一种名为“MintsLoader”的新型恶意软件加载器被发现用于传播未公开的“GhostWeaver”后门程序。该恶意软件通过钓鱼邮件和“ClickFix”技术针对金融机构及医疗组织发起攻击。“ClickFix”利用社会工程学诱导用户点击虚假系统提示以绕过安全意识培训。一旦感染,“GhostWeaver”可窃取敏感数据并长期潜伏于系统中。安全专家建议加强应用白名单、禁用Office宏及提升员工安全意识以应对威胁。 2025-5-2 16:17:56 Author: cybersecuritynews.com(查看原文) 阅读量:9 收藏
A sophisticated new malware loader dubbed “MintsLoader” has emerged in the cybersecurity landscape, serving as a delivery mechanism for a previously undocumented backdoor called “GhostWeaver.”
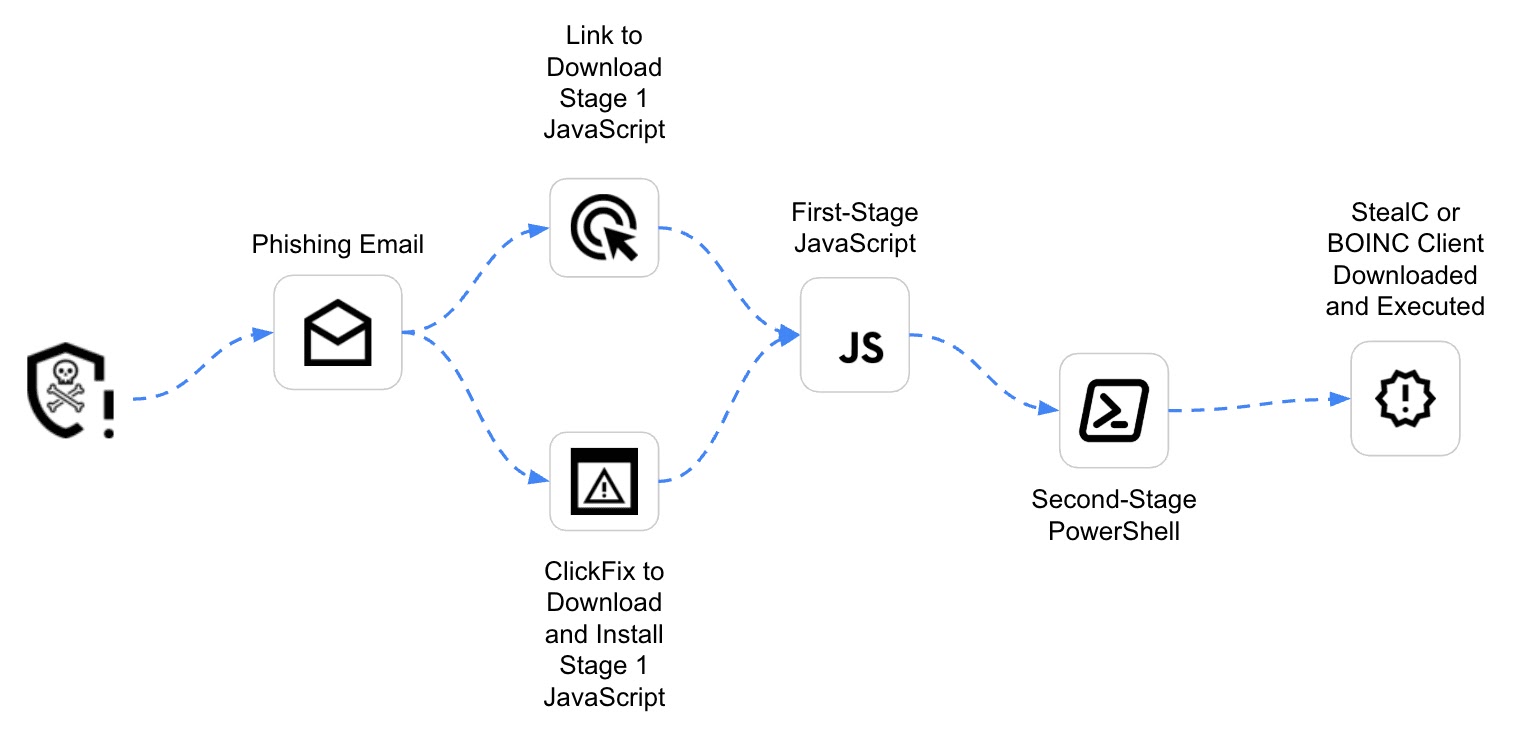
Security researchers have observed a significant spike in targeted attacks against financial institutions and healthcare organizations over the past three weeks, with the malware utilizing a dual-vector approach combining phishing emails and a new technique called “ClickFix” exploitation.
