研究发现大量恶意域名被注册用于2025年FIFA俱乐部世界杯及2026年世界杯的诈骗活动。攻击者提前注册包含品牌关键词的域名,并利用城市名称和赛事关键词吸引目标受众。这些域名涉及假网站、假冒商店及流媒体访问等欺诈行为。 2025-8-28 10:2:7 Author: bfore.ai(查看原文) 阅读量:18 收藏
The 2025 Club World Cup was a sign of what’s to come for the 2026 World Cup
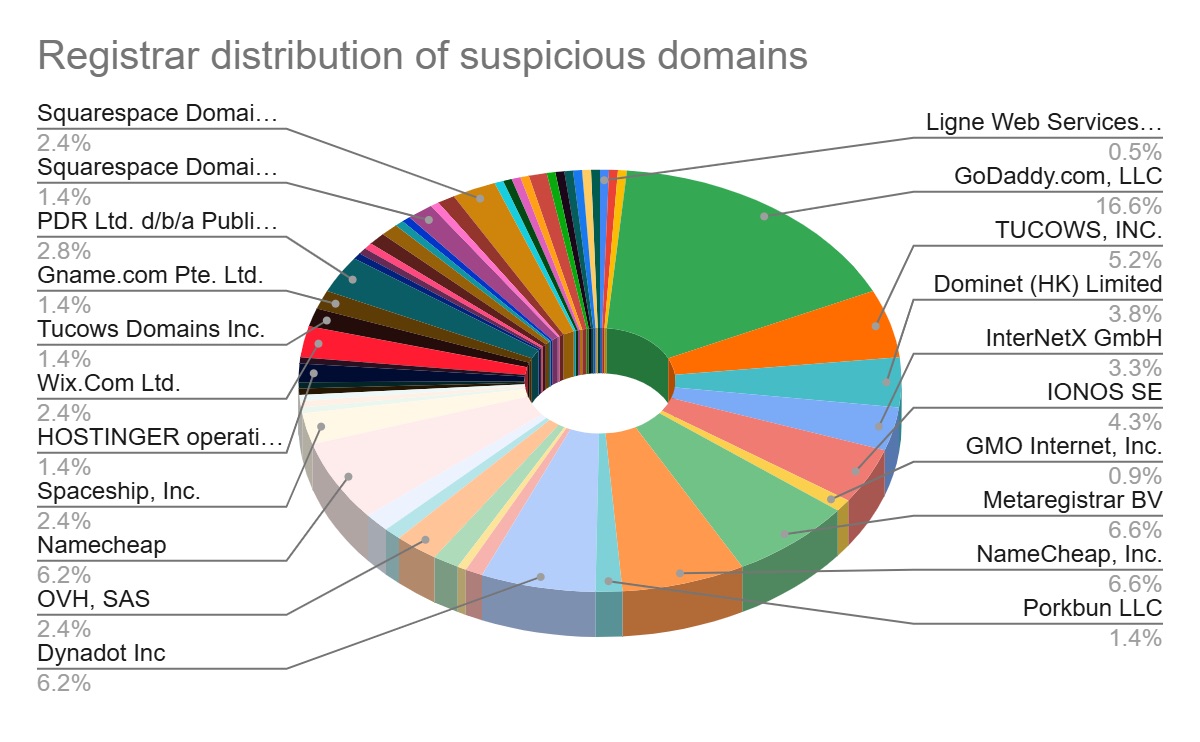
Date: August 2025 In the lead-up to major global events, cybercriminals are quick to launch fraudulent schemes like fake websites and counterfeit online stores. PreCrime Labs, the threat research team at BforeAI, recently found a sizable number of domains created to take advantage of the FIFA Club World Cup 2025 in the U.S. The observations from this event are a harbinger of the malicious domain activity sponsors, businesses, and fans should expect during next year’s 2026 World Cup tournament, also being hosted in the U.S. (as well as Canada and Mexico). During this investigation, the team identified a concerning trend: many domains have already been registered for the FIFA World Cup 2026. This highlights two key tactics used by attackers: they either repurpose old domains for new campaigns or register new ones well in advance. By “aging” these domains for a year or more, attackers can better avoid detection and improve their success rates as the event nears. We even discovered domains registered for the FIFA tournaments in 2030 and 2034. We analyzed a set of 498 domains that contain FIFA, football (soccer), and World Cup-related brand terms (e.g., “worldcup”, “fifa”, “football”). These domains span a mix of obvious trademark typosquats, speculative registrations, generic fan/merchandise/betting names, and community or amateur-football sites. Disclaimer: This set exhibits multiple red-flag clusters commonly used in scams and phishing around major sporting events, particularly in anticipation of attention peaks regarding the FIFA Club World Cup 2025 and the FIFA World Cup 2026. Top registrars: GoDaddy[.]com, LLC, Namecheap, Inc., Gname[.]com Pte. Ltd., Dynadot Inc, and Wix. Among the domains, [.]com accounted for 300 (58.9%), followed by .online with 36 (7.1%), .football with 24 (4.7%), .org with 14 (2.8%), .xyz and .shop with 13 each (2.6%), while the remainder were spread across other TLDs such as .net, .info, .mobi, .store, .vip, .site, and .app.
Approximately 299 domains were registered from 8 August 2025 to 12 August 2025. Why this matters: Major tournaments (2025 Club World Cup; 2026 Men’s World Cup) predictably trigger spikes in fraud infrastructure: fake ticketing, counterfeit merchandise, unlawful streaming, betting lures, and generic “fan guide” pages used as lead-gen or phishing launchpads.
“FIFA” appears in 173 domains; “worldcup” in 129, indicating a strong signal of brand-adjacent intent, ranging from fan commentary to possible abuse. Multiple year-anchored names (e.g., fifawcdallas[.]com, fifa2026atl[.]com, kansascityunitycup2026[.]com, getworldcup2026tickets[.]com) reflect geo-targeting and timing around matches, host cities, or fan events.
Names such as fifaworldcupmerch2026[.]com, fifastore[.]shop, ultrasfootball[.]shop, retrofootballjerseys[.]shop, theworldcup2026[.]store are consistent with counterfeit goods or non-licensed sales patterns. Some may be legitimate sellers; however, the combination of brand terms and generic commerce TLDs is a known fraud vector. Approximately 55 domains include “live” or similar (e.g., watchfootball-live[.]com, fifalive-… , fifa-live-… , footballtv[.]online). Free or “official” live-stream claims are high-risk for malware, credential theft, or subscription scams.
Around 32 names include bet/slot/casino (fifazbet. variants, football88[.]bet, vtkbet[.]football, etc.). Sports betting is often used as monetization or traffic-capture in the event window, jurisdictional compliance is frequently unclear, and phishing overlays are common.
A small subset references “login” / “register” (e.g., fifaworldcup-login[.]com, fifaworldcup-register[.]com), which is a classic credential-phishing framing when paired with tournament branding.
23 domains reference Dallas / ATL(anta) / Kansas / PHL (Philadelphia) / Texas, matching known U.S. host-city narratives for 2025/2026-period events. Examples: fifawcdallas[.]com, fifa2026atl[.]com, kansascityunitycup2026[.]com, 2026texasworldcup[.]com, worldcup26texas[.]com. A few reference visas/hotels (e.g., worldcupcanadavisa[.]com, fifacuphotels[.]com), which are high-risk categories for payment fraud and data theft.
