EntraFalcon 是一个 PowerShell 工具,用于枚举和分析 Entra ID 环境中的对象、权限和配置。它帮助识别高权限对象、潜在风险配置,并生成交互式 HTML 报告。该工具适用于安全分析师、渗透测试人员和系统管理员,支持多种认证方式,并无需 Microsoft Graph API 同意。 2025-4-29 07:1:21 Author: blog.compass-security.com(查看原文) 阅读量:14 收藏
TL;DR: PowerShell tool to enumerate Entra ID objects, assignments and identify highly privileged objects or risky configurations.
Entra ID environments can contain thousands of objects – users, groups, service principals, and more – each with unique properties and complex relationships. While manual reviews through the Entra portal might be feasible in smaller environments, they become a tedious task in larger, complex environments.
There are already several free tools available for enumerating Entra ID data. However, some of them typically focus only on dumping data, without offering much support for identifying highly privileged objects or potentially risky object configurations. Other tools do not enumerate certain objects, properties or assignments like Administrative Units, Application app lock configurations, M365 groups or Privileged Identity Management (PIM) eligible assignments.
This is why we built EntraFalcon, a PowerShell tool designed to help security analysts, penetration testers, and sysadmins review Entra ID environments. It highlights potentially risky object configurations and privileged assignments that are often overlooked.
