CTI isn’t just for blue teams. Used properly, it sharpens red team tradecraft, aligns ops to real-world threats, and exposes blind spots defenders often miss. It’s not about knowing threats, it’s about becoming them long enough to help others beat them.

Learn from Adversaries to Inform Better Practices
Cyber Threat Intelligence (CTI) is often misunderstood within the security sphere. It is not just about reading threat reports or tracking high-level actors. It involves using historical data, evolving incident patterns, and the overlap of red and blue capabilities to understand how adversaries think, act, and adapt. Done well, CTI strengthens an organisation’s overall security posture by informing how defences are designed, tested, and evolved.
Much like the role of offensive security consulting, the real goal is not just to break things or prove a point. Despite how it may appear on the surface, offensive security is about defence. Whether you are a penetration tester assessing technical controls, a red teamer simulating adversary behaviour to identify gaps in detection and response, or a blue teamer monitoring alerts or hunting threats, everyone contributes to the same objective: helping organisations become harder targets.
Offensive Security != Threat Intelligence?
In many technical circles, people still separate offensive security and CTI as distinct, unrelated functions. While threat-led penetration testing and red teaming have gained traction, there is still limited discussion about offensive threat intelligence as its own focused discipline.
This goes far beyond copying IOCs or reading finished intelligence reports. Offensive Threat Intelligence means understanding adversary behaviours at a tradecraft level, recognising shifts in their tooling and tactics, and turning that knowledge into capability development. It feeds into emulation planning, operational decision-making, and validation of controls. This is where the red team benefits not just from thinking like an attacker, but from understanding how attackers evolve in the real world.
Bridging the Gaps
Traditional CTI roles tend to sit closer to defence. Analysts produce reports that guide blue teams or feed into SIEM rule creation. But there is just as much value for offensive teams. The key difference is in how the intelligence is applied.
When CTI is used to inform offensive simulation and adversary emulation, it becomes a force multiplier. Red teams can align their objectives with what real attackers are doing, in specific sectors or with certain motivations. This lifts exercises from basic exploit demonstrations to more advanced threat-informed operations that force defenders to address blind spots in their detection and response programmes and it also encourages blue teams to stay one step ahead developing detections for emerging techniques uncovered by red teams and thus identifying when malicious behaviour occurs in their environment.
Know Your Enemy
... and their motives
The best operators are not just technical. They understand attacker logic, motivations, and timing. Knowing how to exploit something is one thing, but understanding when an adversary would use it, how it would blend into network noise, and what outcomes they are pursuing is what separates decent red teams from great ones.
Adversaries are human. They follow incentives. They cut corners when needed. They reuse infrastructure, adopt publicly released tools, and sometimes leave operational mistakes behind. Yet they also innovate and share knowledge between groups.
By closely studying the tactics of advanced persistent threats, ransomware operators, access brokers, and other criminal groups, we gain better insight into how real attacks unfold. We learn how they chain weaknesses together, exploit poor segmentation, or target overlooked services. This context shapes how red teams operate, helping them emulate realistic behaviour rather than just chase high-value access like domain admin over and over again.
