Today I have discovered the PipelineFilterHook Registry entry only to find out that this blog post has already described it in detail. Nice work!
So, I decided to take a look at my favorite phantom DLLs again, and came up with this finding…
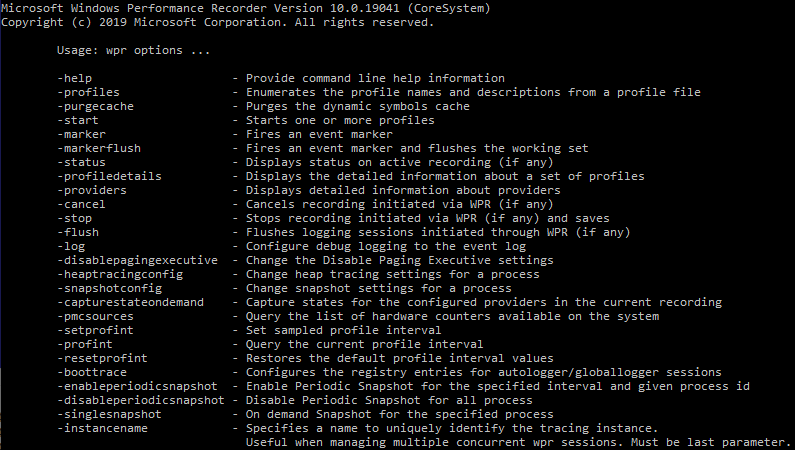
The wpr.exe program accepts many command line arguments:
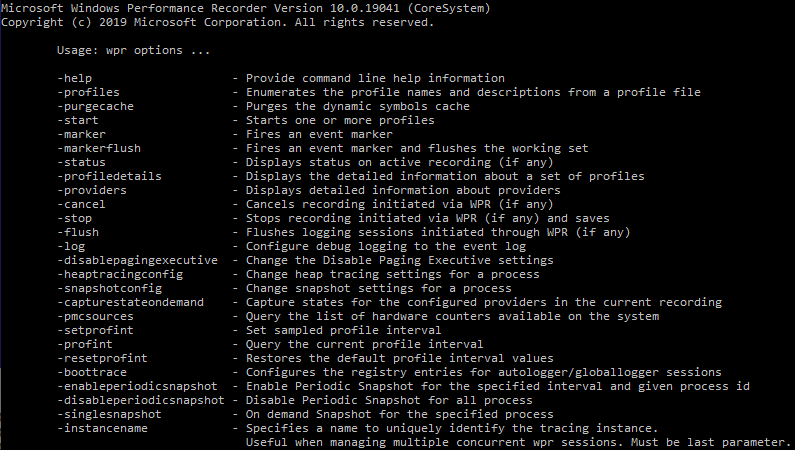
The ‘boottrace’ command line argument is one of them, and if we provide some reasonable, even non-sensical second command line argument to the program, we can trigger the execution of wpr.exe program’s path that will lead to loading of axeonoffhelper.dll from System32 directory. As it happens, axeonoffhelper.dll is a phantom DLL.
So, placing your payload in:
C:\Windows\System32\axeonoffhelper.dll
and then executing f.ex.:
wpr -boottrace -stopboot foo
will lead to C:\Windows\System32\axeonoffhelper.dll being executed.