Dalfox v2.12.0发布,新增高级XSS扫描功能及优化特性。包括更快扫描、智能载荷选择等新标志;支持自定义盲XSS载荷;新增代码库基XSS载荷;增加Markdown报告格式;服务器模式支持API密钥认证及CORS/JSONP;管道模式支持原始HTTP请求输入;修复漏洞并更新依赖;文档优化;未来计划包括改进文档及探索新扫描模式。 2025-7-6 00:0:0 Author: www.hahwul.com(查看原文) 阅读量:19 收藏
More powerful XSS scanning, Integration
Dalfox v2.12.0 has been released. It's been about three months since the previous version, 2.11, and this update includes various feature enhancements. Today, I'll briefly go over the new features that have been added.
Added advanced XSS scanning features
Four new flags have been added to improve the convenience and results of XSS scanning. I'd like to thank @ibrahmsql for contributing these features.
- --detailed-analysis: Performs deeper parameter analysis to uncover more XSS vectors
- --fast-scan: Enables faster scanning, useful in CI/CD pipelines
- --magic-char-test: Generates magic character payloads for manual analysis
- --context-aware: Selects payloads intelligently based on the response context
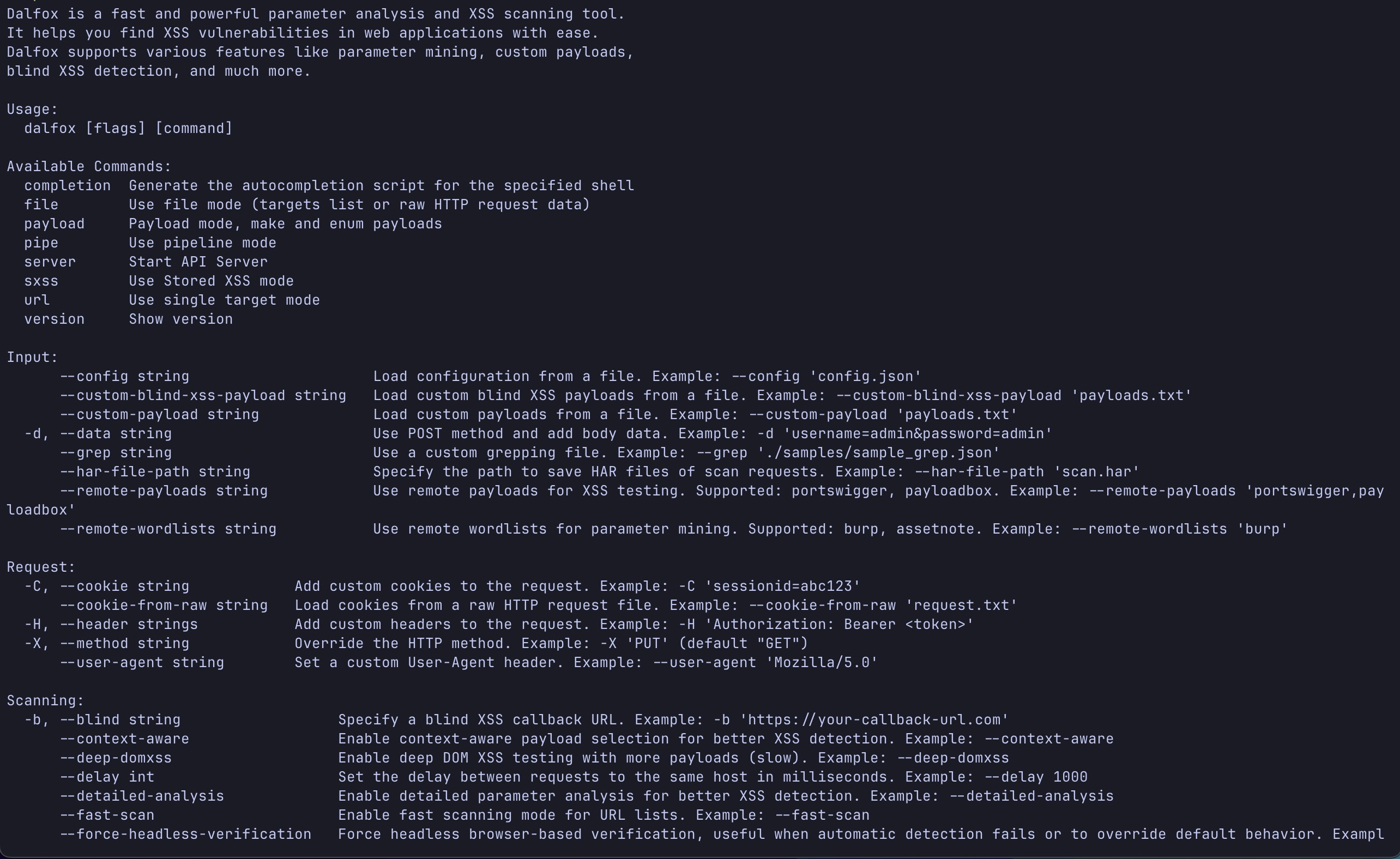
Improve help message (grouping)
The readability of the --help message has been improved. Options are now grouped by function, making it much cleaner and easier to read.
