When our CEO received an invitation to appear on “Bloomberg Crypto,” he immediately recognized the hallmarks of a sophisticated social engineering campaign. What appeared to be a legitimate media opportunity was, in fact, the latest operation by ELUSIVE COMET—a threat actor responsible for millions in cryptocurrency theft through carefully constructed social engineering attacks.
This post details our encounter with ELUSIVE COMET, explains their attack methodology targeting the Zoom remote control feature, and provides concrete defensive measures organizations can implement to protect themselves.
Our encounter with ELUSIVE COMET
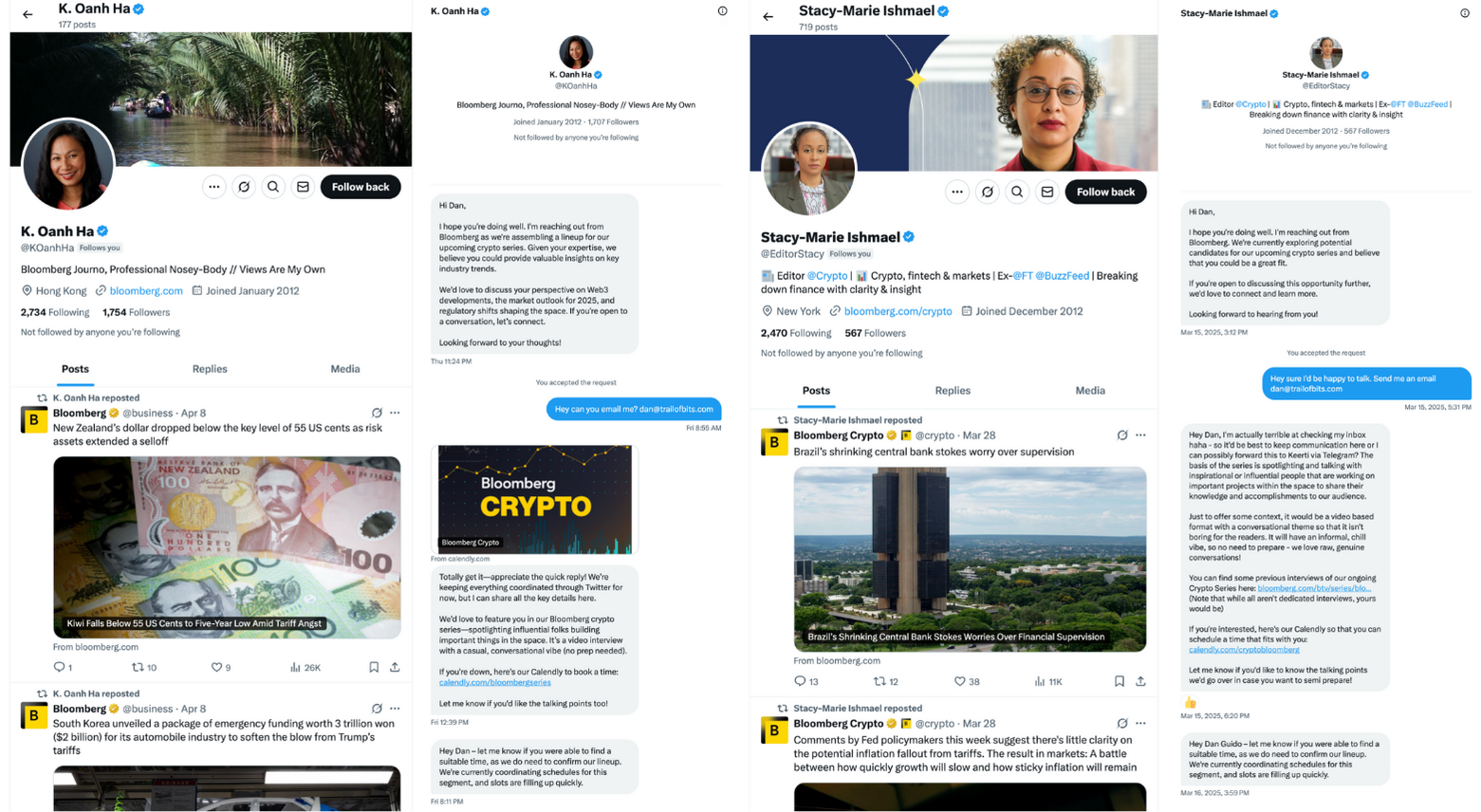
Two separate Twitter accounts approached our CEO with invitations to participate in a “Bloomberg Crypto” series—a scenario that immediately raised red flags. The attackers refused to communicate via email and directed scheduling through Calendly pages that clearly weren’t official Bloomberg properties. These operational anomalies, rather than technical indicators, revealed the attack for what it was.
