人工智能(AI)显著改变了API安全格局,引入了自动化攻击、逻辑漏洞和业务逻辑滥用等新威胁。传统安全措施难以应对这些智能且快速演化的攻击。建议采用实时检测、强化认证机制和全面监控所有API以增强防护能力。 2025-6-26 07:6:8 Author: lab.wallarm.com(查看原文) 阅读量:25 收藏
AI has had dramatic impacts on almost every facet of every industry. API security is no exception. Up until recently, defending APIs meant guarding against well-understood threats. But as AI proliferates, automated adversaries, AI-crafted exploits, and business logic abuse have complicated matters. It’s no longer enough to merely patch known flaws; security teams must now contend with intelligent, adaptive attacks that evolve as fast as the technology they target.
AI: A Catalyst for API Risk
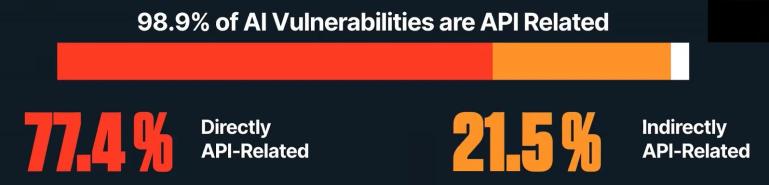
AI and APIs are inextricably linked, especially when it comes to security. According to the Wallarm 2025 API ThreatStats report, the number of AI-related CVEs skyrocketed in 2024, with a staggering 98.9% directly tied to APIs. Remember: AI-powered applications rely on APIs for communication, automation, and data exchange – and this reliance creates new opportunities for attackers.

Common weaknesses include:
- Weak authentication mechanisms: 89% of AI-powered APIs still use static keys, leaving them wide open to abuse.
- Externally accessible endpoints: 57% of these APIs are publicly exposed, often without proper controls.
- New vulnerability categories: Memory corruption issues—previously rare in API discussions—are rising due to AI’s reliance on binary APIs and hardware-level processing.
Remember: AI security is API security.
AI-Driven API Attacks: The Age of Adaptive Threats
However, AI is more than just an attack surface: it’s a threat enabler. Automated bypass techniques, particularly those exploiting logical vulnerabilities, are a severe and growing threat to the API security landscape, allowing attackers to evade detection mechanisms. Here’s how they work:
- Automated Analysis of API Behavior: Attackers use AI to analyze API interactions and gain an understanding of the underlying business processes and workflows. The AI systems monitor and learn from API responses to identify patterns and potential weaknesses in the business logic that could be exploited.
- Reverse Engineering Business Logic: With the API behavior mapped, AI tools then reverse engineer the application’s business logic, determining how it processes data and enforces rules so attackers can pinpoint where they can abuse logic.
- Identification of Logical Vulnerabilities: These insights help attackers identify specific logical vulnerabilities, such as:
- Broken Object Level Authorization: BOLA vulnerabilities occur when an API fails to validate permissions for every call to every object, allowing attackers to manipulate object identifiers in API calls to gain unauthorized access to data or functionalities.
- Broken Function Level Authorization: BFLA vulnerabilities allow users to access functions they are not authorized to use. For example, if an API has an endpoint intended for administrative purposes but lacks proper authorization checks, a regular user could exploit this to perform administrative actions.
- Exploitation Using Bots: Attackers then use bots to automate the exploitation process. These bots can adapt their strategies in real-time, modifying API requests to bypass security controls and manipulate the application’s behavior.
These types of attacks are particularly difficult to detect for two key reasons. First, the bots’ adaptability means that they can evade traditional, signature-based detection mechanisms. Second, AI-driven attacks can mimic normal human behavior, making them difficult to distinguish from legitimate activities without significant context.
Building Resilience Against AI-Driven Attacks
So, how can organizations protect themselves against these threats? It’s not easy, but it’s not impossible. Here are four best practices any organization should follow.
Adopt Real-Time Detection and Response
Traditional security measures fall short against ultra-fast, ultra-sophisticated AI-driven API attacks. Wallarm’s API Security Platform leverages AI-powered behavior-based anomaly detection to identify and block malicious API activity as it occurs, identifying automated behavior, and mitigating the damage these attacks can cause. Moreover, because Wallarm continuously collects and analyzes data, we gain the context necessary to adapt to emerging threats.

Enhance Authentication and Authorization Controls
Robust authentication and authorization are an essential part of API security. While Wallarm does not provide authentication and authorization for APIs, our platform supports these capabilities by identifying rogue APIs that might be missing authentication, ensuring that API endpoints are managed. Further, Wallarm identifies authentication and authorization vulnerabilities that allow attackers to circumvent security controls.
Inventory and Monitor All APIs – Especially Shadow Ones
Unmanaged APIs, like shadow or zombie APIs, are particularly vulnerable to AI-driven attacks. Wallarm’s API Discovery tool provides comprehensive visibility into your organization’s API landscape, automatically identifying all APIs, including undocumented and deprecated endpoints.

Schedule a Demo
Wallarm’s API security platform is the fastest, easiest, and most effective way to stop API attacks and AI-powered applications. We deliver a complete inventory of APIs, patented AI/ML-based abuse detection, real-time blocking, and an API SOC-as-a-service. Want to find out more about how we can protect your organization’s APIs? Schedule a demo today.
如有侵权请联系:admin#unsafe.sh