黑客分发伪造的 SonicWall NetExtender VPN 应用程序以窃取企业用户凭证。该恶意软件(代号 SilentRoute)模仿合法软件,绕过数字证书验证并窃取VPN配置数据发送至远程服务器。用户应从官方渠道下载应用以避免受骗。 2025-6-25 18:9:0 Author: securityaffairs.com(查看原文) 阅读量:5 收藏
Hackers deploy fake SonicWall VPN App to steal corporate credentials

Hackers spread a trojanized version of SonicWall VPN app to steal login credentials from users accessing corporate networks.
Unknown threat actors are distributing a trojanized version of SonicWall NetExtender SSL VPN app to steal user credentials. The legitimate NetExtender app lets remote users securely access and use company network resources as if they were on-site.
The malware-laced version, tracked as SilentRoute by Microsoft Threat Intelligence (MSTIC), mimics the legitimate software that allows remote access to company networks. Users installing the rogue app unknowingly expose their data, as attackers exploit it to gain unauthorized access and steal sensitive information.
A fake NetExtender site hosts a trojanized version signed by “CITYLIGHT MEDIA PRIVATE LIMITED” that steals VPN config data and sends it to a remote server, SonicWall warns.
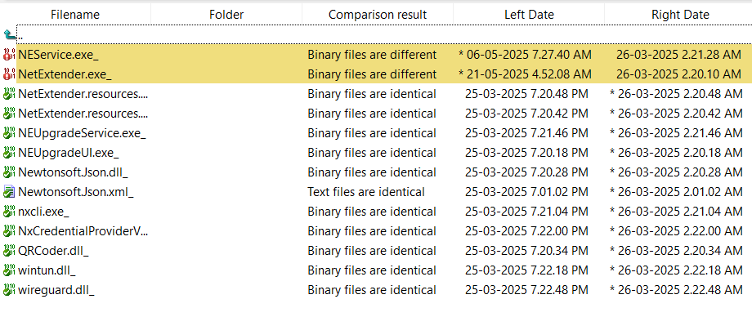
“The threat actor modified the following component files,” reads the advisory, “which are part of the NetExtender installer, to execute the application and send configuration information to a remote server:
- NetExtender.exe (Modified file; no digital signature)”
- NeService.exe (Modified file; digital signature is invalid)

The SonicWall NetExtender service normally checks the validity of its components’ digital certificates before running. If validation fails, it stops. In the trojanized version, attackers modified the code to bypass these checks, letting the program run even if validation fails. They also injected code into NetExtender.exe to steal VPN credentials, like username, password, and domain, and send them to a remote server (132[.]196.198.163:8080) as soon as the user clicks “Connect.”
SonicWall and Microsoft promptly took down the malicious sites hosting a trojanized NetExtender and revoked its certificate. Users should download the app only from official sources. The malware, dubbed “SilentRoute,” is detected by both SonicWall and Microsoft security tools.
The company also published Indicators of Compromise (IoCs) for this threat.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, SonicWall)
如有侵权请联系:admin#unsafe.sh