The ELUSIVE COMET methodology mirrors the techniques behind the recent $1.5 billion Bybit hack in February, where attackers manipulated legitimate workflows rather than exploiting code vulnerabilities. This reinforces our perspective that we’ve entered the era of operational security failures, where human-centric attacks now pose greater risks than technical vulnerabilities.
New ELUSIVE COMET IoCs
In addition to the IoCs previously published in SEAL’s advisory on ELUSIVE COMET, we have identified new accounts associated with this threat actor’s infrastructure:
X: @KOanhHa
Email: bloombergconferences[@]gmail.com
Zoom URL: https://us06web[.]zoom[.]us/j/84525670750
Calendly URL: calendly[.]com/bloombergseries
Calendly URL: calendly[.]com/cryptobloomberg
Organizations should update their monitoring systems and blocklists to include these new indicators.
Understanding Zoom’s remote control feature
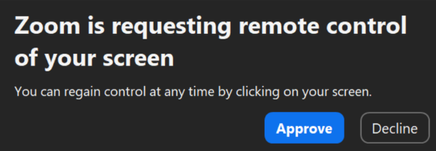
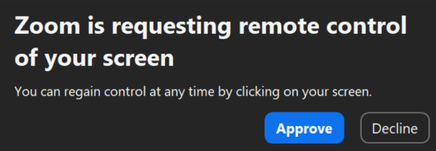
ELUSIVE COMET’s primary attack vector leverages Zoom’s remote control feature—a legitimate function that allows meeting participants to control another user’s computer with permission. When a participant requests remote control, the dialog simply states “$PARTICIPANT is requesting remote control of your screen.”
The attack exploits this feature through a simple yet effective social engineering trick:
- The attacker schedules a seemingly legitimate business call.
- During screen sharing, they request remote control access.
- They change their display name to “Zoom” to make the request appear as a system notification.
- If granted access, they can install malware, exfiltrate data, or conduct cryptocurrency theft.

What makes this attack particularly dangerous is the permission dialog’s similarity to other harmless Zoom notifications. Users habituated to clicking “Approve” on Zoom prompts may grant complete control of their computer without realizing the implications.
Why this attack succeeds (even against security professionals)
The ELUSIVE COMET campaign succeeds through a sophisticated blend of social proof, time pressure, and interface manipulation that exploits normal business workflows:
- Legitimate context: The attack occurs during what appears to be a normal business interaction.
- Interface ambiguity: The permission dialog doesn’t clearly communicate the security implications.
- Habit exploitation: Users accustomed to approving Zoom prompts may act automatically.
- Attention division: The victim is focused on a professional conversation, not security analysis.
This approach targets operational security boundaries rather than technical vulnerabilities—precisely the shift we predicted when discussing the $1.5 billion Bybit hack.
Trail of Bits’ defense posture
Our encounter with ELUSIVE COMET reinforces our belief in defense-in-depth strategies that address both technical and operational security domains:
- Endpoint protection: CrowdStrike Falcon EDR on all systems configured for high-sensitivity environments. As the industry-leading endpoint detection and response platform, CrowdStrike’s heightened sensitivity settings allow us to detect and block sophisticated attacks that might evade traditional antivirus. The behavioral analysis engine can identify suspicious activity—like unauthorized attempts to access system accessibility features—even when the malware is previously unknown.
- OS security: Mandatory latest macOS versions company-wide (major updates within a month of stable point releases). Apple consistently narrows attack surfaces with each major OS release, introducing entire frameworks that mitigate classes of vulnerabilities rather than just patching individual bugs. By standardizing on the latest major release (after point-one stability updates), we ensure our systems benefit from Apple’s most current security architecture.
- Authentication hardening: Security key authentication for all Google properties. Hardware security keys implement cryptographic protocols that bind authentication to specific domains, making them phishing-resistant. Even if an employee attempts to authenticate to a convincing phishing site, the security key will refuse to complete the authentication process—technology that would have prevented many recent supply chain compromises.
- Password management: Company-wide 1Password deployment with domain matching to prevent phishing. When credentials must be manually entered into a website, 1Password will only auto-fill them on the correct domain. This creates a moment of friction when employees are directed to suspicious domains, forcing them to consciously copy-paste credentials—a security speed bump that often triggers risk awareness.
- Communication platform choices: Primary use of Google Meet over Zoom due to its browser-based security model. Browser-based communication tools inherit the security model of the browser itself, limiting their access to system resources. Chrome’s sandbox prevents web applications from accessing local system resources without explicit permission, creating a more controlled execution environment than installed applications can provide.
- Restrictive application controls: When Zoom is required, it’s wrapped with additional security controls and routinely removed from systems. Through threat intelligence and our own security research, we identify high-risk applications that are frequently abused in attacks. We apply additional controls to these “tallest blades of grass” to limit their access to system resources and regularly remove them when not actively needed.
Most critically, our security team has identified the Zoom remote control feature as an unnecessary risk and deployed technical controls to prevent it from functioning on our systems. By specifically targeting the accessibility permissions that enable remote control, we close the attack vector that ELUSIVE COMET exploits without disrupting legitimate videoconferencing functionality.
A layered defense approach
To protect your organization from this attack vector, we recommend using our tools to implement multiple layers of protection:
| Script | Purpose | Execution Frequency | Target Scope |
|---|---|---|---|
create_zoom_pppc_profile.bash | Creates system-wide PPPC profiles that prevent accessibility access | Once per computer | All computers |
disable_zoom_accessibility.bash | Actively checks and removes Zoom accessibility permissions | Every 15 minutes | Computers with Zoom installed |
uninstall_zoom.bash | Completely removes removal of Zoom from fleet computers | Weekly | Computers with Zoom installed |
Index of mitigation tools
System-wide protection with PPPC profiles
Privacy Preferences Policy Control (PPPC) profiles provide the strongest protection by preventing Zoom from requesting or receiving accessibility permissions at the macOS system level. This directly addresses the vulnerability because Zoom’s remote control feature requires accessibility permissions to function—without these permissions, the remote control capability is completely disabled, neutralizing ELUSIVE COMET’s primary attack vector.
PPPC profiles offer several security advantages:
- Apply to all users on a system, including new user accounts
- Cannot be removed by regular users once installed
- Enforce organizational security controls regardless of user preferences
- Specifically target only the official Zoom application using code signature verification
When properly configured, these profiles check both the bundle identifier and certificate chain, making it extremely difficult for malicious actors to circumvent these restrictions with look-alike applications. This approach leverages macOS’s robust application control mechanisms to create an environment where social engineering attempts simply cannot succeed.
Active defense with TCC database monitoring
While PPPC profiles provide proactive protection, organizations could also benefit from implementing reactive measures. Accessibility permissions are controlled by Apple’s Transparency Consent and Control (TCC) framework which can be controlled by the disable_zoom_accessibility.bash script to deliver these security advantages:
- Continuous remediation: Regularly revokes any accessibility permissions that might have been granted to Zoom
- Defense in depth: Provides redundant protection even if other controls are circumvented
- State reset: Returns the system to a known-good state by directly modifying the TCC database
- Attack surface reduction: Minimizes the window of opportunity for exploitation attempts
When run periodically, this script resets the TCC database permissions for Zoom to a known safe state, mitigating several potential bypass vectors. It catches grandfathered permissions granted before profile deployment, reverses direct database manipulations by privileged users, and neutralizes permission resets from application reinstallation. Each execution creates security telemetry indicating potential attack attempts as any permissions removed during runtime indicate potential attack attempts or policy violations.
