VMRay Labs团队在2025年5月专注于新增威胁检测器(VTI),包括检测Windows防火墙修改、禁用Windows安全启动以及Linux环境中新服务创建;更新VideoSpy和Lumma Stealer配置提取器;新增近20个YARA规则以增强对多种恶意软件的检测能力。 2025-6-6 07:57:59 Author: www.vmray.com(查看原文) 阅读量:23 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cyber threat landscape.
In May 2025, the VMRay Labs team has been focused on the following areas:
1) New VMRay Threat Identifiers addressing:
- Detecting modification of Windows Firewall
- Detecting disabling Windows SafeBoot
- Detecting new service creation in Linux environments
2) New or updated configuration extractors for:
- VideoSpy (aka Wetfossil)
- Lumma Stealer
3) Again, this month, almost 20 new YARA rules!
Now, let’s delve into each topic for a more comprehensive understanding.
New VTIs
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis. Here’s a recap of the new VTIs that we added, or improved in the past month.
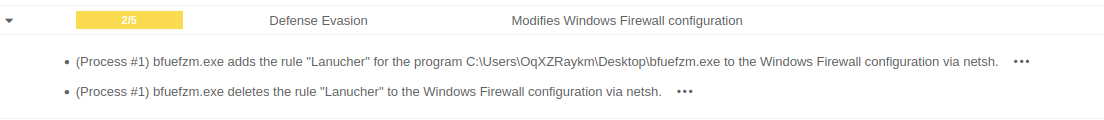
Detecting modification of Windows Firewall
Category: Defense Evasion
MITRE ATT&CK® Technique: T1562.004
Our Labs team recently analyzed a malware sample exhibiting suspicious manipulation — specifically, adding and removing firewall rules. In response, we created a new VTI designed to trigger when such behaviors are observed, as they are strong indicators of unwanted or unintentional tampering with the system’s configuration.
In legitimate cybersecurity operations, modifying firewall rules is a routine task, used by administrators to isolate systems, implement access controls, enforce security policies, or respond to incidents. However, when malware performs this action, its intent is rarely benign.
Malware may remove existing blocking rules in order to:
-
Sneak past security protections, like firewalls that block suspicious internet connections.
-
Open up the system to allow other attackers in or let the malware spread to other devices on the same network.
While it may seem counterintuitive, malware also often adds firewall rules to:
-
Silence security tools by blocking them from sending alerts to IT teams or antivirus systems.
-
Allow only its own activity through the firewall, keeping everything else out.
-
Create a “safe zone” where only specific traffic is allowed, making it harder for defenders to spot anything unusual.
Seen in the wild: Well-known malware families such as Emotet and TrickBot have demonstrated this tactic — disabling Windows firewall entirely or creating custom rules to allow their own processes to operate undisturbed.
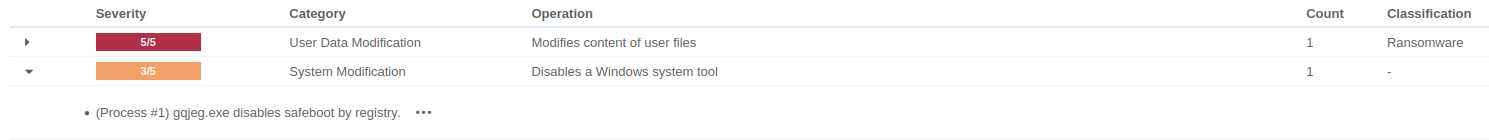
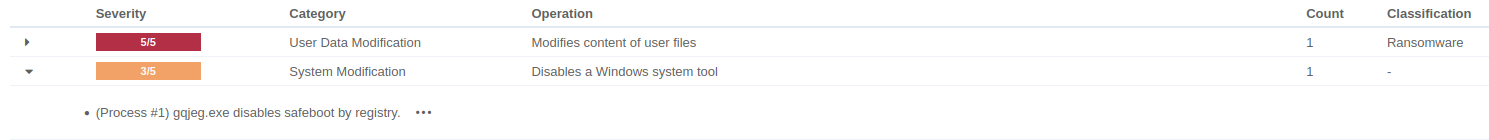
Detecting disabling Windows SafeBoot
Category: System Modification
MITRE ATT&CK® Technique: T1562.001
Safe Mode is a special Windows startup option that loads only the core components needed for the system to run. It’s widely used for troubleshooting issues such as malware infections, faulty drivers, or system instability. What makes Safe Mode work is a behind-the-scenes system configuration known as SafeBoot. This is a critical registry structure that defines which drivers and services Windows should load when entering Safe Mode. You can think of it like this:
- Safe Mode is the repair tool
- SafeBoot is the blueprint that tells the tool what parts of Windows are safe to load
Malware may attempt to delete the SafeBoot key for the following reasons:
1) Preventing recovery and delaying remediation: by deleting the SafeBoot registry key, attackers effectively disable Safe Mode, making it harder for responders to boot into a clean environment to investigate or remove threats. As a result, remediation must occur while the malware remains fully active, significantly increasing the risk of persistence or re-infection during the cleanup process.
