Image: GeoSn0w
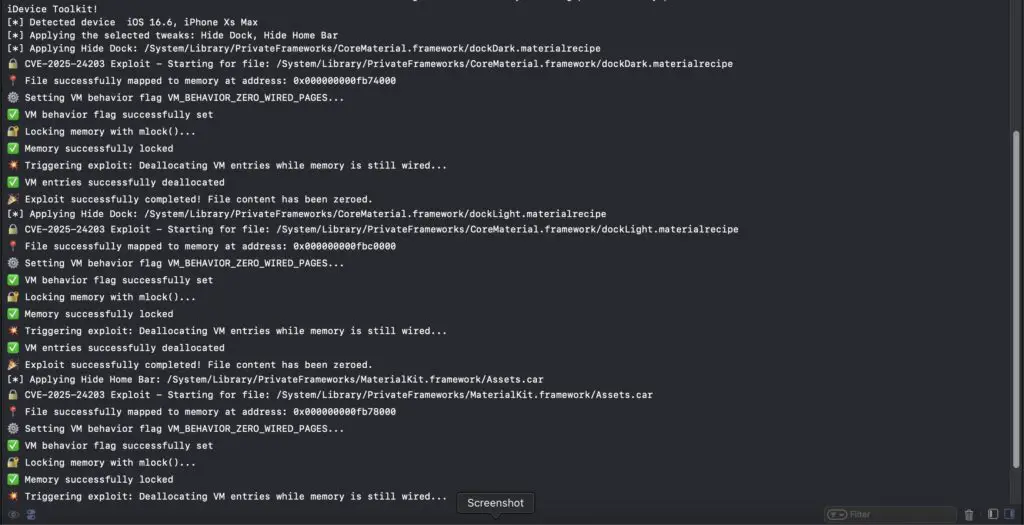
A patched kernel vulnerability, CVE-2025-24203, has attracted great attention in the security community as well as the jailbreak community in the Apple ecosystem. Known in the wild as “dirtyZero” or “mdc0”, this vulnerability allows apps to modify protected areas of the file system, enabling a wave of system customizations without needing a jailbreak.
Disclosed by famed Google Project Zero researcher Ian Beer, the exploit has serious implications for iOS and iPadOS versions 16.0–16.7.10, 17.0–17.7.5, and 18.0–18.3.2.
“An app may be able to modify protected parts of the file system. The issue was addressed with improved checks,” Apple wrote in the security content of iPadOS 17.7.6.
The exploit leverages the behavior of VM_BEHAVIOR_ZERO_WIRED_PAGES, a rarely scrutinized flag within Apple’s memory management system. As Beer explains: “The vm_behavior VM_BEHAVIOR_ZERO_WIRED_PAGES can be set by a task on any vm_entry in its map; there are no permission checks. It causes the entry->zero_wired_pages flag to be set..”
This effectively allows a malicious app to zero out pages of memory backing system files — a powerful tool for attackers or system tweakers.
Key details from Beer’s technical write-up:
- Permission checks are missing at multiple stages.
- Pages can be “zeroed” even if they originate from root-owned, read-only files.
- Leveraging mlock() (a user-accessible syscall) bypasses the need for root or host privileges.
- The exploit can target memory regions mapped from vnode pager files — i.e., UBC (Unified Buffer Cache) pages.
Beer tested the Proof of Concept (PoC) on:
- macOS 15.2 (24C101)
- MacBook Pro 13-inch 2019 (Intel)
Apple has patched this vulnerability in:
- iPadOS/iOS 17.7.6
- iPadOS/iOS 18.4
Users running firmware below these versions are vulnerable.
Following in the footsteps of MacDirtyCow, this exploit is already enabling developers to create customization tools — apps that tweak system behavior, change UI elements, and more — all without needing a full jailbreak.
While the exploit is being used by enthusiasts, the ease of access and lack of permission checks also open the door to potential malicious abuse if embedded into rogue applications.