2020-09-08 - Trickbot gtag ono72
2020-09-08 - TRICKBOT GTAG ONO72ASSOCIATED FILES:2020-09-08-Trickbot-gtag-ono72-IOCs.txt.zip 2020-09-10 07:56:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:125 收藏
2020-09-08 - TRICKBOT GTAG ONO72ASSOCIATED FILES:2020-09-08-Trickbot-gtag-ono72-IOCs.txt.zip 2020-09-10 07:56:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:125 收藏
2020-09-08 - TRICKBOT GTAG ONO72
ASSOCIATED FILES:
- 2020-09-08-Trickbot-gtag-ono72-IOCs.txt.zip 1.5 kB (1,536 bytes)
- 2020-09-08-Trickbot-gtag-ono72-IOCs.txt (4,515 bytes)
- 2020-09-08-Trickbot-gtag-ono72-infection-traffic.pcap.zip 3.5 MB (3,511,464 bytes)
- 2020-09-08-Trickbot-gtag-ono72-infection-traffic.pcap (5,674,932 bytes)
- 2020-09-08-Trickbot-gtag-ono72-malware-and-artifacts.zip 1.2 MB (1,249,909 bytes)
- 2020-09-08-Trickbot-EXE-gtag-ono72.bin (672,166 bytes)
- 2020-09-08-Word-doc-with-macros-for-Trickbot.bin (146,432 bytes)
- 2020-09-08-longrip.png-EXE-from-45.67.228.196.bin (774,144 bytes)
- 2020-09-08-parodyud.vbs-dropped-by-Word-macro.txt (10,490 bytes)
- 2020-09-08-scheduled-task-to-keep-Trickbot-persistent.txt (3,518 bytes)
- 2020-09-08-shortwave.png-EXE-from-45.67.228.196-1-of-2.bin (774,144 bytes)
- 2020-09-08-shortwave.png-EXE-from-45.67.228.196-2-of-2.bin (774,144 bytes)
NOTES:
- All zip archives on this site are password-protected with the standard password. If you don't know it, see the "about" page of this website.
IMAGES
Shown above: Word document with macros for Trickbot.
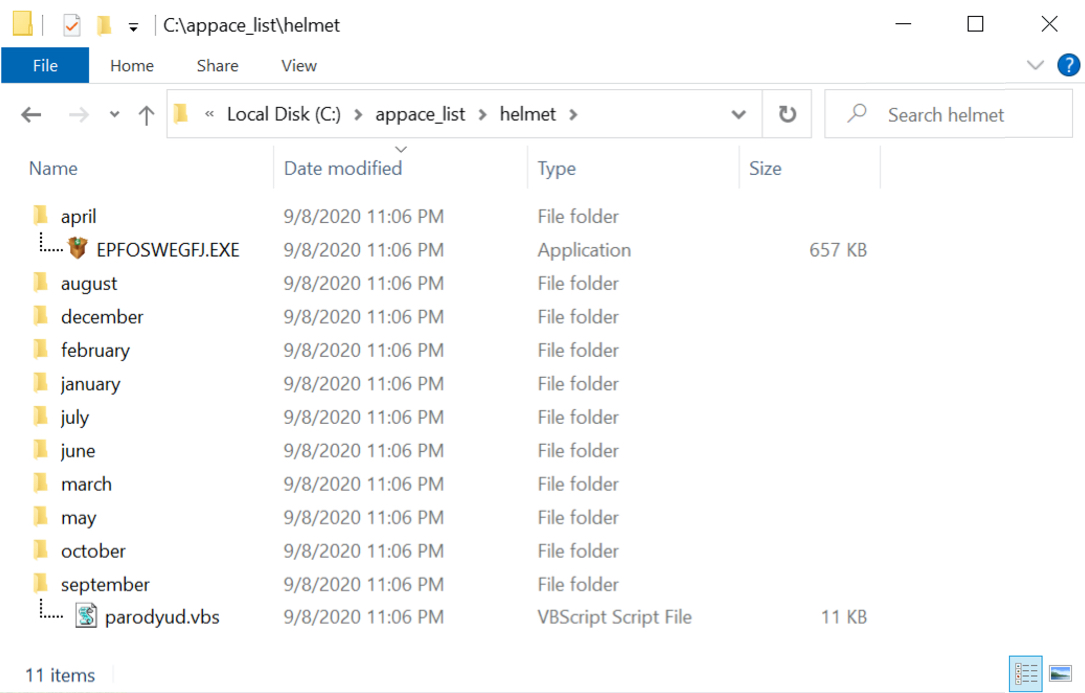
Shown above: EXEE and VBS files from the infected Windows host.
