文章揭示了AI幻觉导致的恶意软件威胁——"AI Slopsquatting"。黑客利用大型语言模型生成的虚假包名创建恶意软件,并上传至公共仓库。开发者因依赖AI建议而安装这些包,导致系统感染、数据泄露及高额损失。文章强调需谨慎验证包来源并采取安全措施以防范此类威胁。 2025-7-7 15:18:20 Author: hackernoon.com(查看原文) 阅读量:7 收藏
You’re rushing to finish a Python project, desperate to parse JSON faster. So you ask GitHub Copilot, and it confidently suggests “FastJsonPro”. Sounds legit right? So you type pip install FastJsonPro and hit enter.
Moments later, your system’s infected. Your GitHub tokens are gone, your codebase is leaking to the dark web, and your company is facing a
This isn't a typo. It's AI slopsquatting, a malware trick that exploits large language model (LLM) hallucinations.
Let me show you how hackers turn AI’s mistakes into malware, why coders like you are the perfect target, and how to lock down your code.
In a world where AI writes your code, one bad install can sink you. Want to stay safe? Let’s start.
What’s AI Slopsquatting?
AI slopsquatting is a situation when hackers exploit AI’s wild imagination. Sometimes, LLMs like ChatGPT or Grok invent fake package names that sound real but don’t exist. Attackers spot these hallucinations, create malicious packages with those exact names, and upload them to public repositories.
It’s not a misspelling (like typosquatting). It’s worse, because AI confidently recommends something that was never real, and someone makes it a danger.
This threat popped up in 2024 as AI tools became a part of everyday coding.
Slopsquatting turns trust into a trap. If you’re coding in 2025, this is your wake-up call: AI’s suggestions aren’t always safe.
**How Slopsquatting Tricks You
\
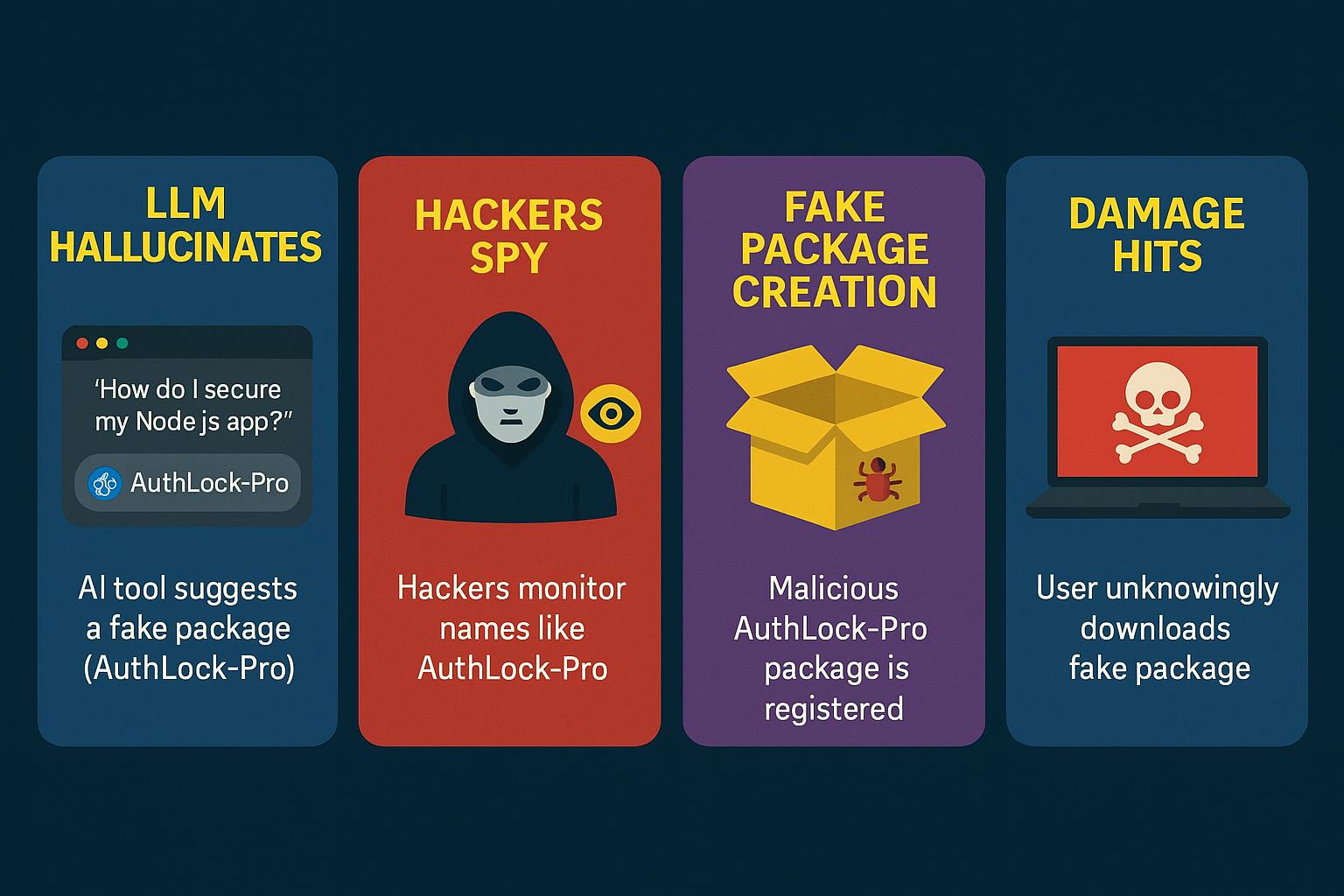
Here’s how hackers pull off this scam, step by step:
LLM hallucinates
You query an AI tool (e.g. How do I secure my Node.js app?). It suggests AuthLock-Pro, a fake package, because of gaps in its training data.
