VMRay Platform 2025.3版本优化了Live Interaction功能,新增剩余时间显示、手动停止等改进;引入计算机视觉AI用于反钓鱼检测;升级Ubuntu系统并增加SSO安全选项;新增Microsoft Sentinel和Defender连接器。 2025-8-1 07:48:47 Author: www.vmray.com(查看原文) 阅读量:32 收藏
Introduction
Since the release of VMRay Platform 2025.2, we’ve had a busy start to the summer. Back then, we introduced SVG file analysis, a feature that continues to gain traction as threat actors increasingly adopt SVG-based phishing delivery techniques. If you’re curious about the evolution of SVG threats and how our Labs team is staying ahead of the curve, check out our monthly detection blog series for deep dives and real-world insights.
But it wasn’t just feature work keeping us busy. In June 2025, we launched a new product: UniqueSignal, a VMRay-powered threat intelligence feed delivering actionable, high-fidelity indicators to supercharge your detection and response workflows. If you haven’t explored it yet, we invite you to learn more, and we hope you’re already enjoying the benefits or will be soon! Now, let’s look at what’s been cooking in the VMRay Platform 2025.3 release.
A better feel for Live Interaction
If you’re a hands-on analyst who values direct, observable threat behavior, you already know the power of Live Interaction. It’s the feature that lets you take the wheel during malware analysis—interact with a live VM, execute manual actions, mimic user behavior, and watch malicious samples react in real time.
Some of our users reached out with valuable suggestions on how to make the experience faster, smoother, and more insightful; and we listened. Based on your feedback, we rolled out a series of improvements designed to make Live Interaction more powerful and intuitive. Here’s what’s new:
1) See remaining analysis time at a glance
No more guesswork. You’ll now see how much time is left in your Live Interaction session directly in the UI. This gives you better control, helping you plan actions without running out of time unexpectedly.
2) Manual stop
Need to end your session early? You can now stop a Live Interaction session manually at any time, freeing up resources instantly and speeding up report generation.