Maximum protection by purging Zoom
For high-security environments or organizations handling cryptocurrency, the most direct approach is to completely remove Zoom from systems. This elimination strategy operates on a simple principle: software that isn’t installed can’t be exploited. For organizations handling particularly sensitive data or cryptocurrency transactions, the risk reduction from eliminating the Zoom client entirely often outweighs the minor inconvenience of using browser-based alternatives:
- Complete attack vector elimination: Removes the application that ELUSIVE COMET relies on
- Digital hygiene: Ensures no remnant components remain that could be leveraged in an attack
- Comprehensive cleanup: Removes all potential persistence mechanisms including preferences and cached data
- Zero surface area: Guarantees that users cannot accidentally expose themselves to this risk
When combined with a policy encouraging browser-based meeting participation, purging zoom with uninstall_zoom.bash provides the strongest protection against ELUSIVE COMET’s attack methodology.
Additional security recommendations
Beyond the specific Zoom mitigations, we recommend these additional defensive measures:
- Train users to recognize social engineering tactics in video calls: While this is primarily a technical issue with Zoom’s permissions model, user awareness still matters. Train staff to recognize unusual permission requests during video calls—particularly those requesting system control. Create a simple mental model for employees: “No legitimate business process should ever require giving someone else control of your computer.” Establish a protocol requiring secondary verification (like a phone call to IT) before granting remote control to anyone, even seemingly trusted contacts.
- Implement comprehensive IoC monitoring across communication channels: Deploy email security tools like Material Security and Sublime Security that enable searching your entire organization for communications from known threat actors. When new indicators are published (like those in this post), these tools allow security teams to quickly identify if anyone in the organization has been targeted. Despite these attacks primarily occurring on social media, the attackers eventually need to send calendar invites via email—creating a detectable footprint if you have the right monitoring tools.
- Create explicit policies for media appearances and external communications: At Trail of Bits, all media appearances follow an established process involving multiple stakeholders to develop messaging and talking points. When our CEO was approached via Twitter DM, his immediate response was to direct communication to email—following our standard procedure for external engagements. Establish clear verification processes requiring communication through official channels (corporate email) for any external engagement. Train staff that legitimate media organizations respect and follow these processes.
- Deploy email boundary controls as brand protection: While this specific ELUSIVE COMET campaign didn’t use email spoofing, properly configured DMARC, SPF, and DKIM prevent attackers from directly impersonating your domain in future campaigns. This limits an attacker’s ability to exploit your organization’s brand when targeting others. Bloomberg’s properly implemented email security likely forced ELUSIVE COMET to use non-Bloomberg domains (gmail.com accounts)—a red flag that helped our CEO identify the attack immediately.
- Cultivate a rapid information sharing culture: When our CEO identified this attack, he immediately posted a notification to the company-wide Slack channel, alerting everyone to the ongoing campaign. Create low-friction reporting channels that make it easy for employees to share suspicious interactions. Establish a “no penalty” culture for security reporting—reward people who report suspicious activity even if it turns out to be legitimate. Time is critical in these situations; a culture of rapid, blame-free reporting can prevent multiple victims within your organization.
Building resilient security against human-centered attacks
The ELUSIVE COMET campaign represents the continuing evolution of threats targeting operational security rather than technical vulnerabilities. As we’ve entered the era of operational security failures, organizations must evolve their defensive posture to address these human-centric attack vectors.
By implementing the multilayered defense approach outlined above, organizations can significantly reduce their exposure to this specific attack vector while maintaining business functionality. More importantly, this case study demonstrates the critical importance of combining technical controls with operational security awareness in defending against modern threats.
If your organization handles sensitive data or manages cryptocurrency transactions, our security engineers can help you develop a tailored threat model that addresses both traditional vulnerabilities and operational security boundaries. Contact us to learn more.