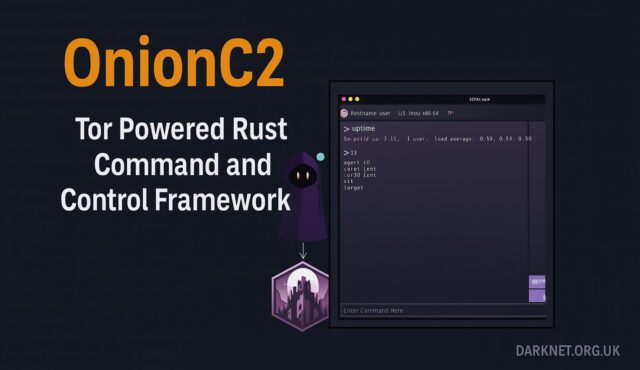
OnionC2 is an open-source C2 framework that uses Tor for encrypted, anonymised communications. The agent is written in Rust (using Arti), and the server and API are in Go, in a style compatible with XENA’s C2 interface.
Overview
OnionC2 enables red teams to establish a stealthy command-and-control channel over the Tor network. It leverages Tor’s onion routing to hide both the server and agent IP addresses, minimising detection risk. The architecture separates the data and control planes:
- The agent runs on the target system, compiled in Rust and linked with Arti (a Rust Tor implementation).
- The C2 server and API are written in Go and can be accessed locally or via the XENA GUI.
Key Offensive Features
- Encrypted, anonymised C2 traffic via Tor onion services
- Agent written in Rust for cross-platform payload delivery
- Windows persistence using registry and shortcut techniques
- Shell command execution, file upload/download, clipboard access, and system reconnaissance
- Planned screenshot capability for future situational awareness
- Time-based agent check-in (active hours) to reduce visibility
Installation and Use
# Server setup (requires Go and Tor) cd api go run . --api-key=YOUR_SECRET_KEY # Configure Tor onion service tor -f torrc # Build and configure agent cd agent # update get_address in config.rs with .onion URL cargo build --release # Deploy to target and run ./agent --api-key=YOUR_SECRET_KEY |
The server exposes two APIs: one for agent connections via a Unix socket or through the onion service, and another (by default, on port 8080) that serves the XENA C2 UI.
Operational Use Cases
- Initial access and post-exploitation via Tor to evade network monitoring
- Cross-platform red team operations using the Rust agent
- Secure remote access for lateral movement
- Maintaining persistence on Windows environments through stealth
- Adding slow, time-bound check-ins to minimise detection
Limitations and Defensive Considerations
- Arti provides only partial Tor feature coverage; running legacy Tor alongside is recommended.
- Detection is possible through unexpected Rust binaries, registry changes, or onion traffic.
- Still under active development; features may change or require stabilising.
Recommendation
OnionC2 is a valuable tool for anonymity-focused red teams that require a Tor-based C2 channel without the need for external proxies. Its cross-platform Rust agent and Go server make it suitable for engagements requiring stealth and encryption. This framework pairs well with screenshot or data exfiltration modules for complete campaigns.
Next Steps
- Deploy OnionC2 in an isolated lab to measure agent performance, persistence effect, and detection signals.
- Integrate agent builds into custom payload repositories and test against AV/EDR detection.
- Combine with stealth surveillance tools and secure exfiltration paths.
You can read more or download OnionC2 here: https://github.com/zarkones/OnionC2