As threat surfaces grow and attack sophistication increases, many security teams face the same dilemma: they want visibility but don’t want vendor lock-in or cloud pricing that scales like ransomware.
A free and open-source security platform with SIEM and XDR-like capabilities, Wazuh is fast becoming the go-to choice for deep host monitoring, compliance frameworks, and a unified dashboard, without sacrificing control.
What is Wazuh?
Wazuh is an open-source platform for security monitoring, log analysis, intrusion detection, file integrity monitoring (FIM), vulnerability assessment, and incident response.
While it began as an OSSEC fork, today it has evolved into a full-featured security analytics platform. It supports:
- Real-time monitoring of Linux, Windows, macOS endpoints
- Detection of malware, rootkits, and file changes
- Threat intelligence ingestion and alert correlation
- Cloud monitoring (AWS, Azure, GCP)
- Compliance automation (PCI, HIPAA, NIST, GDPR)
It’s essentially a modular SIEM + HIDS + compliance suite—without the licensing bill.
Key Features
Host-based Intrusion Detection (HIDS)
Monitors endpoints for unusual behaviour, unauthorised file changes, suspicious binaries, and privilege escalation.
Log Analysis & Event Correlation
Ingests logs from syslog, journald, cloud APIs, and custom apps. Built-in rules identify known attack patterns and suspicious activity.
File Integrity Monitoring
Tracks changes to critical system files, binaries, and configs with support for real-time notifications and baseline comparisons.
Vulnerability Detection
Correlates software versions with OVAL feeds and CVEs to flag known vulnerabilities on endpoints.
Threat Intelligence Integration
Supports STIX/TAXII feeds and third-party threat sources for enrichment and correlation.
Compliance Auditing
Out-of-the-box policy checks for:
- PCI-DSS
- HIPAA
- NIST 800-53
- GDPR
- TSC/ISO 27001
Cloud & Container Support
Monitors Docker, Kubernetes, and public cloud activity, including misconfigurations, policy violations, and unauthorised actions.
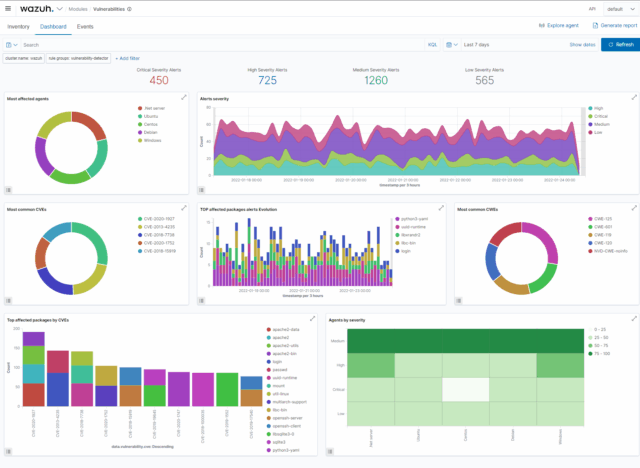
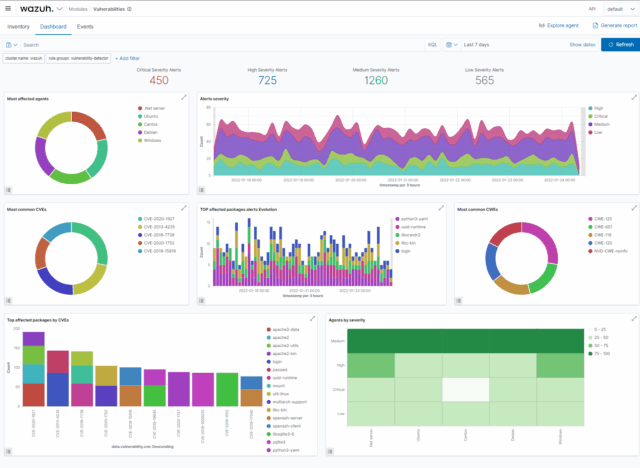
Visual Dashboards
Kibana-based dashboards provide real-time insight into alerts, agent status, attack surface exposure, and compliance drift.
Architecture Overview
Wazuh follows a modular architecture:
- Agents run on endpoints, collecting logs and monitoring behaviour.
- Manager processes data, applies rules, and triggers alerts.
- Indexing Layer (usually Elasticsearch) stores events.
- Dashboard (via Kibana) presents interactive views for triage and investigation.
Optional: Active response modules can trigger scripts, firewall rules, or integrations when specific conditions are met.
Why Use Wazuh?
- Open-source and fully auditable
- Strong documentation and community
- Active development (monthly releases)
- No vendor lock-in
- Lightweight agent, scalable backend
- Built-in compliance and CVE coverage
Final Thoughts
Wazuh is more than a HIDS—it’s a modular, open-source security platform that provides many of the capabilities of commercial XDR tools without the lock-in or price tag.
Suppose you’re looking for deeper endpoint visibility, security telemetry, or compliance monitoring without handing your logs to a third party. In that case, this is one of the most mature and well-supported options.
You can read more about it or download Wazuh here.