r/netsec是一个由社区管理的技术信息安全内容聚合平台,旨在为安全从业者、学生、研究人员和黑客提供有价值的信息。最近发现某语言学习网站存在XSS漏洞,通过绕过前端过滤直接注入有效载荷,在用户个人页面触发存储型执行。 2025-7-9 03:16:41 Author: www.reddit.com(查看原文) 阅读量:9 收藏
/r/netsec is a community-curated aggregator of technical information security content. Our mission is to extract signal from the noise — to provide value to security practitioners, students, researchers, and hackers everywhere.
![]()
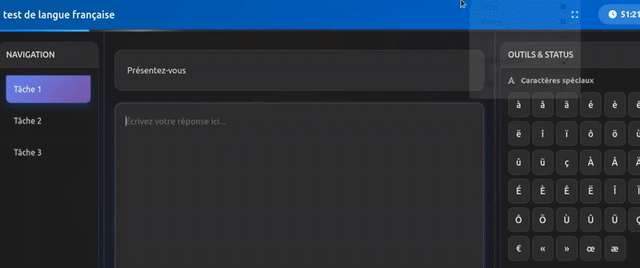
I recently tested a language-learning site that used live frontend filtering to block HTML input (e.g., <img> <svg> tags were removed as you typed).
But by injecting the payload directly via browser console (without typing it), the input was submitted and stored.
Surprisingly, the XSS executed later on my own profile page — indicating stored execution from a DOM-based bypass.
I wrote a short write-up here:
enjoy
如有侵权请联系:admin#unsafe.sh
