CVE‑2025‑25256
Fortinet FortiSIEM存在预身份验证命令注入漏洞,允许未认证用户执行远程代码,可能导致系统完全控制、数据泄露及恶意软件安装。建议升级到最新版本修复。 2025-8-21 22:0:30 Author: horizon3.ai(查看原文) 阅读量:12 收藏
Fortinet FortiSIEM存在预身份验证命令注入漏洞,允许未认证用户执行远程代码,可能导致系统完全控制、数据泄露及恶意软件安装。建议升级到最新版本修复。 2025-8-21 22:0:30 Author: horizon3.ai(查看原文) 阅读量:12 收藏
Fortinet FortiSIEM Pre-Authentication Command Injection Vulnerability
Fortinet FortiSIEM Pre-Authentication Command Injection Vulnerability allows for unauthenticated remote code execution (RCE) attacks.
Exploiting this vulnerability can allow an attacker to gain complete control over the affected system. This includes accessing sensitive data, modifying or deleting system resources, and potentially installing malware or creating backdoors.
Mitigations
- Reference the vendor advisory and upgrade to the latest patched version of the software.
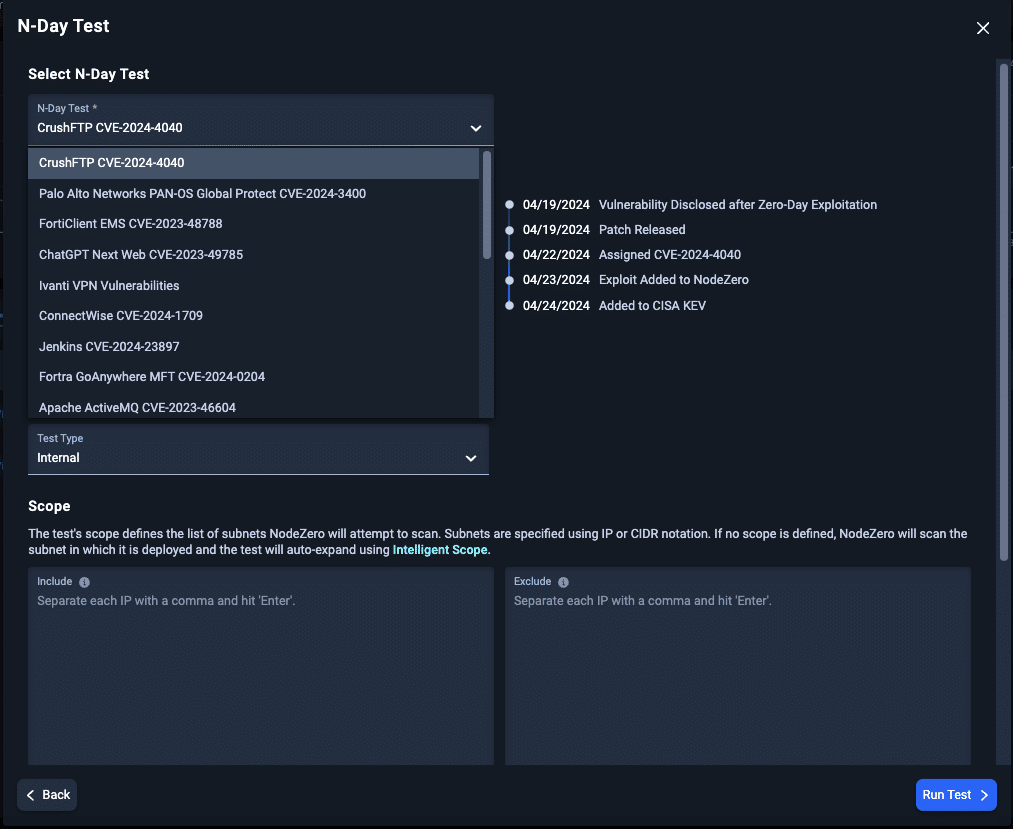
Rapid Response N-Day Testing
References
🔗 Fortinet Warns About FortiSIEM Vulnerability (CVE-2025-25256) With In-the-Wild Exploit Code
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
文章来源: https://horizon3.ai/attack-research/vulnerabilities/cve%e2%80%912025%e2%80%9125256/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
