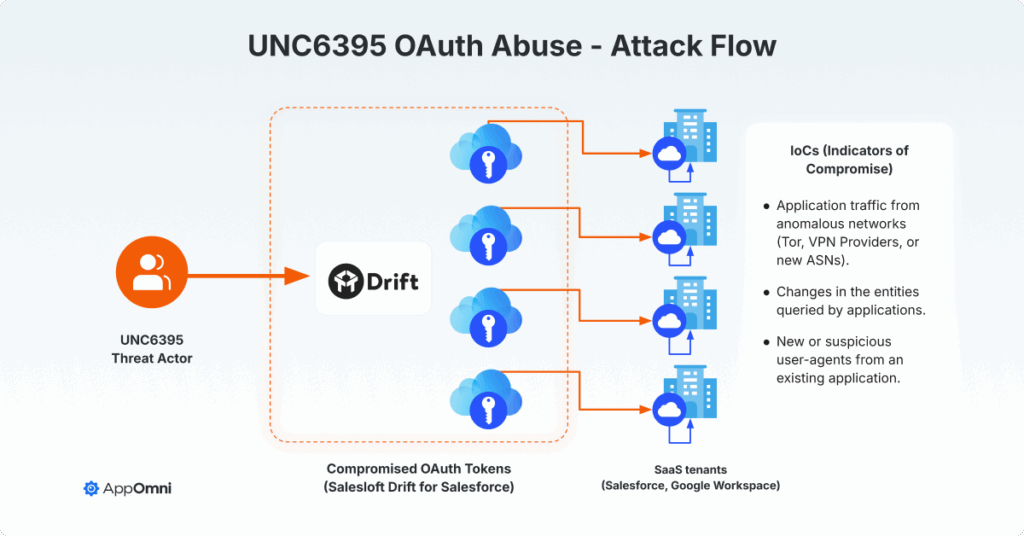
UNC6395 carried out an attack, which impacted over 700 organizations, including Zscaler and Palo Alto Networks. It was shockingly simple and effective. The attackers didn’t use malware, and they didn’t phish any users.
Instead, they targeted the trusted connections between apps. By compromising the Drift integration for Salesforce, they gained a foothold into organizations’ sensitive data. And it did not stop there. As investigations continue, integrations from Drift to Google and other SaaS applications were compromised.
Here’s a breakdown of their method:
- Initial access: They compromised OAuth tokens from connected applications like Drift and Drift email, compromising the Salesloft SaaS provider, not user credentials.
- Defense evasion: By using authorized app sessions, their activity appeared as legitimate API traffic, allowing them to bypass MFA and traditional security alerts.
- Lateral movement: A foothold in one app quickly became a superhighway. They pivoted from the initial breach into connected SaaS tenants and platforms like Google Workspace and Slack.
- Exfiltration: Once inside, they moved fast, stealing credentials and API keys.
This was an oversight of permissions and OAuth governance. The attack proves that SaaS breaches rarely stay confined to one app and that attackers will exploit trusted interconnections to expand their compromise.
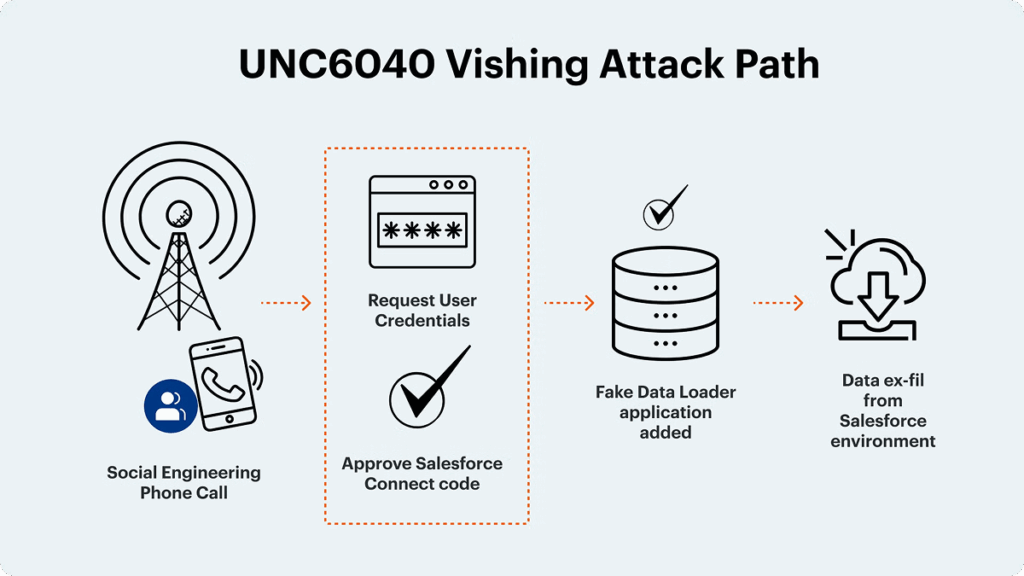
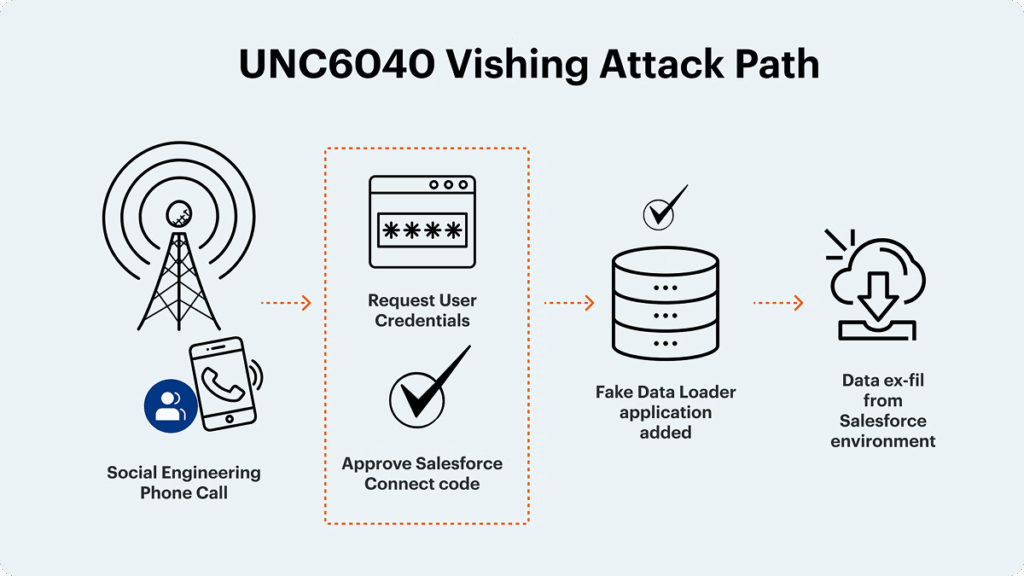
Case study 2: UNC6040 / ShinyHunters and the rogue Data Loader attack
The attack group UNC6040 (possibly ShinyHunters) took a different but equally effective approach. Rather than compromising a legitimate integration, they used social engineering to introduce a fraudulent one.
They created a malicious app that perfectly mimicked the legitimate Salesforce Data Loader, a common business tool. By disguising their app, they tricked users and administrators into granting it broad OAuth permissions, which gave the attackers sweeping access to sensitive Salesforce data.
Both trusted and rogue apps can be entry points for attackers. It’s not enough to know who connects an app, you must scrutinize what permissions these apps are requesting and why. In this case, attackers took advantage of the API access controls.
The real risk: Your interconnected SaaS ecosystem
These attacks succeed by exploiting the hidden risks in how modern applications connect and share data, primarily through OAuth. And attackers are now targeting:
- Token leakage: OAuth tokens can be stolen or leaked, giving attackers direct access without needing a password.
- Overbroad scopes or exposed secrets: Many applications request far more permissions than necessary, and often rely on secrets that, if leaked or stolen, can be abused by attackers for unauthorized access.
- Forgotten access: Revoking access for old apps is often a manual, error-prone process, leaving old doors open for attackers.
