
朝鲜关联黑客组织WaterPlum利用新型恶意软件OtterCookie针对全球金融机构和金融科技公司展开攻击。该恶意软件自2024年9月起迅速迭代至v4版本,具备跨平台数据窃取能力,并通过检测虚拟环境和窃取加密货币相关凭证提升隐蔽性和攻击效率。 2025-5-10 13:17:11 Author: gbhackers.com(查看原文) 阅读量:7 收藏
A North Korea-linked attack group, known as WaterPlum (also referred to as Famous Chollima or PurpleBravo), has been actively targeting financial institutions, cryptocurrency operators, and FinTech companies globally.
Since 2023, their infamous Contagious Interview campaign has utilized malware such as BeaverTail and InvisibleFerret to infiltrate systems.
However, in September 2024, WaterPlum introduced a sophisticated new malware dubbed “OtterCookie,” which has since undergone rapid updates.
First detailed in a December 2024 blog, OtterCookie has evolved through multiple versions (v1 to v4) with enhanced capabilities, as observed in attacks up to April 2025.
This persistent threat demonstrates the group’s determination to refine their toolkit, targeting a wide range of operating systems including Windows, Linux, and macOS, with a clear focus on data theft and system espionage.
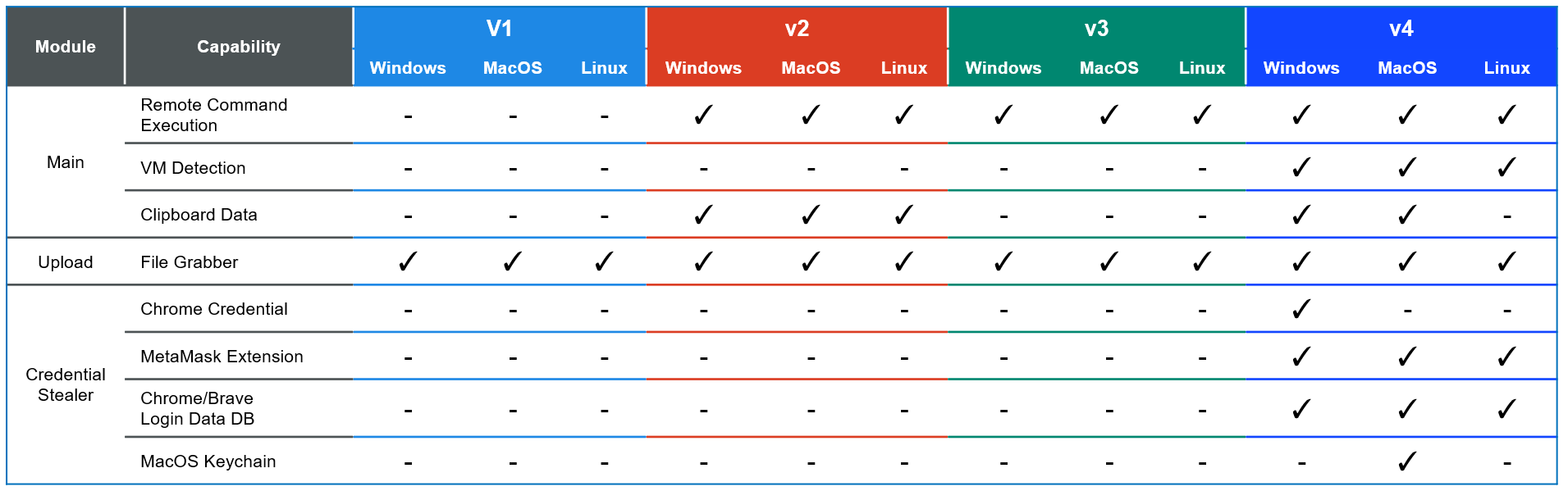
Technical Advancements
According to the Report, OtterCookie’s evolution showcases WaterPlum’s adaptability and technical prowess.
The initial version (v1) was limited to a basic file grabber function, but by the time v4 emerged in April 2025, it had incorporated advanced features such as virtual environment detection to evade sandboxes and multiple stealer modules targeting sensitive data.
In v3, observed in February 2025, the malware featured a main module with legacy functionalities and an upload module for C2 server communication, introducing Windows support to exfiltrate files with specific extensions.
It also hardcoded commands to collect documents, images, and cryptocurrency-related files across other OS environments.
By v4, OtterCookie added two stealer modules-one decrypting Google Chrome login data using DPAPI and storing it for further use, while the other steals encrypted credentials from MetaMask, Chrome, Brave, and macOS systems.
Intriguingly, the inconsistent data processing between these modules suggests development by different coders within the group.
Additionally, clipboard content theft in v4 now relies on native OS commands rather than external libraries, highlighting a shift toward stealthier operations.
These updates reflect WaterPlum’s ongoing efforts to enhance OtterCookie’s versatility and effectiveness, posing a significant challenge to cybersecurity defenses, particularly in regions like Japan where attacks have been noted.
For deeper insights, SOC analysts Motoda and Koike will present detailed findings on OtterCookie’s attack flow and infrastructure at SINCON2025 in Singapore on May 22-23, 2025, in their talk titled “Anti Confiture: An Otter Has A Sweet Tooth.”
Indicators of Compromise (IoCs)
| Type | Value |
|---|---|
| Domain | alchemy-api-v3[.]cloud |
| Domain | chainlink-api-v3[.]cloud |
| Domain | moralis-api-v3[.]cloud |
| Domain | modilus[.]io |
| IP Address | 116[.]202.208.125 |
| IP Address | 65[.]108.122.31 |
| IP Address | 194[.]164.234.151 |
| IP Address | 135[.]181.123.177 |
| IP Address | 188[.]116.26.84 |
| IP Address | 65[.]21.23.63 |
| IP Address | 95[.]216.227.188 |
Setting Up SOC Team? – Download Free Ultimate SIEM Pricing Guide (PDF) For Your SOC Team -> Free Download
Aman Mishra is a Security and privacy Reporter covering various data breach, cyber crime, malware, & vulnerability.
如有侵权请联系:admin#unsafe.sh
.png
)