Typo-like: fifaworldcupstadiucom (missing “m”), fifaclubwccom (missing dot). Such errors are typical of deception or traffic-siphon attempts. Pinyin-style strings around “Club World Cup” (e.g., zh-fifaclub-…, …-shijubei[.]com) appear geared at Chinese-language audiences, often for live-stream/betting lures.
[.]com dominates (58.9%), with a meaningful presence of low-friction TLDs (.online, .xyz, .shop, .store) and theme TLDs (.football). This mix is consistent with cheap, disposable domain tactics. Note: Caveat: Many “football” sites in the list clearly refer to American football. For example, sites related to high school football teams, clubs, or other football-related programs (e.g., simivalleyflagfootball[.]org, gwinnettcountyhsfootball[.]com). These are likely benign and should not be confused with soccer. Example future risk narratives (estimation from similar infrastructures)
In one example (Figure 2), we observed a domain with a page title that says, “FIFA world cup schedule” to lure users searching for official match information, but when they visit the site, they are met with a betting page. This is a common trend observed around mega sporting events (Olympics, World Cup, ICC tournaments), where adversaries abuse trending keywords to maximize search visibility and social media spread. The page content is in Mandarin Chinese, but FIFA and official broadcasters do not use such channels for promotions. Prominent use of celebrity pictures and “official partner” keywords are used to establish legitimacy, which is not verifiable with FIFA’s actual sponsor list. Claims like “巴西圣保罗” (Brazil São Paulo official partner) are used, but in Mandarin, to enhance credibility.
Another domain (Figure 3) disguises itself as a social criticism and activist page around FIFA 2026 volunteering, highlighting the exploitation of unpaid volunteers, economic costs, and equity concerns. Unlike pure scams (fraudulent shops, betting platforms, or fake ticketing sites), this site leverages controversy and critical narratives. This can be used for influence operations, hacktivism campaigns, or reputational hazards aimed at large sporting organizations. The website also focuses on strong emotional framing and call-to-action buttons such as “Support your city (paid!)” that could potentially redirect users to external fundraising platforms or politically motivated campaigns.
Another webpage promotes an “EV Map for World Cup 2026”, claiming to help fans traveling to World Cup matches find hotels and restaurants with electric vehicle (EV) chargers. By highlighting the FIFA 2026 brand context (Figure 4) as a hook to make the offer look legitimate and relevant, this campaign is positioned as a partnership opportunity, encouraging businesses to “apply to be featured”. The campaign had several ways to collect personally identifiable information (PII) through a B2B phishing scheme, like sensitive business information (financial details, owner identity, contact info). Additionally, sites like this may charge a fee to unsuspecting businesses seeking advertising opportunities to be “featured” in a non-existent directory.
Typical scams associated with large sporting events are websites with prominent call-to-action buttons to “Buy Tickets”, a classic high-risk lure for financial fraud. In this case, fake branding elements, especially those of payment partners (VISA), flags, and FIFA logo lookalikes, were strategically added to the domains. This particular Spanish-language domain (Figure 5) aligns with Mexico, one of the 2026 World Cup host countries. The CTA button likely redirects users to payment phishing pages or shadow e-commerce platforms. Users risk not only financial loss but also identity theft if personal data is captured. In our experience, ticket scams historically spike 12–18 months before a FIFA tournament takes place, as interest and demand build. This fits the pattern seen earlier in FIFA 2018 and the 2024 Paris Olympics, with thousands of fake ticket domains appearing prior to the actual event.