2) Disrupting automated tools: some EDR/AV tools perform special scans or repairs in Safe Mode. Disabling SafeBoot blocks these automated recovery routines and allows malware to remain undetected longer.
In the past month, we introduced a new VTI that detects attempts to delete or disable SafeBoot on Windows systems to better defend against this technique.
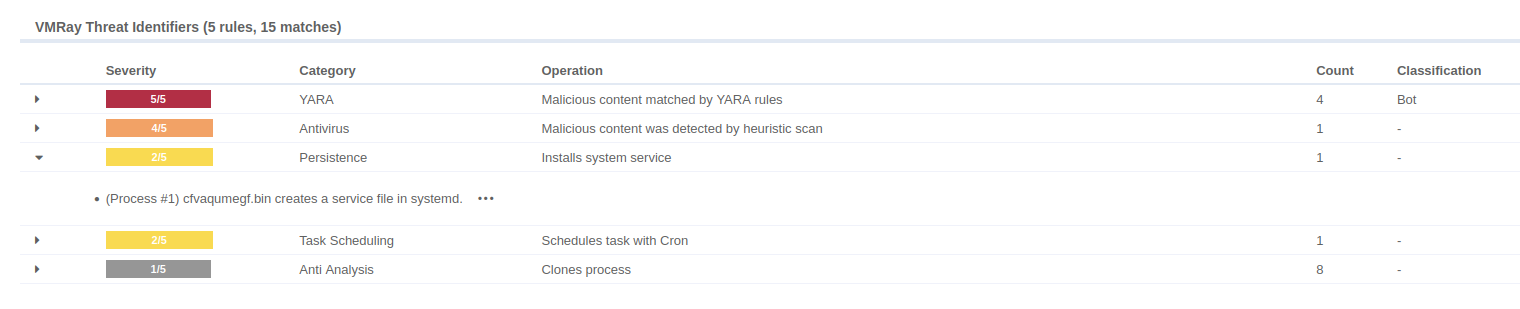
Detecting new service creation in Linux environments
Category: Persistence
MITRE ATT&CK® Technique: T1543.002
Persistence is key to a successful malware campaign, and attackers increasingly leverage native system tools to stay hidden. One such tactic involves creating a systemd service file — a legitimate way to manage background processes on modern Linux systems, but also one that can be misused by threat actors. A systemd service file tells the system how to start, stop, and manage a process, which makes it an ideal tool for malware looking to auto-start on boot, restart on failure, or run with specific privileges.
Prometei malware
During a recent investigation, our Labs team observed the Prometei malware employing:
-
Dropping a
systemdservice file, and -
Enabling it via
systemctl
This behavior in malware context should raise suspicion, as:
1) By creating a .service file in a systemd-controlled directory, the malware ensures it is automatically executed at system startup — a classic persistence mechanism.
2) When dropped into system-wide paths like /usr/lib/systemd/system/ or /etc/systemd/system/, the service is launched by systemd as root. This grants the malware full access to system files, processes, network settings, and even security tools — which it may disable.
3) The service file can include directives like Restart=always, meaning systemd will automatically restart the malware process if it is terminated, making remediation more difficult.
To counter this threat, we introduced a new VTI that detects when a new systemd service file is created by the analyzed sample.
Last month, we introduced a new YARA signature for the VideoSpy malware family (also known as Wetfossil). This emerging threat continues to gain traction in the wild, yet public knowledge about its behavior and capabilities remains limited.
As we highlighted previously, references to the name VIDEOSPY offer a strong hint about the malware’s functionality. Our ongoing analysis confirms that this malware is designed to perform invasive surveillance actions on compromised systems, including:
-
Silently activating the victim’s webcam
-
Capturing video feeds or snapshots
-
Exfiltrating this footage to a remote command-and-control (C2) server
To enhance visibility into VideoSpy’s and strengthen our detection capabilities, we developed and integrated a new malware configuration extractor into the VMRay Platform.
Lumma Stealer, this infostealer malware first spotted in 2022, has rapidly evolved into one of the most active threats in the cybercrime ecosystem. Written in C and sold as Malware-as-a-Service on Russian-speaking forums, Lumma continues to target sensitive user data — particularly cryptocurrency wallets and 2FA credentials. Despite recent takedown efforts, most notably Operation Endgame in May 2025, which aimed to dismantle major initial access malware operations including Lumma — the stealer continues to operate in the wild.
