CVE-2025-32433
Erlang/OTP旧版本存在未认证远程代码执行漏洞,攻击者可通过SSH协议缺陷远程执行代码。已修复于特定版本,并建议更新或禁用SSH服务器以缓解风险。 2025-4-21 11:20:37 Author: horizon3.ai(查看原文) 阅读量:49 收藏
Erlang/OTP旧版本存在未认证远程代码执行漏洞,攻击者可通过SSH协议缺陷远程执行代码。已修复于特定版本,并建议更新或禁用SSH服务器以缓解风险。 2025-4-21 11:20:37 Author: horizon3.ai(查看原文) 阅读量:49 收藏
Full RCE Vulnerability in Erlang/OTP
A security vulnerability exists in Erlang/OTP prior to versions OTP-27.3.3, OTP-26.2.5.11, and OTP-25.3.2.20, where a SSH server may allow an attacker to perform unauthenticated remote code execution (RCE). By exploiting a flaw in SSH protocol message handling, a malicious actor could gain unauthorized access to affected systems and execute arbitrary commands without valid credentials.
This issue is patched in versions OTP-27.3.3, OTP-26.2.5.11, and OTP-25.3.2.20.
Mitigations
- Update to OTP-27.3.3, OTP-26.2.5.11, or OTP-25.3.2.20.
- Disable the SSH server if not required.
- Use firewall rules to restrict access to the SSH server.
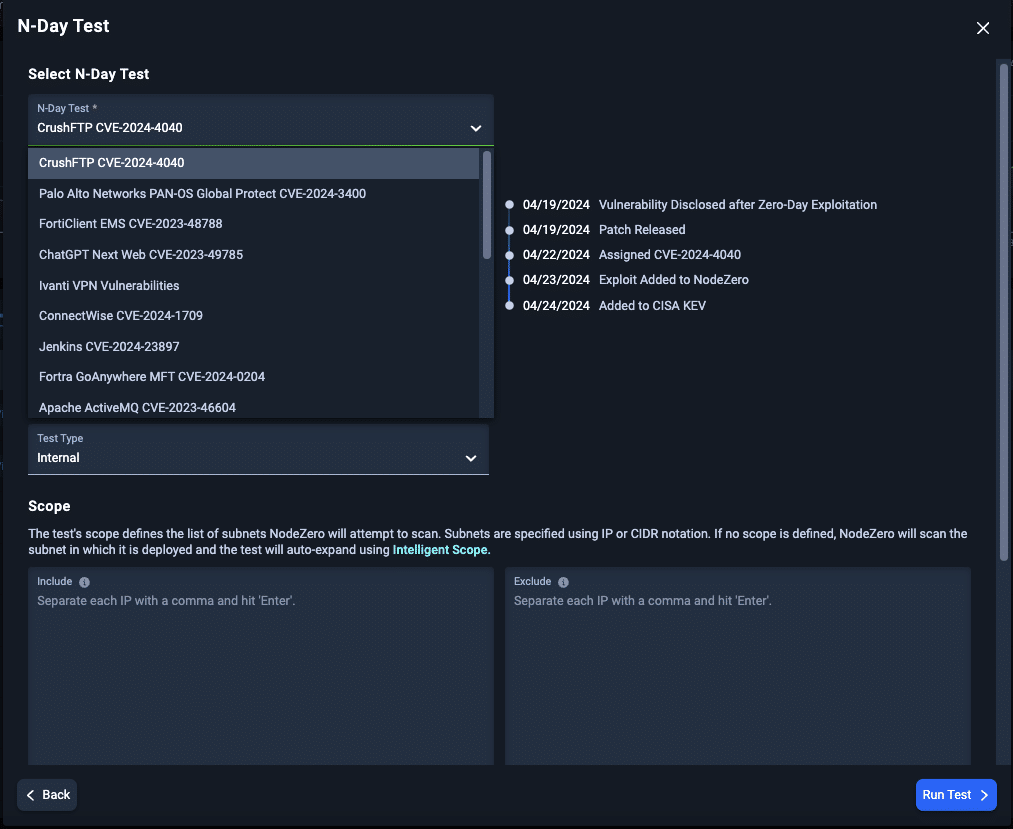
Rapid Response N-Day Testing
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
文章来源: https://horizon3.ai/attack-research/vulnerabilities/cve-2025-32433/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