Hackers spy
They monitor and scrape LLM outputs on various platforms like GitHub, X, or Reddit to find hallucinated names developers mention. They might spot patterns like AuthLock-Pro popping up frequently.
Fake package creation
Attackers create a fake package with that exact name (AuthLock-Pro) and then upload it to PyPI or npm. These packages often mimic legitimate ones with solid READMEs.
You install it
You trust the AI’s recommendation and unknowingly download the fake package. The package blends into your normal workflows but quietly infects your system.
Damage hits
Once installed, the malware steals your credentials, leaks code, or plants ransomware. And one infected dependency can compromise your entire organization, CI/CD pipelines, open-source projects, and downstream users.
Attackers even use AI to tweak package names and descriptions, with 38% mimicking real ones.
Open-source LLMs hallucinate 21.7% of the time, so this threat’s ready to blow up.
Why You’re an Easy Target
Slopsquatting shines because it preys on your habits. Here’s why it works:
Over-reliance on AI
The majority of coders use AI tools, and most of them don’t verify the package suggestions. If Copilot suggests FastPyLib, you roll with it.
Deadline pressure
Tight deadlines can push you to download packages without verifying the package maintainers or download stats, especially when the AI suggestion appears functional.
Convincing fakes
38% of hallucinated names resemble real ones, with credible documentation that makes them bypass casual security.
Hackers move fast
Attackers register hallucinated package names hours before you notice.
One wrong install can affect your entire organization, leaking data and triggering a breach that costs
Slopsquatting in the AI Threat Scene
Slopsquatting is part of a bigger AI-driven crime wave, tying into threats like phishing and deepfakes:
Phishing
Hackers pair fake packages with AI-crafted emails, making it more effective than human scams.
Ransomware
Fake packages deliver ransomware like Akira, locking your system.
Deepfakes
You can get a
How to Fight Slopsquatting Malware
Good news: you can beat slopsquatting with vigilance and AI-powered defenses. Here’s how to lock it down:
For developers
Verify packages
Don’t just trust AI blindly. Visit PyPI, npm, or GitHub before installing and check the package age, as new packages are riskier. Then you check for the download counts, stars, issue history, and recent activity. Use tools like pip-audit or Socket to scan for known threats.
Track dependencies
Use a Software Bill of Materials (SBOM) to map every package and spot fake ones early.
Run dependency scanners
Use tools like Snyk, Dependabot, or Socket.dev to flag vulnerable packages before you install them.
Test locally
Run new packages in a sandbox or virtual machine to catch malware before it hits your main system.
For Organizations
Train smart
Run slopsquatting simulations to teach developers how to verify packages and identify AI hallucinations.
Use AI to fight AI
Deploy tools like Socket or SentinelOne to detect suspicious packages in real time.
Lock down your pipelines
Enforce zero trust. Restrict installs to vetted repositories and require multi-step approvals.
Monitor repos
Watch PyPI or npm for new packages that match hallucinated names. Flag those with low downloads or no history.
For security teams
Hunt threats
Add slopsquatting patterns to threat feeds. Monitor X or GitHub for AI-suggested packages chatter.
Secure CI/CD pipelines
Validate every new dependency with tools like GitHub Actions and SBOM checks before it hits production.
For AI providers
Fix hallucinations
Filter out package recommendations that don’t exist and cross check with PyPI or npm databases.
Warn users
Notify users when a suggestion might be inaccurate or unverified. You can label unverified suggestions with a “check this package” alert.
Bottom Line
AI is your coding buddy, but it’s also a hacker’s favorite tool.
Slopsquatting is a clever, rising threat to the global software supply chain. The same AI that speeds up your workflow can also invent backdoors for attackers.
If developers trust every AI suggestion, attackers only need one hallucination to breach entire systems.
You’ve got this though.
Verify every package, scan with Snyk, and test in a sandbox. Teams, train your devs, lock down CI/CD, and use AI to fight back.
This is a code war, and you’re on the front line. Run a package check today, share this guide, and block the next breach.
Don’t let AI’s imagination become your infection.
Code smart, stay sharp and win.
如有侵权请联系:admin#unsafe.sh