Understanding threat actor targeting also provides sector-specific awareness. Knowing which industry verticals are being targeted, and by whom, allows teams to tailor their operations for maximum relevance and realism.
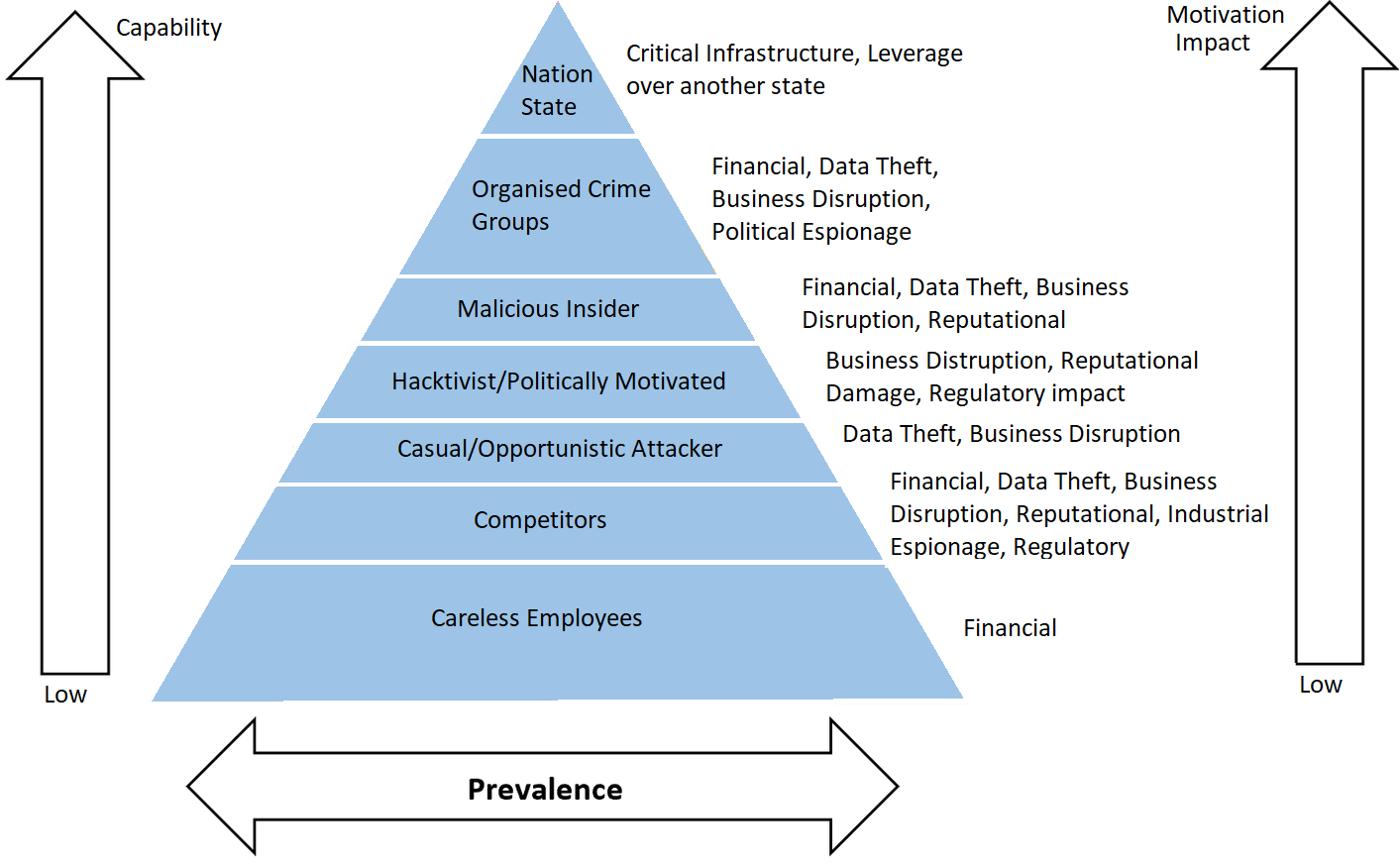
The accompanying diagram shows how an increase in attacker motivation and impact, alongside a rise in capability and prevalence, maps across different threat tiers.
If you are reading this not on blog.zsec.uk and the article is a word for word copy, know that the original is located on Andy Gill's blog.
CTI as an Offensive Security Focused Professional
At its core, CTI is about making sense of threats before they strike. It involves collecting, analysing, and synthesising information that reveals how digital assets might be compromised. But for red teams, it is not about indicators. It is about patterns of behaviour and how those patterns evolve over time.
CTI pushes red teams to stop chasing the same objectives over and over again. Instead of always reaching for domain admin, threat-informed operators design attacks that mirror real intrusions and breaches. This might mean targeting production environments instead of test systems, hitting high value target data stores, or mimicking the long-term access patterns of espionage groups rather than smash-and-grab criminals.
This kind of thinking forces defenders to look deeper. It is no longer enough to block a hash or IP. They have to understand intent, lateral movement patterns, and what behaviour is likely to be benign versus malicious under specific conditions.
Intelligence-led red teaming creates a more adversarial mindset across all areas of the engagement. From infrastructure setup to payload delivery to the operator’s decision-making process, everything is shaped by what real adversaries do.
CTI Illuminates Internal Threats Too
It’s not just about APTs and ransomware groups. CTI also reveals internal risks insider threats, abuse of trusted access, poor role separation, or high-value misconfigurations. These are often harder to detect, but can be just as damaging as an external adversary.
A good red team exercise informed by targeted threat intelligence might simulate an insider selling access or using legitimate access to further access to areas like source code or supply chain.
Having the knowledge as to what tools are used by insider threats typically allows an organisation to build detections for those things and understand once again where gaps might exist.
Intelligence Isn’t a Static Feed: It’s an Operational Enabler
CTI is not static. It is not just another PDF or a feed of indicators to be piped into a SIEM. When embedded properly, it becomes an operational component that informs how offensive operations are planned and executed.
This is where offensive threat intelligence shows its true value.
Use it to build infrastructure that reflects real-world attacker setups, from domain names and TLS configurations to how payloads are staged and delivered. Study threat actor mistakes and build your operational security models to avoid them and adapt. Understand how adversaries pivot, and apply those lessons to test whether your client’s controls are doing anything meaningful in response.
CTI helps transform a red team from a group running tools to a team acting like adversaries. It sets the tone for realistic engagements that provide far more than a list of vulnerabilities.
Final Thoughts
CTI sharpens our ability to think like adversaries and, more importantly, to operate like them in a controlled, repeatable, and measurable manner. When paired with grounded tradecraft, that mindset enables red teams to deliver real value not just by proving something is exploitable, but by demonstrating how a genuine threat actor would approach it, why they would target it, and how long they might remain undetected.
Ultimately, it is not just about knowing the threats. It is about understanding them deeply enough to become them, temporarily, and then helping defenders learn how to beat them.