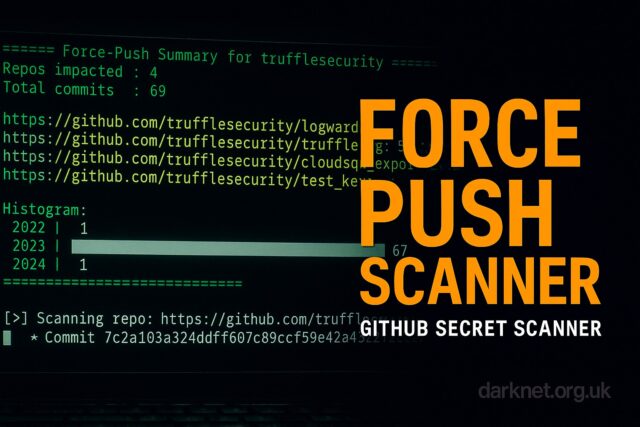
Force Push Scanner is an offensive security tool that identifies secrets inadvertently left in deleted commits following GitHub force‑push events. Developed by Truffle Security, it leverages GitHub Archive logs to surface ephemeral exposures in developer workflows.
Overview
GitHub force push allows users to overwrite branch history, often to remove sensitive information such as API keys, credentials, or tokens. While the intention is to erase sensitive data, artefacts remain accessible in dangling commits—unreferenced snapshots retained temporarily on GitHub’s infrastructure. Force Push Scanner monitors these events in real-time, extracts Git commit diffs, scans for secrets, and reports exposures before they are permanently deleted.
The tool integrates with GitHub Archive, a project that archives all public GitHub events. It parses push events and specifically scans for force type pushes, then retrieves commit contents to apply regex and entropy-based secret detection.
Features
- Real‑time monitoring of GitHub force‑push events
- Regex patterns and entropy heuristics to find credentials
- Docker container for easy deployment or direct Python execution
- Configurable alerting via Slack or email
- Log events for further audit or red team reporting
Use Cases
Red teams can deploy Force Push Scanner to stealthily monitor target repositories during penetration tests or red team engagements. It identifies leaked credentials before defenders uncover them. Security teams can also test developer hygiene by simulating monitoring to flag misconfigurations.
Since it tracks all public force pushes, the tool can be used for open-source intelligence, identifying high-profile targets that leak secrets, which is useful for OSINT and threat researchers.
Red Team Relevance
Force Push Scanner enriches post-exploitation workflows by harvesting credentials from publicly discarded history. These secrets may lead to cloud access, token reuse, or lateral movement paths. It complements existing reconnaissance frameworks such as Caracal for clandestine persistence and Force Push Scanner for credential harvesting, expanding both red and blue team visibility.
Comparison with Other Tools
Unlike tools like GitLeaks or TruffleHog, which scan current repositories, Force Push Scanner targets ephemeral history that defenders rarely monitor. That history may contain freshly committed secrets that are later removed. This real-time scavenging fills a gap in traditional secret scanning workflows.
Detection, Avoidance, and Mitigation
- Disable force-push on protected branches to prevent secret leaks via history rewriting
- Implement pre‑push secret scanning via Git hooks
- Maintain audit logs for force pushes and enforce peer reviews
- Use dedicated secret management solutions to reduce the risk of accidental commit
Deployment
To deploy via Docker, use:
docker pull trufflesecurity/force-push-scanner docker run -e GITHUB_TOKEN=your-token trufflesecurity/force-push-scanner |
Alternatively install via Python:
pip install force-push-scanner force-push-scanner --token your-token --slack-webhook <URL> |
Final Analysis
Force Push Scanner is a focused offensive tool that turns a common developer habit into a reconnaissance opportunity. It highlights how ephemeral commit history contains high-value intelligence for red teams. By integrating real-time secret discovery into workflows, teams can both simulate adversarial activity and harden developer pipelines.
You can read more or download Force Push Scanner here: https://github.com/trufflesecurity/force-push-scanner