A couple domains were observed promoting staking of “FIFA coin” via ETH and providing a static wallet address, a classic sign of a scam ICO. These domains show fake statistics ($18M staked and 421K wallets as mentioned in the image below, Figure 6) to build credibility. One of the websites uses the common “generator scam” format often seen in gaming cheats, free currency, or airdrops. The other domain was hosted on Weebly, offering low-cost setup and throwaway infrastructure for threat actors. These domains are likely designed for phishing wallets and conducting financial fraud.
Some websites indicated recent registration or were in initial staging phases before actual content deployment. One particular domain, “fifaworldcupusa” (Figure 7), is suspected to be strongly tied to FIFA 2026 (USA/Canada/Mexico). This is a clear case of typosquatting, exploiting FIFA’s brand name for potential fraud. Parked domains like this are often later used to actively proliferate phishing, ticket scams, or malware campaigns, or used as redirect infrastructure to scam portals alleging to offer products and services like betting, ticketing, or crypto coins/investments. We expect waves of new registrations as the 2026 World Cup approaches, then further spikes as the event edges closer. Domains with brand + year + city are particularly valuable for SMS (“smishing”) and social DM lures such as “Your Fan ID is incomplete”, “Schedule update”, or “Payment required”. Short-lived infrastructure (cheap TLDs, CDN/proxy hosting) complicates blacklisting unless proactive, or pattern-based controls are deployed. Employ active tracking of various indicators of maliciousness that make the threat obvious. For example, monitoring of long-tail event-specific keywords (e.g., city names + “WorldCup2026”, “FIFAcoin”, “EV map World Cup”), in addition to obvious ones like “FIFA tickets.” Authorized parties and official sponsors of the upcoming FIFA World Cup event can register defensive domains across TLDs known for malicious activities (.xyz, .online, .shop, .football, .vip). Active disruption of various threats such as ICO scams and rug pulls tied to FIFA branding or mentions of “FIFA Coin,” “ticket generator,” or “World Cup token” in Telegram, dark web markets, and Discord groups is highly recommended. Site URLs containing keywords with unusual or extra keyword additions that may be used to establish authenticity (e.g., “fifaworldcupusa.org” or “fifatickets2026.shop”) should be avoided. Unofficial or modified versions of apps that promote streaming, gambling or betting, investments, schedules, or crypto coins should be avoided. Host cities (Dallas, Atlanta, Kansas City, Philadelphia, etc.) should take extra steps to monitor and verify the veracity of local business promotions (like hotels or restaurants) leveraging their names to protect visiting fans from being scammed. This report is based solely on the domains provided. Some domains are likely legitimate (clubs, schools, news blogs, community events) and must not be labeled malicious, as they are examples of staging and/or benign infrastructure related to clustering. However, the timing of their registrations and domain updates occurring around or shortly after the FIFA World Cup 2025 raises suspicion that they may be attempting to exploit FIFA’s brand while it is trending. We are not asserting that phishing SMS tied to these exact domains was delivered; we highlight that SMS is a frequent delivery vector in similar campaigns, and the naming fits common lure patterns.
Author: PreCrime Labs, BforeAI
5. Peak registration phase:
Key research findings and trends
1) Heavy brand and event anchoring
2) Commerce and counterfeit risk (shops/stores/merchandise)
4) Betting and gaming signals
5) Low but notable “account” cues
6) City/host anchoring and travel-adjacent lures
7) Novel typosquat constructions
8) TLD choices reflect opportunistic registration
Ticket scams are common, especially when official allocations sell out.
Often collect payment without delivery or deliver counterfeit items.
Targeted at fans expecting ticketing/lottery portals.Free match streaming platforms

Hate and criticism-oriented websites

Business advertising campaigns

Sale of FIFA World Cup tickets

Cryptocurrency and FIFA Initial Coin Offering (ICO)
Websites recently registered and under construction

Explore our latest PreCrime™ Labs report:
如有侵权请联系:admin#unsafe.sh