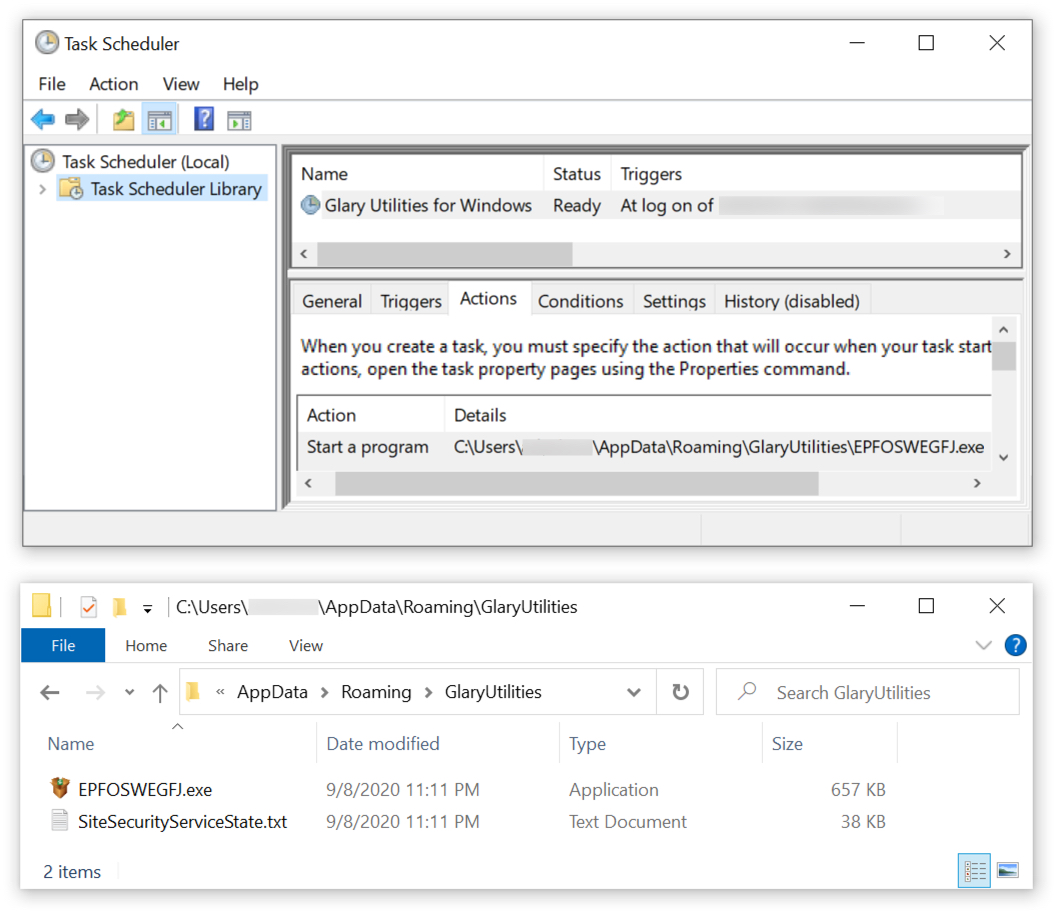
Shown above: Scheduled task to keep the infection persistent.
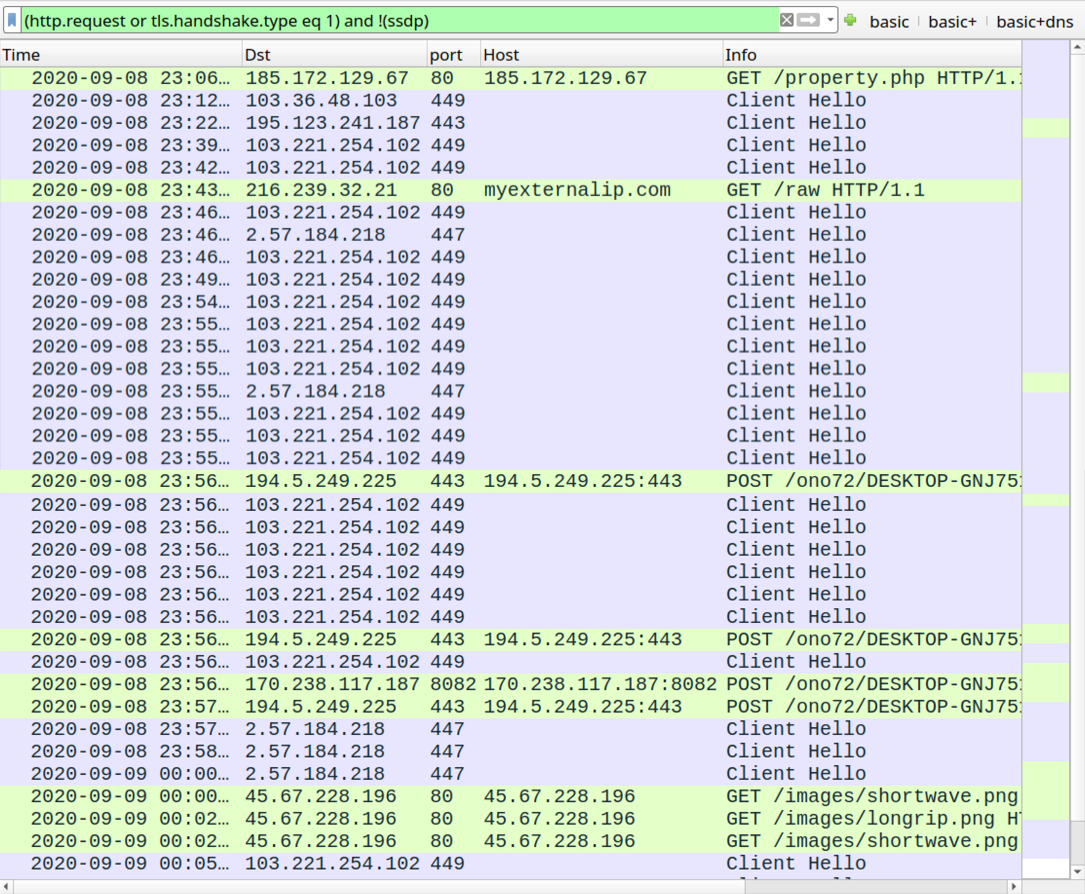
Shown above: Traffic from the infection filtered in Wireshark.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2020/09/08/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh