Welcome to the second day of our first ever Pwn2OwnBerlin. Yesterday, we awarded $260,000 for some amazing research. Today looks to be even better, with more AI on the line, plus SharePoint and VMware ESXi. As always, we’ll be updating this blog with results as we have them.
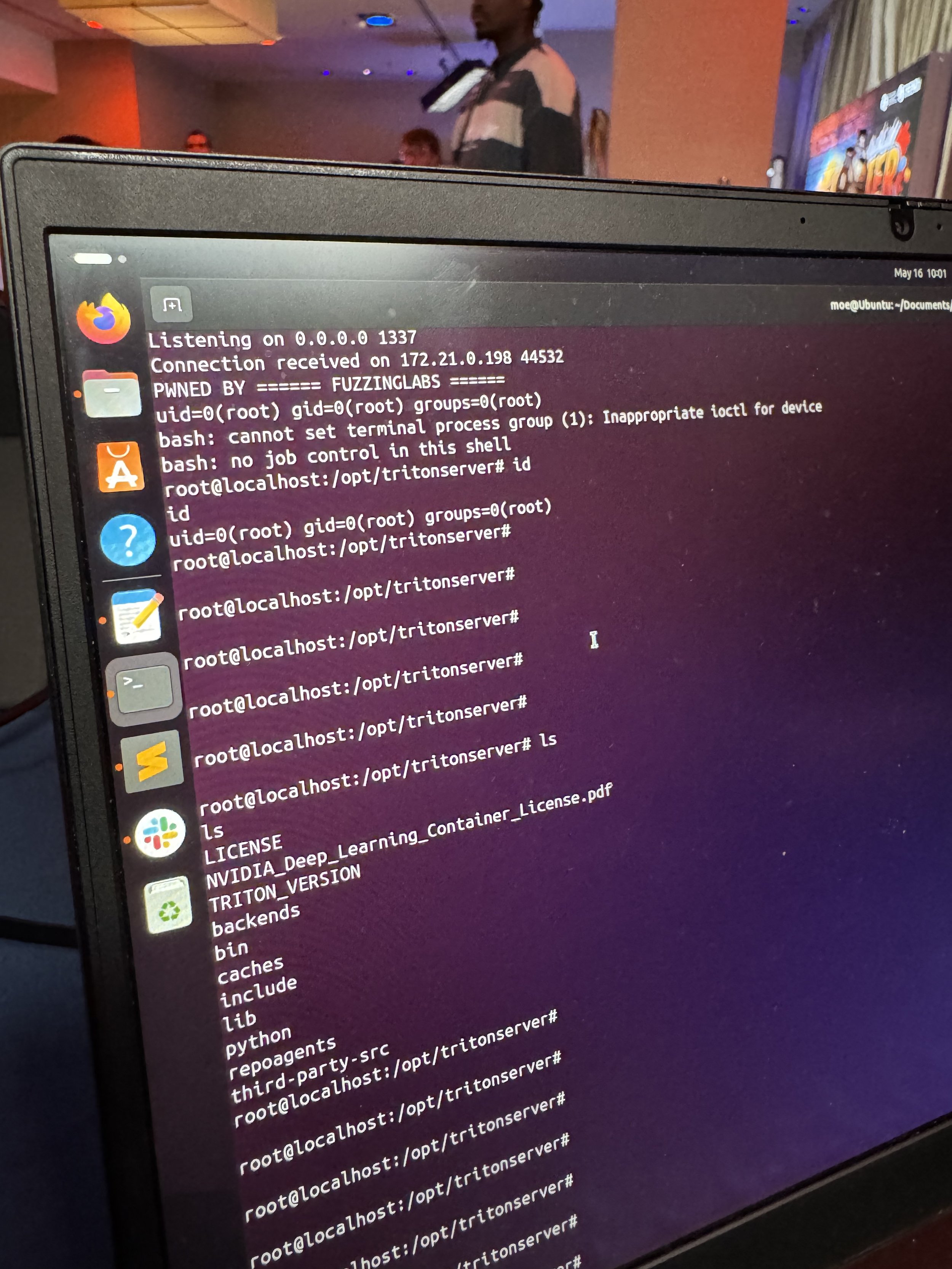
COLLISION - Mohand Acherir & Patrick Ventuzelo (@pat_ventuzelo) of FuzzingLabs (@fuzzinglabs) exploited #NVIDIA Triton, but the exploit they used was known by the vendor (but unpatched). They still earn $15,000 and 1.5 Master of Pwn points.
SUCCESS - Dinh Ho Anh Khoa of Viettel Cyber Security combined an auth bypass and an insecure deserialization bug to exploit Microsoft SharePoint. He earns $100,000 and 10 Master of Pwn points.

SUCCESS - Nguyen Hoang Thach of STARLabs SG used a single integer overflow to exploit #VMware ESXi - a first in Pwn2Own history. He earns $150,000 and 15 Master of Pwn points.