3) Maximum timeout by default
By default, Live Interaction analyses now run with the maximum timeout duration. This gives analysts more breathing room to investigate complex behaviors without watching the clock.
4) Clearer job naming & descriptions
We updated the names and descriptions of Live Interaction jobs for Dynamic and Web Analyses to make them easier to understand. You’ll now see more precise explanations of what’s happening during each stage of the analysis, so it’s easier to follow along in real time.
This is yet another step in making Live Interaction an excellent experience. We began this journey in our last release, when we prioritized Live Interaction jobs over others in the same account queue. In the meantime, jump into a Live Interaction session, try out the new experience yourself, and give us your thoughts on how these changes work for you.
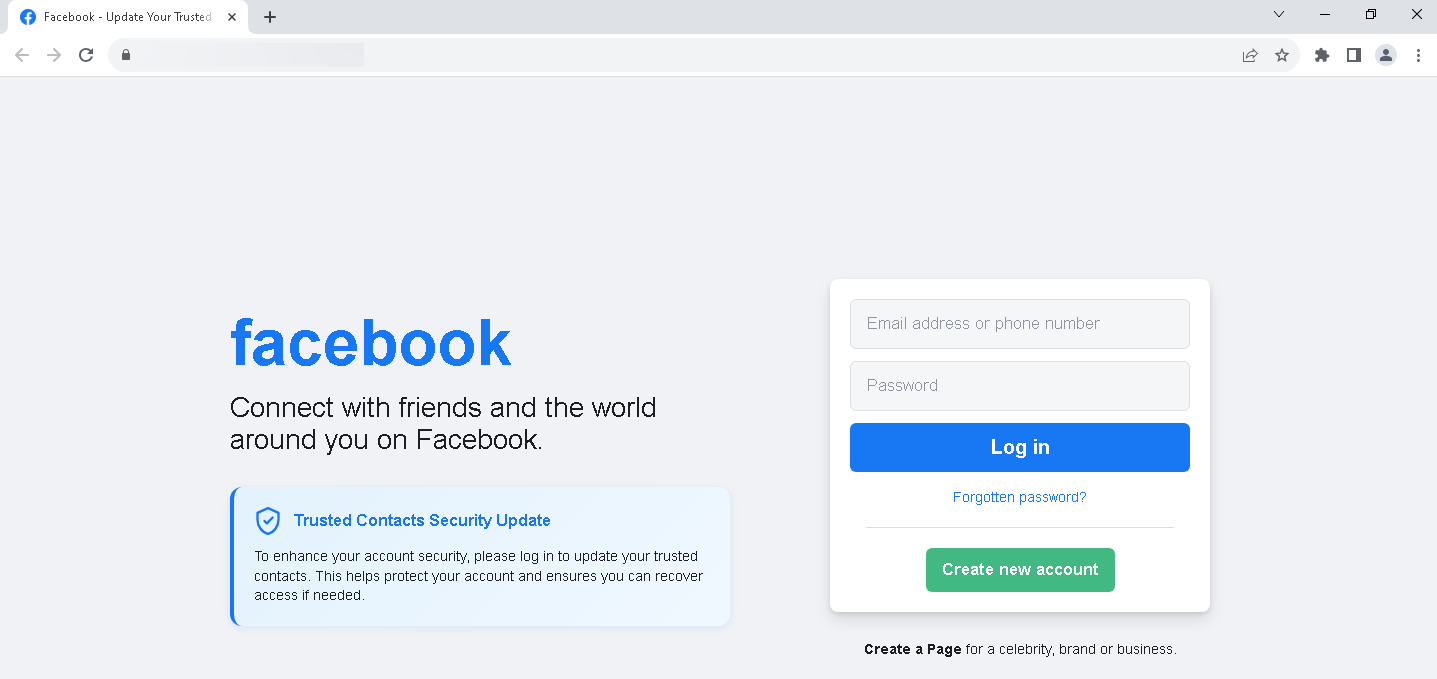
Visual AI approach to phishing detection
With this release, we’re raising the bar in phishing detection by introducing Computer Vision (CV) AI for phishing, a powerful enhancement to our existing threat detection stack for VMRay Cloud users. Here’s a breakdown of what we achieved in recent weeks of the development.
Seeing phishing through a human lens
Phishing is a visual deception. Most phishing sites are designed to fool users, not machines. They mimic familiar brand logins, craft convincing layouts, and visually replicate legitimate pages. That’s why detecting phishing effectively means analyzing it the way a human would—visually.
With VMRay 2025.3, our Platform performs Computer Vision-based analysis on screenshots captured during web analysis. Screenshots of web content are passed through an Object Detection AI model that mimics how a user might perceive the page by:
- Detecting whether a webpage is a login page, based on visual structure and layout.
- Recognizing brand logos and matching them to known companies (e.g., Microsoft, Google, Dropbox) to help identify impersonation attempts.
This model analyzes screenshots independently from the DOM structure, making it more resilient to obfuscation techniques commonly used in phishing.