--custom-blind-xss-payload flag
Previously, only predefined values could be used for BSS (Blind XSS) payloads. Now, the --custom-blind-xss-payload flag allows users to specify their own custom payloads. This is useful in environments that require a private C2 or a specific format.
dalfox url http://test.com/?q=1 --custom-blind-xss-payload 'payloads.txt'
New payload patterns
Recently shared payloads have been added, such as those for codebase-based XSS.
<object data=# codebase=javascript:alert(document.domain)//>
<embed src=# codebase=javascript:alert(document.domain)//>
Add markdown report format
A markdown (or md) format has been added to the --report-format option. You can now save scan results as a clean markdown report, making it easy to integrate into other documents.
dalfox url "https://xss-game.appspot.com/level1/frame?query=AB" \
--report \
--report-format md
This feature is especially useful when connecting to Caido. Please refer to the Dalfox Caido Integration documentation.
Server mode
Here are the improvements for Server mode.
API Key based authentication
The --api-key flag has been added to Server mode. By setting an API Key with this flag, you can operate the scanner more securely by only allowing requests that include the key in the X-API-Key header.
# Start Server
dalfox server --api-key="SECRET" &
# Scan
curl --request POST \
--url http://localhost:6664/scan \
--header 'Content-Type: application/json' \
--header 'X-API-Key: SECRET' \
--data '{
"options": {
"use-headless": true,
"use-deepdxss": true,
"output-all": true,
"output-request": false,
"output-response": false,
"follow-redirects": true
},
"url": "http://testphp.vulnweb.com/listproducts.php?artist=123"
}'
CORS, JSONP support
Server mode now supports Cross-Origin Resource Sharing (CORS) and JSONP. The --allow-origins and --jsonp flags allow for more flexible integration of the Dalfox API with web applications from other domains.
dalfox server \
--allow-origins "https://www.hahwul.com" \
--jsonp
Pipe mode
Here are the improvements for Pipe mode.
Add raw HTTP request support to pipe mode
Pipe mode now supports Raw HTTP Request as a direct input, just like File mode. This significantly improves interoperability, as you can directly pipe requests copied from proxy tools like Burp, Caido, and ZAP for testing.
echo "POST https://www.hahwul.com/?q=dalfox HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: ko-KR,ko;q=0.8,en-US;q=0.5,en;q=0.3
Connection: keep-alive
Cookie: _ga=GA1.2.1102548207.1555467144; _gid=GA1.2.1362788908.1563875038
Upgrade-Insecure-Requests: 1
Host: www.hahwul.com
asdf=asdf" | ./dalfox pipe --rawdata
Bug Fixes & Dependency Updates
- Updated to a version of
chromedpwhere an upstream bug has been fixed. (It's recommended to update, as it was causing some errors). - Other minor bugs have been fixed, and dependency libraries have been updated.
Documentation
The documentation has been improved in line with the updates. @fabaff, who maintains dalfox in Nixpkgs, also contributed to the documentation updates. I'd like to thank him again.
Next Plan
In the future, Dalfox is planned to be improved in the following ways:
- Docs: We plan to overhaul the documentation to improve readability and accessibility.
- Features from Issues: We will review various feature suggestions reported as GitHub issues and incorporate them into development.
- New Mode: We are conceptualizing new scan modes, such as an Interactive mode that utilizes AI or proceeds with scans through user interaction.
Thank you to everyone who contributed to this release. This summer in korea is unusually hot, so I'll get to the next phase of work when the weather cools down a bit!
如有侵权请联系:admin#unsafe.sh