Over the past year, our Lumma config extractor, originally built to support version 4.0, has been a reliable tool for parsing and analyzing Lumma samples. But recent campaigns have shown signs of new variants.
We observed Lumma spreading through new and deceptive channels:
-
GitHub abuse: Threat actors are impersonating GitHub Security Team members in comments on that platform, urging developers to download supposed “fixes”, which are in fact Lumma payloads.
-
: Users are redirected to malicious web pages displaying phony CAPTCHA challenges. Interacting with these prompts PowerShell scripts that fetch and execute Lumma malware.
-
New version activity: Community posts on X and underground forums suggest that new Lumma variants are circulating in the wild, likely with updated configuration formats and evasion techniques.
In response, our configuration extractor logic was updated ensuring compatibility with recent builds of Lumma. Additionally, we refined our YARA rules to improve detection across new variants.
YARA Rules
The previous month’s detection updates brought a powerful boost to our Platform with over 20 new YARA rules! In this blog, we’ll give you a quick overview of the latest additions (again, almost 20 new or updated rules).
YARA coverage for stealers
CoinLurker
- CoinLurker is a Go-based stealer targeting cryptocurrency wallets and app credentials (Telegram, Discord, etc.).
- It spreads via fake software update alerts, malvertising, phishing emails, and deceptive CAPTCHA prompts.
- CoinLurker uses Microsoft Edge WebView2 to display convincing fake update dialogs that trigger payload execution upon user interaction.
BlihanStealer
- We introduced new YARA rules to detect BlihanStealer, a relatively new Windows-targeting infostealer first observed in late 2024.
-
Its notable capabilities include:
-
Windows Registry manipulation
-
Use of MPRESS compression to obfuscate code and evade detection
-
GremlinStealer
-
GremlinStealer is a fresh piece of malware that surfaced on Telegram in March 2025. Early analysis suggests it shares several components with the SharpStealer malware family, suggesting that it could be a modified variant or fork of that codebase.
- GremlinStealer is capable of stealing data from infected machines and uploading it to a dedicated web server, likely for resale or public exposure.
- It targets a wide range of information, including classic data types such as credit card credentials, browser cookies, and clipboard contents, as well as VPN and FTP login credentials.
StealC v2
-
First seen in early 2023, StealC is an infostealer introduced by a developer operating under the alias “Plymouth” on Russian-language cybercrime forums.
- Distributed via a Malware-as-a-Service model, StealC has quickly gained traction among threat actors due to its wide-ranging capabilities, including stealing browser data, cryptocurrency wallet information, and credentials from messaging apps.
- Recently, we identified signs of a new variant of StealC (v2) in the wild. To be better equipped against this new version, we updated our existing YARA rule that improves our detection coverage against the latest variant.
New signatures for recent Lumma version
- As mentioned in the updated configuration extractor’s description in this blog, we also enhanced YARA rule for Lumma to better support its recent variants.
YARA coverage for backdoors
FORSSHE/Bespin
-
The FORSSHE/Bespin backdoor is one of many malicious OpenSSH-based threats that specifically target Linux systems. It was thoroughly analyzed in ESET’s report “The Dark Side of the ForSSHe,” which uncovered 21 different backdoor variants — many of them previously unknown.
-
This particular malware is designed to steal credentials, provide covert remote access, and maintain persistence on infected machines by modifying legitimate SSH binaries.
WarmCookie
- We released a YARA rule to detect the WarmCookie backdoor, a growing threat seen in targeted phishing campaigns.
- WarmCookie is a Windows-based malware that gives attackers remote control over infected systems — allowing them to run commands, grab screenshots, manage files, and drop additional payloads.
- Threat actors are delivering WarmCookie via phishing emails that pose as job offers or invoice-related messages, luring users to download malicious scripts.
- Recent variants show signs of active development, including self-updating features and tighter persistence mechanisms.
YARA coverage for loaders
DonutLoader/Injector
- DonutLoader (aka donut_injector), a modular malware loader that leverages the open-source “Donut” framework to convert .NET assemblies, EXEs, DLLs, and scripts into in-memory shellcode — effectively bypassing traditional, file-based detection.
-
DonutLoader is known for:
-
Injecting code into legitimate processes, allowing stealthy execution under trusted binaries
-
Encrypting payloads, making reverse engineering and static analysis more difficult
-
- Actively used in targeted attacks, often delivered via phishing campaigns and vulnerability exploits (e.g., Microsoft’s memory corruption vulnerability in the Equation Editor component (CVE-2017-11882)), to deploy malware such as WARZONE RAT.
WINELOADER
- WINELOADER, a sophisticated backdoor attributed to APT29 (aka Cozy Bear), the Russian state-sponsored threat actor.