This highlights a fundamental vulnerability in how many organizations manage authentication. For a deeper dive, you can read more about OAuth token vulnerabilities.
Traditional security tools were not built to manage the complexity of a sprawling, interconnected SaaS environment. They often fail because:
- There’s no visibility: Most security stacks cannot discover all the third-party apps and integrations connected to core platforms like Salesforce or Microsoft 365.
- They’re blind to risky permissions: Traditional tools don’t monitor for configuration drift or apps that have been granted excessive permissions, leaving massive security gaps.
- Logs are not analyzed or collected: Many security teams do not collect SaaS logs. Each SaaS platform has a different logging format, making it nearly impossible to trace an attack that moves from one app to another without a solution that can normalize the data.
A modern defense strategy for the SaaS supply chain
To defend against campaigns like UNC6395 and UNC6040, enterprises need a security strategy built for the SaaS-to-SaaS layer.
- Discover your full SaaS attack surface: You can’t protect what you can’t see. Start by creating a complete inventory of all apps (sanctioned and unsanctioned) connected to your core SaaS environments. And further restrict users’ ability to grant OAuth permissions to applications, reducing risk of sprawl.
- Continuously govern app permissions: Don’t “set and forget” integrations. Regularly review the OAuth scopes and permissions granted to third-party apps. Block or restrict any app that requests unnecessary access to data via IP restrictions and security policies.
- Analyze behavior to detect threats: Centralize and normalize your SaaS activity logs to establish a baseline for normal behavior. This allows you to apply behavioral analytics that can flag suspicious activity, such as an app suddenly moving abnormal volumes of data or a token being used from a strange location.
UNC6395 and UNC6040 are just the beginning
The Salesforce Drift breach and the rogue Data Loader app breach are more than just isolated incidents; they prove that modern SaaS attacks are:
- Expansive: They often begin in one app but can spread across others, like Google Workspace and Slack.
- Complex: Each integration multiplies the attack surface.
- Under-monitored: Traditional tools don’t track SaaS connections, enforce policy, or normalize logs.
As you secure your business, remember that your risk isn’t limited to the apps you buy, but also the integrations you trust.
Secure your SaaS supply chain. Request a complimentary risk assessment to find out how.
The post How New Supply Chain Attacks Challenge SaaS Security: Lessons from UNC6395, UNC6040, and ShinyHunters appeared first on AppOmni.
*** This is a Security Bloggers Network syndicated blog from AppOmni authored by Chad Knipschild, Director of Product Marketing, AppOmni. Read the original post at: https://appomni.com/blog/saas-supply-chain-attacks-unc6395-unc6040/
如有侵权请联系:admin#unsafe.sh