Key Features
- Enumerates Entra ID objects, including:
- Users, Groups (incl. PIM-eligible assignments), App Registrations, Enterprise Apps, Managed Identities, Administrative Units
- Role assignments: Entra roles, Azure roles (active and PIM-eligible)
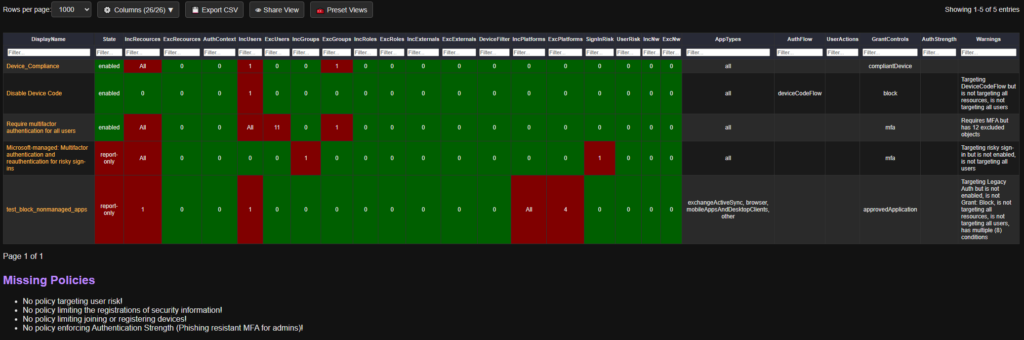
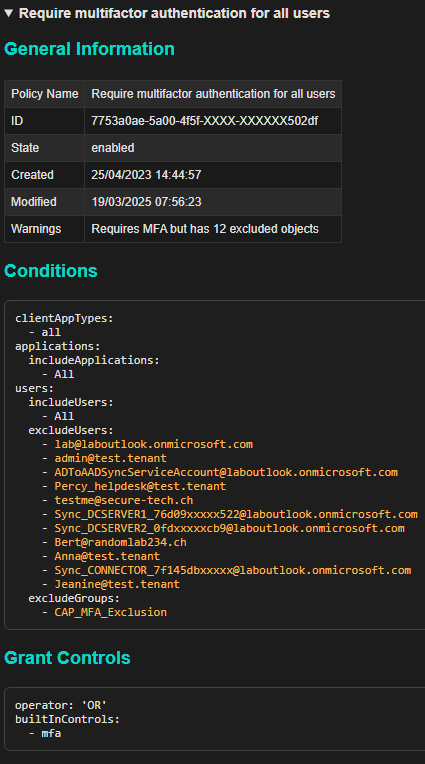
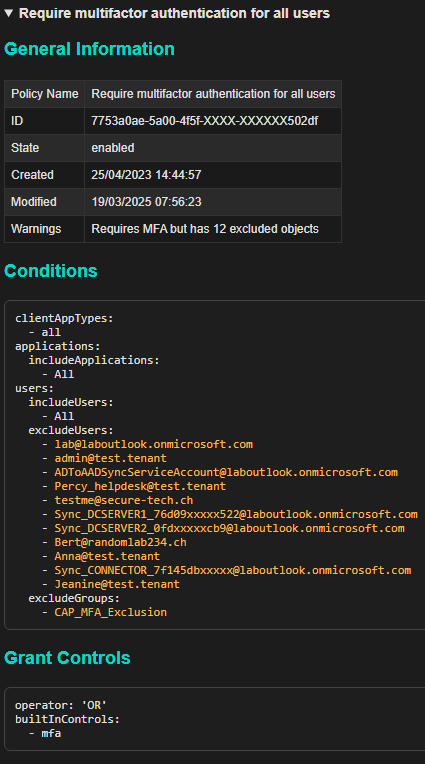
- Conditional Access Policies
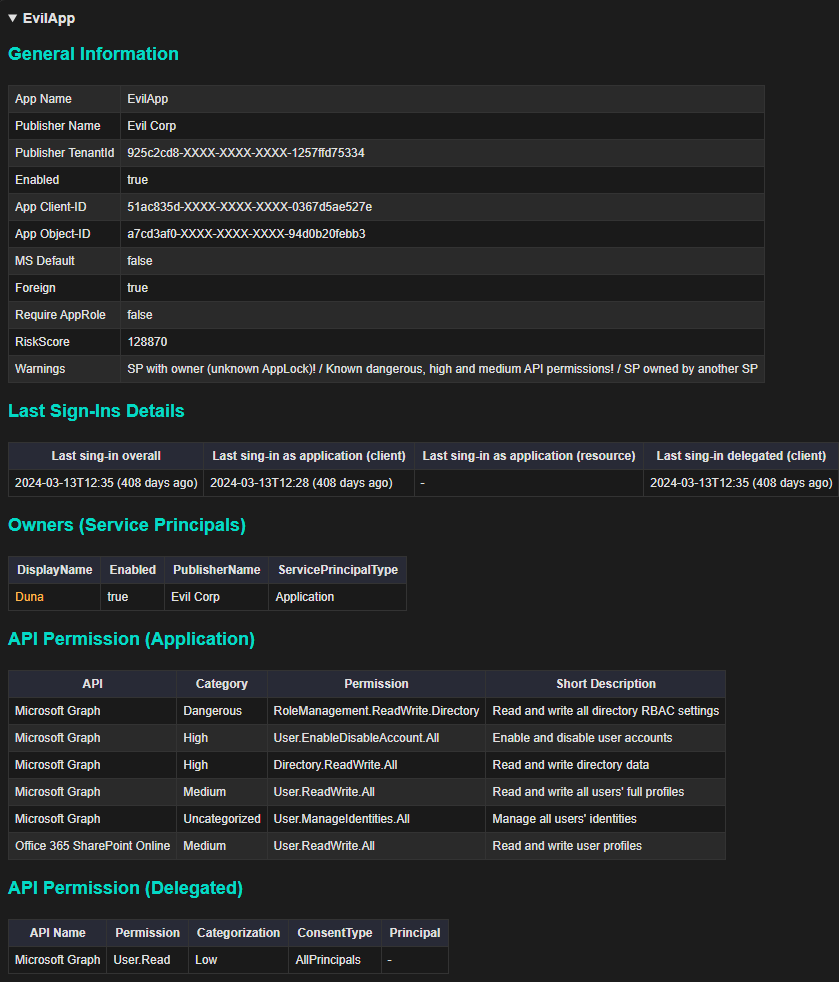
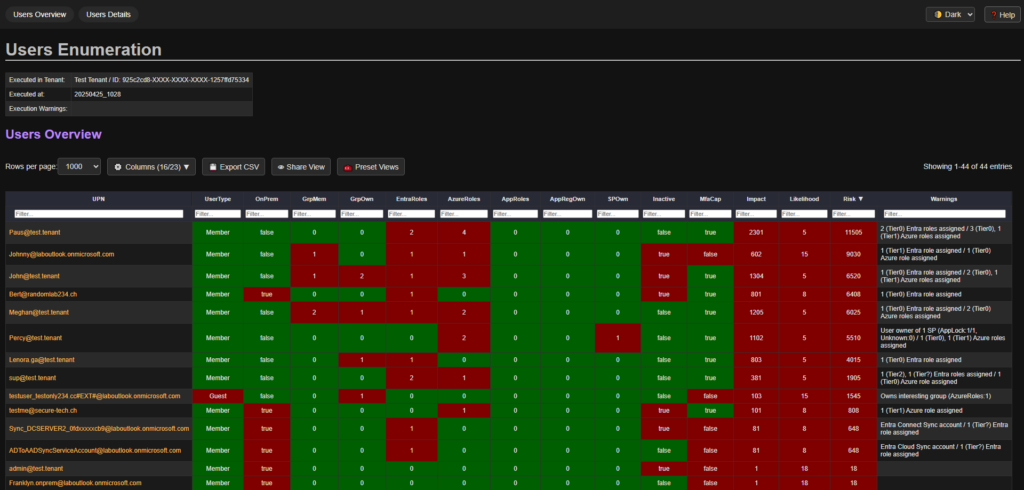
- Applies a simple scoring model to each object, assigning impact, likelihood, and risk scores to help prioritize findings. Interesting configurations or highly elevated privileges are highlighted with warnings
- Generates interactive HTML reports that are sortable, filterable and exportable
- Simple and flexible to use:
- No dependencies: pure PowerShell compatible with both PowerShell 5.1 and 7 (Windows and Linux)
- Built-in authentication supporting different authentication flows
- Bypasses Microsoft Graph API consent – using Microsoft first-party apps with pre-consented API permissions for authentication
Example Findings
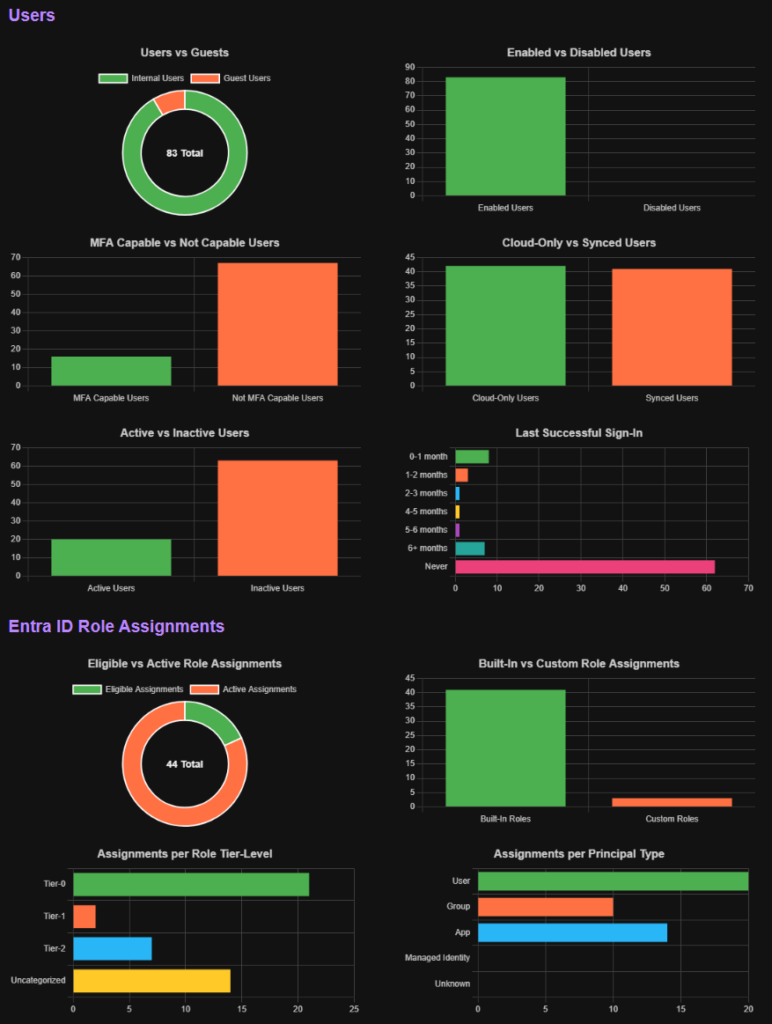
Some examples EntraFalcon helps to identify:
- Users with control over highly privileged groups or applications
- Foreign or internal enterprise applications with excessive permissions (e.g., Microsoft Graph API, Entra/Azure role assignments)
- Users assigned Azure IAM roles directly on resources
- Highly privileged accounts that are synchronized from on-premises directories
- Inactive accounts or users without MFA capability
- Unprotected groups used in sensitive assignments (e.g., Conditional Access exclusions, subscription ownership, or eligible member of a privileged group)
- Missing or misconfigured Conditional Access Policies – such as combining user risk and sign-in risk in a single policy.
Report Samples
Required Permissions
To collect data from Entra ID, the user executing the tool requires at least Global Reader permissions.
To include Azure IAM data (optional but recommended), the Reader role is needed for each relevant Management Group or Subscription.
Limitations
While EntraFalcon helps surface potential issues, manual analysis is still essential to fully understand the impact of each finding. Furthermore, the risk scores provided are intended as indicators, not definitive assessments – they should be reviewed in context as part of a broader investigation.
Get Started
To get started with EntraFalcon, visit our GitHub repository for usage instructions, examples, and additional details.
如有侵权请联系:admin#unsafe.sh