
一个复杂的加密货币盗窃活动通过npm包传播,恶意软件伪装成开发工具窃取用户钱包资金。攻击者利用混淆技术隐藏代码,并通过环境变量获取密钥进行非法交易。该活动涉及多个包,下载量超2100次,非法获利约450美元。 2025-6-3 11:21:35 Author: cybersecuritynews.com(查看原文) 阅读量:14 收藏
A sophisticated cryptocurrency theft campaign has emerged on the npm package registry, targeting developers and cryptocurrency users through malicious packages designed to drain Ethereum and Binance Smart Chain wallets.
The attack leverages heavily obfuscated JavaScript code to steal up to 85% of victims’ cryptocurrency holdings, demonstrating an evolving threat landscape where software supply chain attacks increasingly target digital assets.
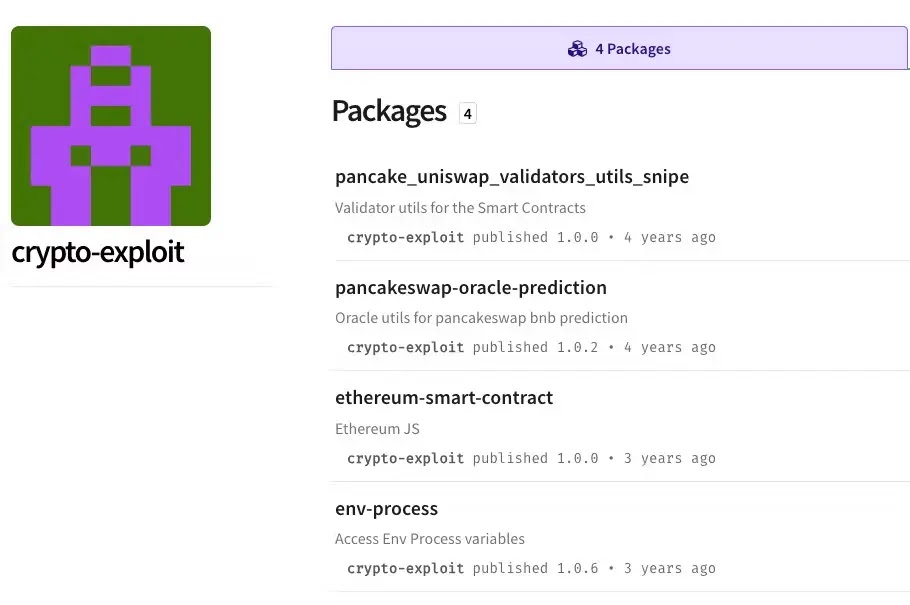
The malicious campaign centers around four npm packages published by a threat actor operating under the username @crypto-exploit, who registered using the email address [email protected] from a Russian webmail service.
.webp)
These packages collectively amassed over 2,100 downloads before being identified and reported as malware, with the most successful package, env-process, alone accounting for 1,054 downloads.
Socket.dev researchers identified the malware campaign and noted that the threat actor employed increasingly sophisticated tactics across multiple iterations of their malicious packages.
The packages masqueraded as legitimate cryptocurrency development tools, with names like pancake_uniswap_validators_utils_snipe, pancakeswap-oracle-prediction, ethereum-smart-contract, and env-process, designed to attract developers working with decentralized finance protocols and blockchain applications.
The attack methodology relies on victims inadvertently installing these packages and storing their private cryptocurrency wallet keys as environment variables, a common practice in development environments.
Once executed, the malicious code accesses these credentials and initiates unauthorized transactions to a hardcoded wallet address: 0x71448ec2D9c5fC4978F5A690D5CE11A8669C9D02.
Blockchain analysis reveals that this address received multiple transactions totaling approximately $450 worth of Ethereum during the campaign’s active period between 2021 and 2022.
Advanced Obfuscation and Deception Techniques
The most striking aspect of this malware campaign lies in its sophisticated use of JavaScript obfuscation to evade detection and analysis.
The threat actor employed hex-encoded string arrays to conceal the true nature of their code, making initial inspection extremely difficult for both automated scanning tools and human reviewers.
A prime example of this obfuscation can be seen in the original pancake_uniswap_validators_utils_snipe package, where critical variables were encoded as hexadecimal values.
The array var _0x450b = ["\x77\x65\x62\x33", "\x53\x57\x41\x50", "\x65\x6E\x76"...] translates to common JavaScript terms like “web3”, “SWAP”, and “env” when decoded.
This technique effectively hides function calls such as require("web3") and process.env from casual inspection.
The deobfuscated code reveals the malware’s core functionality: connecting to either Ethereum or Binance Smart Chain networks based on environment variables, retrieving the victim’s wallet balance, and constructing a transaction to transfer 80-85% of the funds.
The transaction logic follows this pattern: value: web3.utils.toWei((fbb * 80 / 100).toString(), "ether"), where fbb represents the victim’s current balance.
Notably, the threat actor deliberately avoids draining wallets completely, leaving 15-20% of funds untouched.
This calculated approach serves dual purposes: maintaining sufficient balance for transaction fees and reducing the likelihood of immediate detection by victims who might not notice partial fund transfers.
The campaign demonstrates concerning evolution in tactics, with later packages employing typosquatting techniques and more streamlined code.
The final iteration, env-process, likely targeted the legitimate Node.js process package, representing a maturation of the threat actor’s social engineering capabilities alongside their technical obfuscation methods.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
如有侵权请联系:admin#unsafe.sh

.png
)