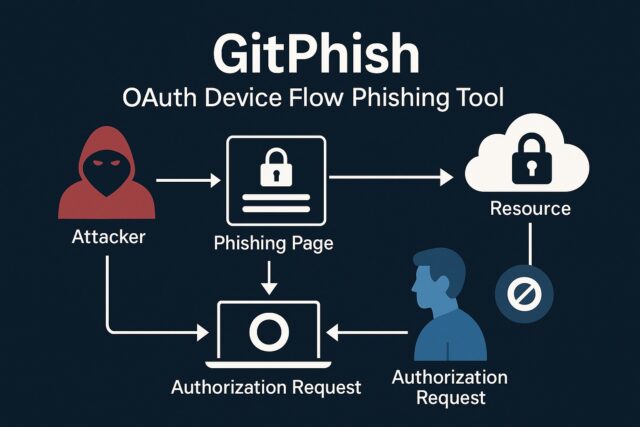
GitPhish is an automated tool that exploits GitHub’s OAuth device code flow to gain unauthorised access to user accounts. Developed by Praetorian, it demonstrates how attackers can use legitimate GitHub functionality to trick users into granting access to repositories, secrets, and CI/CD pipelines.
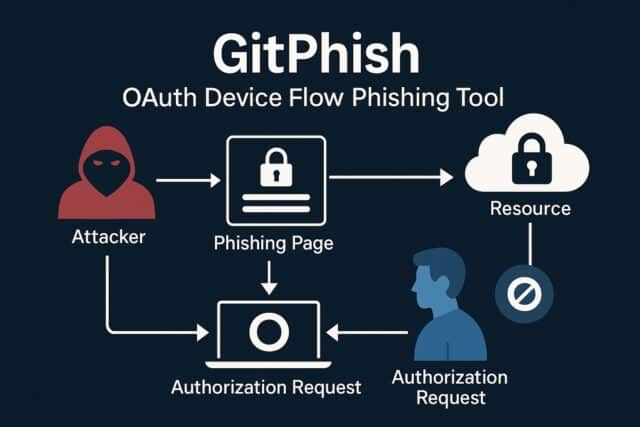
The attack does not rely on spoofed login pages. Instead, it generates real device codes through GitHub’s API, delivers them through custom GitHub Pages sites, and captures the resulting OAuth tokens once a user approves the request.
GitPhish will be publicly released on June 26, 2025.
Overview
GitHub’s device code flow allows devices without a browser to authenticate users via a separate interface. Users are asked to go to https://github.com/login/device and enter a code to complete the login. This mechanism is designed for ease of use but introduces a phishing opportunity: if an attacker can convince a user to enter a malicious device code, they gain full access granted by that token.
GitPhish automates this attack chain.
Key Features
- Generates GitHub OAuth2 device codes automatically
- Hosts phishing payloads on GitHub Pages
- Captures and stores valid OAuth tokens upon successful user authorisation
- Provides access to private repositories, secrets, GitHub Actions, and CI/CD integrations
- No need for password interception or fake login forms
Security Implications
This technique is currently not preventable by GitHub organisation policies. The device flow cannot be globally disabled. Most developers will not recognise malicious code or a delivery URL if it appears to come from GitHub infrastructure.
Security teams should review GitHub OAuth usage, revoke unnecessary tokens, and regularly audit external application authorisations. Additional monitoring should be in place for unusual authorisation events.
Installation and Usage
GitPhish is expected to be released under an open-source license on June 26. Installation will likely follow standard Python-based toolchain procedures. Based on the pre-release write-up, usage will follow a workflow similar to the one shown below.
# Clone the repository git clone https://github.com/praetorian-inc/gitphish.git cd gitphish # Install dependencies pip install -r requirements.txt # Launch phishing server and generate new device code python gitphish.py --start # Monitor incoming OAuth tokens tail -f logs/tokens.log |
More detailed usage documentation will be available upon release.
Mitigation Recommendations
- Enforce GitHub SSO wherever possible
- Regularly audit OAuth applications and tokens via the GitHub API
- Train developers to avoid authorising unsolicited device login requests
- Consider limiting developer GitHub access from unmanaged endpoints
You can read more here: Introducing: GitHub Device Code Phishing