一种新的Android间谍软件Android.Spy.1292.origin伪装成Alpine Quest地图应用传播,目标是俄罗斯军人。该恶意软件通过俄罗斯应用商店分发,可窃取联系人、地理位置和文件信息,并下载额外模块窃取敏感数据。 2025-4-24 05:28:53 Author: securityaffairs.com(查看原文) 阅读量:12 收藏
Android spyware hidden in mapping software targets Russian soldiers

A new Android spyware was discovered in a fake Alpine Quest app, reportedly used by Russian soldiers for war zone planning.
Doctor Web researchers uncovered a new spyware, tracked as Android.Spy.1292.origin, targeting Russian military personnel. The malicious code was hidden in a trojanized Alpine Quest app and spread via Russian Android catalogs. The malware steals contacts, geolocation, and file info, it can also download extra modules to exfiltrate stored data when instructed.
“Alpine Quest is topographic software that allows different maps to be used both in online and offline mode. It is popular among athletes, travelers, and hunters but also widely used by Russian military personnel in the Special Military Operation zone—and this is what the malware campaign organizers decided to exploit.” reads the report published by Doctor Web. Threat actors embedded Android.Spy.1292.origin into one of the older Alpine Quest app versions and distributed the trojanized variant under the guise of a freely available version of Alpine Quest Pro, a program with advanced functionality.”
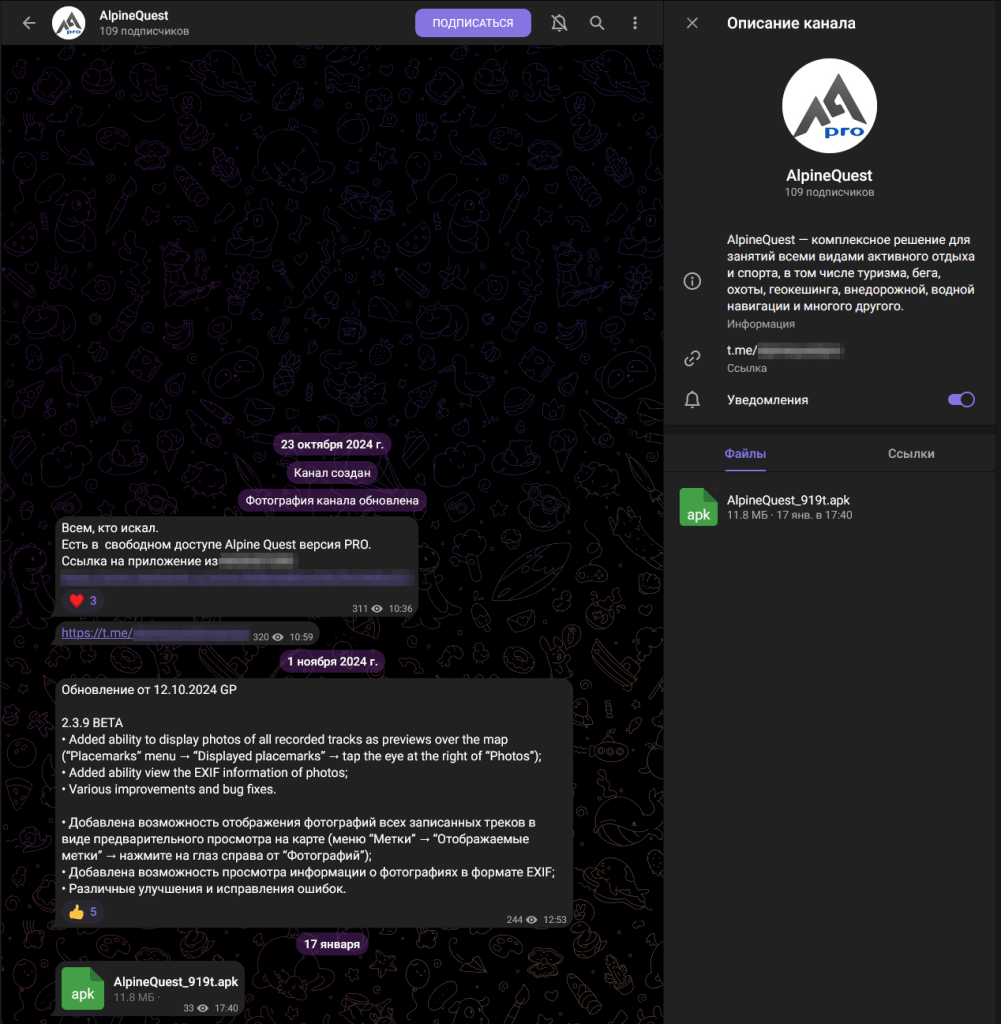
Threat actors set up a fake Telegram channel to distribute the trojanized Alpine Quest app. They shared a link to download the app from a Russian app catalog and later used the same channel to push a malicious “update.”.”
Android.Spy.1292.origin is embedded within a genuine copy of the Alpine Quest app, making it appear and function like the original, to avoid detection. Each time the app is launched, the trojan silently gathers and transmits data such as the user’s phone number, accounts, contact list, current date, geolocation, stored file details, and the app version to a command-and-control server. Simultaneously, it shares some of this data, such as updated geolocation, directly with the attackers’ Telegram bot whenever the device’s location changes.
Once the trojan gathers file information, attackers can instruct it to download and run extra modules to steal specific data. The threat actors behind the malicious app appear interested in confidential documents shared through Telegram and WhatsApp and the locLog file generated by Alpine Quest. This enables Android.Spy.1292.origin to track user locations and exfiltrate sensitive files. Its modular design also allows it to expand its capabilities and perform a broader range of malicious activities.
“As a result, Android.Spy.1292.origin not only allows user locations to be monitored but also confidential files to be hijacked. In addition, its functionality can be expanded via the download of new modules, which allows it to then execute a wider spectrum of malicious tasks.” concludes the report.
The researchers recommend downloading Android apps only from trusted sources like official app stores, avoiding Telegram channels and shady sites, especially those offering free versions of paid apps. Users should also verify app distributors, as attackers often impersonate legitimate developers with similar names and logos.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Android spyware)
如有侵权请联系:admin#unsafe.sh