- The loader has been seen in spear-phishing campaigns posing as wine-tasting invitations from diplomats or political figures — a tactic aimed at high-profile targets.
- The infection chain starts with a PDF linking to a compromised site hosting a ZIP archive. This contains an obfuscated HTA file, which fetches and executes further payloads.
- Known targets include European diplomats and political parties, indicating the campaign’s geopolitical motivation.
KoiLoader
- KoiLoader is a notable loader targeting Windows systems, often acting as the delivery mechanism for Koi Stealer — a credential and data-harvesting infostealer written in C#.
- It spreads via phishing emails containing ZIP archives with disguised .LNK files. These shortcuts exploit a Windows bug to hide malicious command-line instructions, triggering the download of the loader.
- KoiLoader uses anti-analysis features such as region/language checks, obfuscated PowerShell and JavaScript scripts, and AMSI bypass mechanisms to evade detection.
Other YARA Updates
New signatures for CozyDuke/CozyBear
- CozyDuke, is a state-sponsored Advanced Persistent Threat (APT) malware toolkit, linked to Russian intelligence and targeting government, diplomatic, and critical infrastructure organizations globally.
- This toolkit employs custom malware, including backdoors, loaders, and reconnaissance tools, designed for stealthy, long-term espionage operations.
- Focuses on stealing sensitive information, including credentials, emails, and classified documents, often exfiltrated over encrypted channels.
New signatures for AteraAgent
-
We added new YARA rule to detect AteraAgent, a legitimate Remote Monitoring and Management (RMM) tool increasingly abused by threat actors.
-
While AteraAgent is commonly used by IT professionals and MSPs to remotely manage endpoints, deploy software, monitor system health. However, adversaries are leveraging it for:
-
Persistence in compromised environments
-
Data exfiltration and remote command execution
-
-
Due to its legitimate nature, AteraAgent often bypasses traditional defenses like firewalls and antivirus tools.
YARA coverage for XORDDoS (Linux)
-
We enhanced our existing YARA rule for XORDDoS, reflecting recent changes observed in this malware family’s code.
-
XORDDoS is a longstanding Linux Trojan that turns infected machines — including servers, IoT devices, and Docker containers — into bots for large-scale DDoS attacks.
-
The malware is named after its use of XOR encryption to obfuscate configuration data and communication with its command-and-control (C2) servers.
YARA coverage for COLDRIVER
- COLDRIVER is a Russian state-linked cyberespionage group active since at least 2015.
-
Known for spear phishing and credential harvesting targeting:
-
Western governments, think tanks, defense contractors, academics, and NGOs.
-
Individuals involved in Ukraine and NATO policy.
-
-
Its primary goal is Espionage, not financial gain — focused on stealing sensitive data.
-
In a recent article by Wesley Shields, a researcher at Google Threat Intelligence Group, she discusses new malware attributed to COLDRIVER: “Google Threat Intelligence Group (GTIG) has identified a new piece of malware called LOSTKEYS, attributed to the Russian government-backed threat group COLDRIVER. LOSTKEYS is capable of stealing files from a hard-coded list of extensions and directories, along with sending system information and running processes to the attacker.”
YARA signatures on malicious LNKs
-
At the start of last year, we introduced enhanced support for detecting Windows script-based threats triggered by .LNK files (Windows shortcuts) in the VMRay Platform.
-
Recently, we came across a clever use of an .LNK file that goes far beyond what you’d expect from a simple shortcut. In this case, the .LNK file was equipped to do more than just open a program. It was hiding a full attack chain inside its command line instructions, including the use of PowerShell or HTA (HTML Application) scripts, to download and run further malicious code.
- In plain terms: a user could double-click a shortcut file that looks harmless (like a link to a document), but behind the scenes, it launches code that downloads and runs malware directly in memory — without writing anything to disk. This technique allows attackers to bypass traditional AV tools, which often rely on scanning files saved to your computer.
Additionally, we implemented the following YARA detection rules:
- Suspicious PDFs: new YARA signatures designed to flag anomalous PDF files.
- SecureDoc2 phishkit: a dedicated signature to detect the emerging SecureDoc2 phishing kit.
- Real-time email validation phishkit: detection rules targeting phishing kits that leverage real-time email address validation techniques.
Final Thoughts
May 2025 was a busy month for our Labs team, marked by major enhancements to our VMRay Threat Identifiers, configuration extractors and a broadened, fine-tuned YARA rule set spanning multiple threat categories.
As attackers refine their tactics, our ongoing commitment remains clear — to stay ahead of the curve, proactively enhancing detection, and equipping defenders with the tools needed to counter modern cyber threats. Stay tuned for our next edition of signature and detection updates, planned to be published in the weeks ahead.
如有侵权请联系:admin#unsafe.sh