渗透测试是一种主动网络安全技术,通过模拟真实攻击发现并修复漏洞,比传统扫描更深入,验证实际风险,适用于网络、Web应用、无线、社会工程和云环境等类型,使用工具如Nmap和Metasploit进行侦察、枚举、利用和后利用阶段,帮助企业满足合规要求并提升安全性. 2025-4-30 15:40:25 Author: horizon3.ai(查看原文) 阅读量:8 收藏
Horizon3.ai | April 30, 2025 | Blogs
Pentesting, short for penetration testing, is a proactive cybersecurity technique where ethical hackers simulate real-world cyberattacks to discover and fix security vulnerabilities before threat actors can exploit them. Unlike traditional vulnerability scans, which passively compare software versions against known flaws, pentesting replicates the actual TTPs (tactics, techniques, and procedures) used by today’s most sophisticated adversaries.
At Horizon3.ai, we view pentesting as more than a checkbox. It’s a critical pillar of modern security operations, designed not just to identify vulnerabilities, but to validate which ones truly matter based on real-world exploitability.

Why Is Pentesting Critical?
Cyber threats are advancing at a rapid and relentless pace, and so are the compliance mandates. From ransomware and supply chain attacks to insider threats and zero-days, the risks have never been greater. Penetration testing helps organizations:
- Find weaknesses before attackers do
- Validate security controls against real attack paths
- Meet compliance requirements like PCI-DSS, HIPAA, GDPR, NIS2, and DORA
- Prioritize remediation based on actual impact, not theoretical risk
For example, the NIS 2 Directive and DORA both require continuous risk assessments, pushing pentesting from a security best practice to a regulatory mandate. Without this level of validation, organizations risk flying blind and assuming they’re secure while exploitable gaps remain.
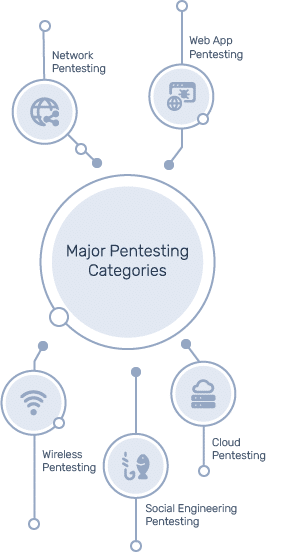
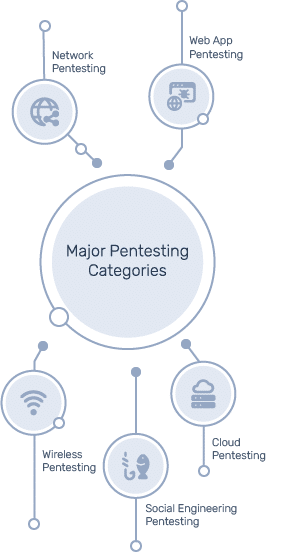
Types of Pentesting: One Size Doesn’t Fit All
Effective pentesting adapts to the attack surface. Here are the major categories:
- Network Pentesting: Targets internal and external networks to uncover misconfigurations, unpatched systems, and weak protocols.
- Web Application Pentesting: Identifies flaws like SQL injection, XSS, and broken authentication in web apps.
- Wireless Pentesting: Evaluates Wi-Fi networks for weak encryption and rogue access points.
- Social Engineering Pentesting: Simulates phishing, pretexting, and impersonation attacks to test human vulnerabilities.
- Cloud Pentesting: Focuses on environments like AWS, Azure, and GCP to uncover IAM misconfigurations, exposed storage, and permission issues.
Each type simulates realistic attack scenarios tailored to your unique environment, because attackers don’t use templates, and neither should your tests.
How Pentesting Works: The Methodology Behind the Mission
A thorough penetration test follows a structured methodology to simulate and validate attacks step-by-step:
1. Reconnaissance
Gather intelligence using open-source data and scanning tools like Nmap.
2. Enumeration & Scanning
Map the attack surface; open ports, services, domains.
3. Exploitation
Attempt to breach systems using known exploits and novel techniques.
4. Post-Exploitation
Assess lateral movement, data access, privilege escalation.
5. Reporting & Remediation Guidance
Provide proof-of-exploit, impact analysis, and fix recommendations.
