
文章介绍了如何利用HEVD中的Race Condition(Double-Fetch)漏洞进行攻击。通过分析漏洞机制和源代码,展示了如何在Windows 10中绕过保护并执行Shellcode。 2025-7-11 11:0:14 Author: xavibel.com(查看原文) 阅读量:13 收藏
Hi everyone,
In this blog post, I’m going to explain how to exploit a Race Condition (Double-Fetch) vulnerability in the HEVD (HackSys Extreme Vulnerable Driver) in a Windows 10 Pro:
https://github.com/hacksysteam/HackSysExtremeVulnerableDriver
This post will be divided into two parts:
- Vulnerability Identification & Exploitation
- Protection Bypasses & Shellcode Execution
In the previous post, you can find also the explaination of how to install the vulnerable driver, and some of the generic function that I’m using to find ntoskrnl.exe base address:
HEVD – Write-What-Where – Windows 10 Pro – SMEP, kCFG, kASLR protections
1. Vulnerability Identification & Exploitation
1.1 Vulnerability Analysis
Disclaimer: After spending some time studying this topic, this is how I currently understand the vulnerability. Please note that it might not be 100% accurate, this is the first race condition I’ve ever tried to exploit. So I highly recommend double-checking it on your own as well. Thanks! 🙂
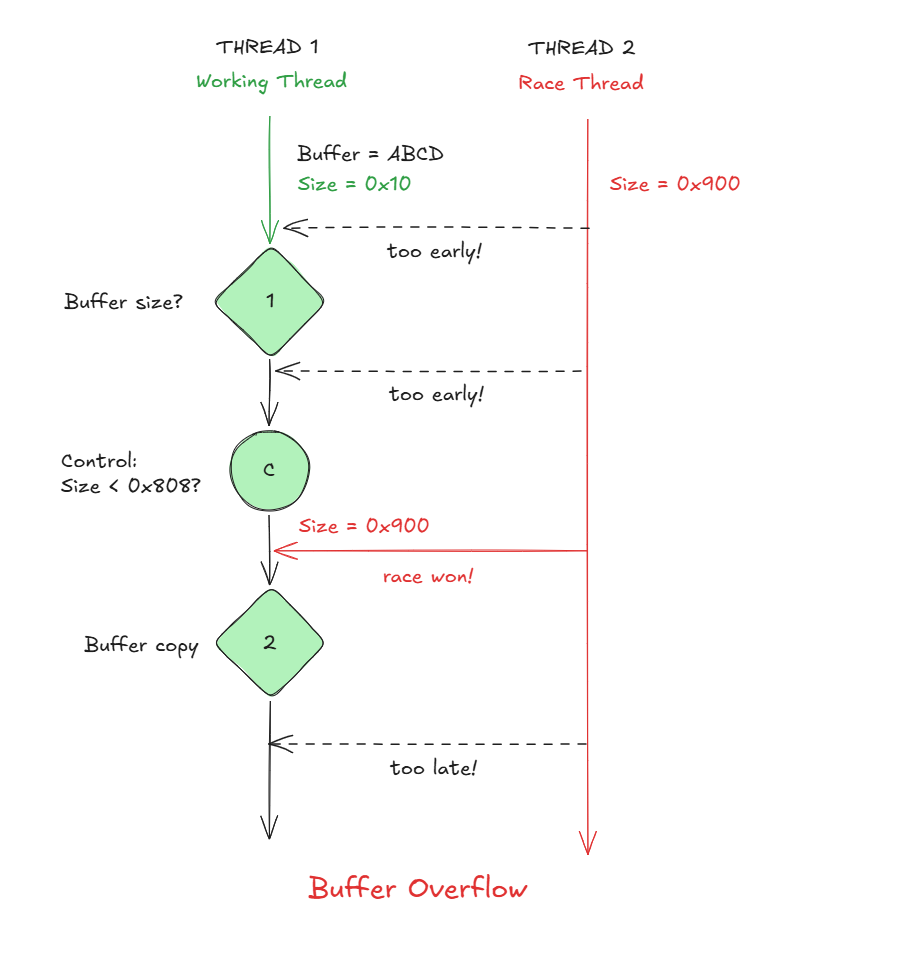
The vulnerability in this case is commonly known as a double fetch, which is a specific type of TOCTOU (Time-Of-Check to Time-Of-Use) race condition.
Here’s how I understand the flow:
- The driver first fetches a value (in this case, the Size field from a user-controlled structure).
- Then it checks whether the size is acceptable (e.g., if size < 0x808).
- Later, it fetches that same value again during a memory copy operation. (Double-Fetch)
Since both reads are directly from userland memory and there’s no internal copy made, a second thread can race in and modify the value between the check and the use. If the size is changed after passing the validation but before the copy, the driver will end up copying more data than intended, causing a kernel stack buffer overflow.
1.2 Source Code
Here we can see the vulnerability:
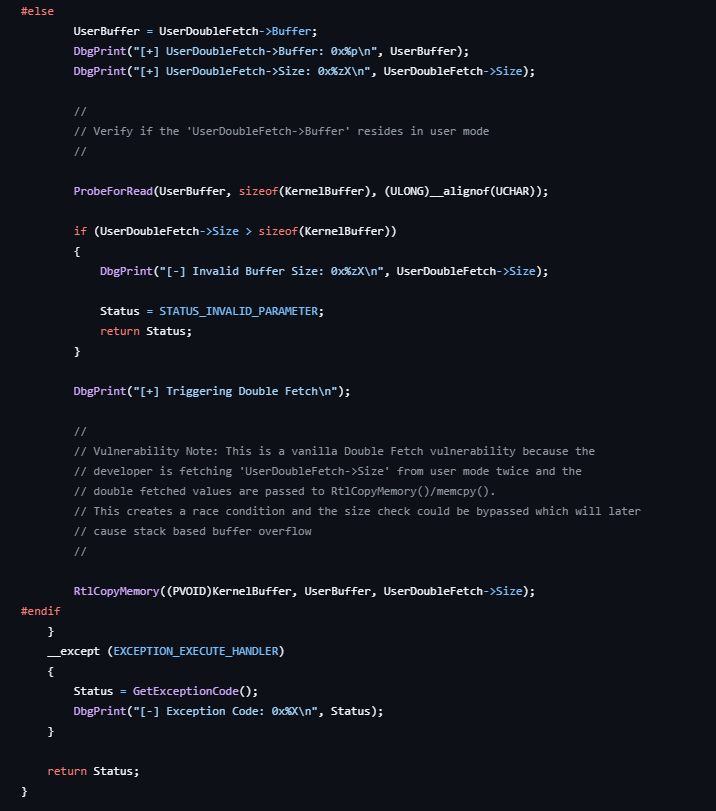
Link to the source code:
DoubleFetch.c
Link to the structures (we will need them later):
DoubleFetch.h
1.3 Reversing
This entry was posted in Uncategorized. Bookmark the permalink.
如有侵权请联系:admin#unsafe.sh