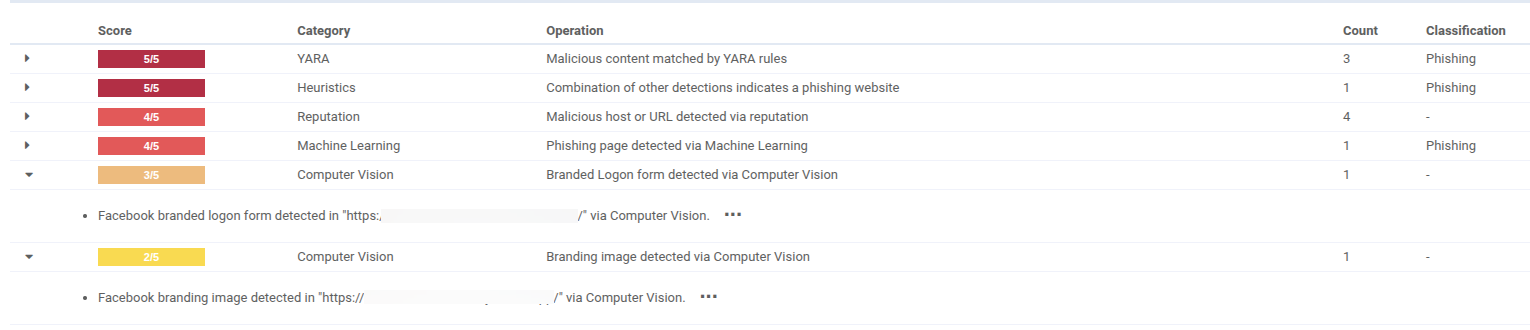
VTIs powered by vision
The output from our CV models is integrated into VMRay Threat Identifiers, our behavioral rule engine. By incorporating visual elements like logo and layout detections, the CV-enhanced VTIs offer several advantages:
- Resilience against DOM evasion: Phishing sites often manipulate their page source DOM to avoid detection, but visual appearance remains critical to deceiving users. CV provides a fallback path when DOM parsing fails.
- Better brand spoofing detection: Even if a single character or URL is changed, visual clues like a logo or “Submit” button in the right spot can reveal the real intent.
- Efficiency and accuracy: DOM analysis is expensive and complex, especially on modern dynamic websites. CV helps reduce processing load while improving detection accuracy.
Privacy-first
We understand that screenshots can be sensitive. That’s why we built our CV pipeline with privacy and security at its core:
- All screenshots are processed in-house, never sent to third parties.
- Our AI models are pre-trained, meaning they do not learn from or store customer screenshots or data.
- The entire system is cloud-native and self-hosted, ensuring complete data sovereignty for our customers.
The result: better phishing detection, blind spots closed at light speed
By combining traditional behavioral analysis, DOM inspection, and now Computer Vision AI, VMRay delivers a multi-layered approach to phishing detection that’s more resilient and aligned with how phishing actually works.
For those who keep it local, we’ve got something new
This release also brings some updates for our On Premises customers; we’re happy to share two important upgrades designed to boost your performance and compliance.
VMRay Platform upgraded to Ubuntu 24.04 LTS
The VMRay Platform now runs on Ubuntu 24.04 LTS, bringing improved compatibility and better performance across the board. With a newer Linux kernel and updated system libraries, this upgrade delivers:
- Enhanced support for modern hardware
- Increased resource efficiency for large-scale deployments
- Critical security patches and performance optimizations
Whether you’re scaling your analysis infrastructure or tightening system hardening, this update lays a stronger foundation for high-performance environments.
More SSO security options
Additionally, we introduced a new option to sign VMRay-initiated SSO authentication requests digitally. For customers with strict compliance requirements, this adds an additional layer of trust and validation during login attempts, helping ensure that SSO workflows remain secure and auditable.

Source: https://ubuntu.com/blog/ubuntu-desktop-24-04-noble-numbat-deep-dive
New Connectors on board
VMRay Platform already offers a range of connectors, enabling easy integration and data exchange with other security tools and systems. Over the past few weeks, we’ve been developing new integrations, and we’re ready to announce that they’ve just been released in their 1.0 versions. The latest additions include:
Microsoft Sentinel
We’re pleased to release version 1.0 of the Microsoft Sentinel connector for VMRay. This polished integration automatically enables VMRay enrichment information within Microsoft Sentinel. Give it a try today! Visit the https://github.com/vmray/ms-sentinel page for detailed integration and installation instructions.
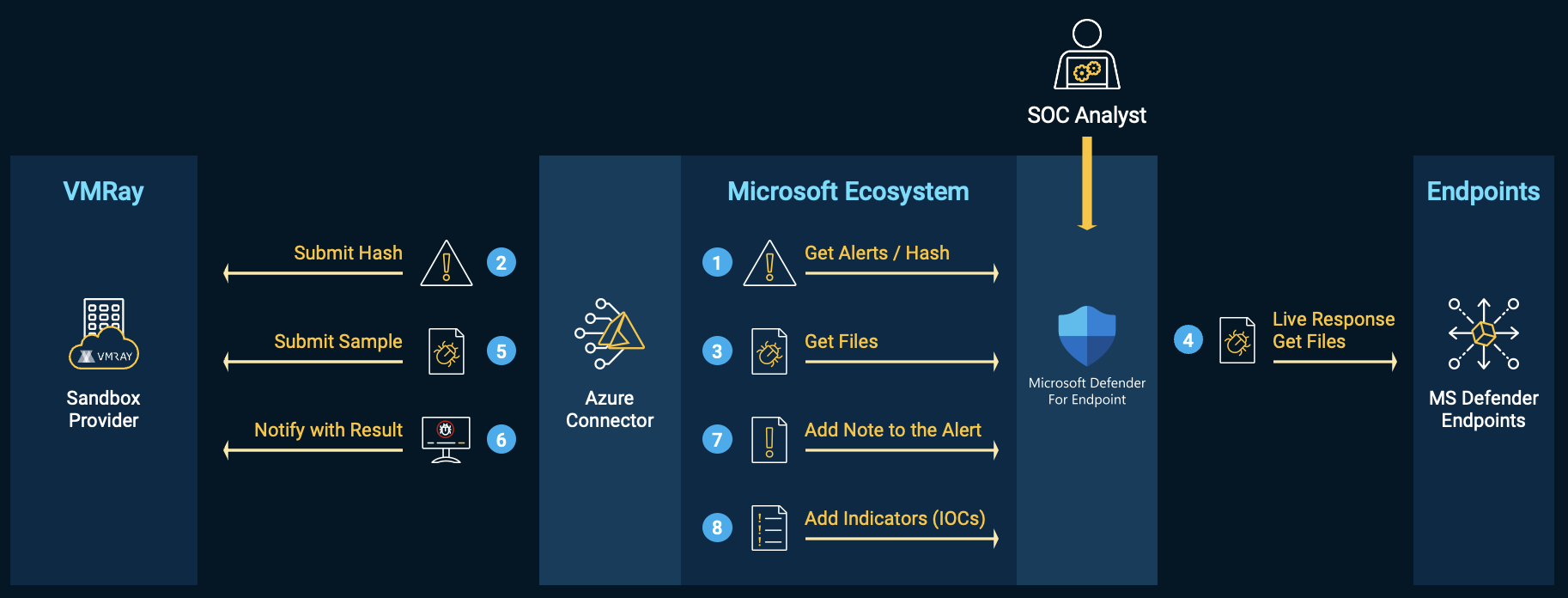
Microsoft Defender for Endpoint
In the 2025.2.0 release, we introduced the second beta version of the Microsoft Defender for Endpoint connector for integration with the VMRay Platform. We’re now pleased to announce the official release of version 1.0, which includes several enhancements, such as filtering by alert severity and status, and adding tags to VMRay submissions, which now show the threat name in Microsoft Defender. We encourage you to give it a try! For detailed integration and installation instructions, visit: https://github.com/vmray/ms-defender-azure.
Final thoughts
We hope you will greatly benefit from our development teams’ work. From the improved Live Interaction UX to making the best of AI for better phishing detections, new connectors, and impactful On Premises improvements, there’s a lot to explore.
Going forward, we will be on the lookout for further Live Interaction improvements, fine-tuning our newly released threat intelligence feed, as well as monitoring and exploring what else we can do better to stay ahead of constantly evolving phishing threats.
As we march through 2025, one more release is still on the horizon, promising valuable updates by the end of October. In the meantime, enjoy the warmth of summer and the upcoming holiday weeks. Stay tuned as we continue this journey together!
如有侵权请联系:admin#unsafe.sh