The initial infection vector typically begins with carefully crafted phishing emails containing malicious Microsoft Office documents or PDF files that appear legitimate to the untrained eye.
These documents purportedly contain information about financial transactions, medical records, or urgent corporate communications. Upon opening, victims are prompted to enable macros or click through seemingly harmless notification dialogs that silently trigger the first stage of the attack chain.
Recorded Future analysts identified the malware after observing unusual network traffic patterns from multiple client networks, noting that the attackers leverage a sophisticated social engineering technique they’ve termed “ClickFix.”
This approach exploits human psychology by presenting users with fake error messages that can only be resolved through specific click patterns, effectively bypassing standard security awareness training.
The consequences of infection have proven severe, with GhostWeaver establishing persistent access to compromised systems and exfiltrating sensitive data including credentials, financial records, and intellectual property.
Security teams have reported instances where the malware remained undetected for weeks, suggesting a high level of sophistication in its evasion capabilities and minimal system footprint.
Infection Mechanism Deep Dive
MintsLoader employs a multi-stage infection process that begins with an innocuous-looking VBA macro in Office documents.
.webp)
When executed, it downloads a seemingly benign PowerShell script that contains obfuscated code, as shown below:-
$e = [System.Convert]::FromBase64String('H4sIAAAAAAAAAO1ZW3PiOBZ+n6r5D1q/TNVOGYxtLnYCXV3dDjjBJiEJYJLuzFQVsi3ArWt
LHskG0lP973skGwgkpHu6Z3Znd6qSEB8dHX3nJulcfH3OXugT58Q/OT4+Pj497ShMM87s8zvXjW3G
2hHzTZpwxXh7KVmgpV8kTHlp9oNR8dzX...')
$d = New-Object IO.Compression.GzipStream([IO.MemoryStream][Convert]::FromBase64String($e), [IO.Compression.CompressionMode]::Decompress)
$o = New-Object IO.StreamReader($d, [Text.Encoding]::ASCII)
$s = $o.ReadToEnd()
Invoke-Expression $sThe decompressed code establishes a connection to a command and control server that utilizes domain generation algorithms (DGAs) to avoid blacklisting.
Once connected, MintsLoader downloads and executes the GhostWeaver payload, which immediately begins implementing persistence mechanisms through scheduled tasks and registry modifications.
.webp)
MintsLoader Attack Chain illustrates how the malware creates multiple persistence points to ensure survival across system reboots and attempts at remediation.
A particularly notable feature is its ability to detect and disable endpoint protection products through direct manipulation of Windows Management Instrumentation (WMI) objects.
The ClickFix component represents an evolution in social engineering tactics. When activated, it creates a seemingly legitimate system dialog box that mimics Windows update notifications, security alerts, or software installation prompts.
These dialogs are designed to appear intermittently, training users to click through them without reading. Each interaction provides the malware with additional privileges or executes additional payload components.
These deceptive prompts closely mimic legitimate Windows interfaces, making them particularly effective against users who have become accustomed to dismissing system notifications.
Security researchers recommend organizations implement application whitelisting, disable Office macros, maintain up-to-date endpoint protection, and conduct specific awareness training focused on identifying these new social engineering techniques.
Indicators of compromise including file hashes and network signatures have been published to assist security teams in detecting and mitigating this emerging threat.
Are you from the SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
如有侵权请联系:admin#unsafe.sh

.png
)