This isn’t just box-checking, it’s real-world security validation. If a vulnerability can be exploited, your pentest will prove it. Helping your team focus on the issues that actually matter.
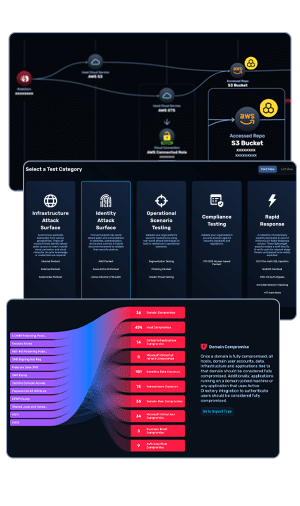
Pentesting Tools of the Trade
Modern pentesters use a blend of automated tools and manual techniques. Here’s a snapshot of what’s in their toolkit:
- Nmap: Network mapping and scanning
- Metasploit: Exploitation framework for known vulnerabilities
- Burp Suite: Web app security testing and fuzzing
- Wireshark: Packet sniffing and network traffic analysis
- SQLmap: SQL injection discovery and exploitation
- John the Ripper: Password cracking
- BloodHound: Active Directory attack path mapping
- Kali Linux & Parrot OS: Comprehensive pentesting OS distributions
NodeZero™, Horizon3.ai’s autonomous pentesting platform, uses many of the same techniques, on autopilot, to help organizations continuously test their environments without needing an army of pentesters.
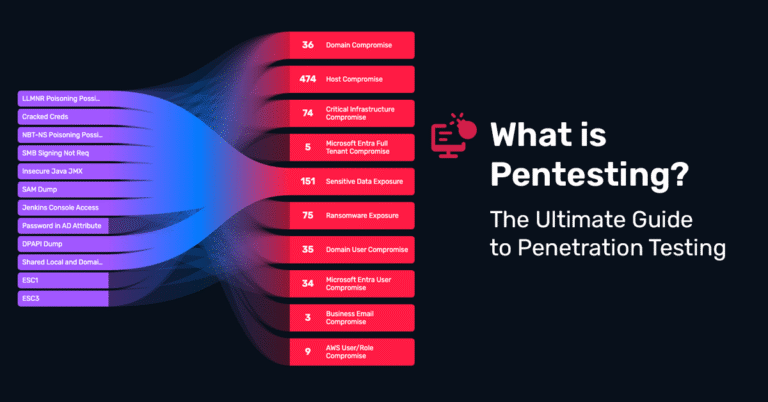
Pentesting vs. Vulnerability Scanning: What’s the Difference?
While both help improve security posture, vulnerability assessments and penetration testing serve very different purposes:
| Vulnerability Assessment | Pentesting |
|---|---|
| Automated Scan | Simulated Attack |
| Identifies Potential Issues | Exploits Real Vulnerabilities |
| No Validation | Validates Actual Risk |
| Low Cost, High Volume | High Value, Targeted Insights |
Pentesting delivers attack path validation, which is critical for cutting through alert fatigue and long vulnerability lists. It tells you what an attacker can do, not just what they might do.
How to Get Started with Pentesting
Interested in becoming a pentester? Here’s your roadmap:
- Learn the fundamentals: Networking, OS internals, scripting (Python, Bash)
- Get hands-on experience: Platforms like Hack The Box, TryHackMe, and Capture The Flag (CTF) challenges
- Master the tools: Metasploit, Burp Suite, Nmap, etc.
- Earn certifications: OSCP, PNPT, CEH, and more
- Build a portfolio: Share write-ups, GitHub projects, and bug bounty reports
Whether you’re red teaming, bug hunting, or automating testing at scale, there’s a place for your skillset in the world of ethical hacking.
Why Pentesting Matters More Than Ever
Pentesting is not just a technical exercise, it’s a strategic investment in cyber resilience. With increasing pressure from attackers and regulators alike, organizations must adopt a continuous, risk-based approach to security validation.
At Horizon3.ai, we help organizations shift from reactive defense to proactive validation. Our autonomous pentesting platform, NodeZero™, empowers security teams to continuously assess and harden their environments, without needing deep offensive expertise.
In an era where assuming breach is the new default, autonomouspentesting is how you fight back.
Learn More
How can NodeZero help you?
Let our experts walk you through a demonstration of NodeZero®, so you can see how to put it to work for your organization.
如有侵权请联系:admin#unsafe.sh