
网络钓鱼攻击者采用新策略"精准验证钓鱼",仅在用户输入特定目标邮箱时显示虚假登录页面。此方法通过实时验证确保钓鱼内容仅针对预先筛选的高价值目标展示。研究人员常用假邮箱测试已被绕过,导致检测难度增加。防御需转向行为指纹识别和实时威胁情报关联以应对威胁。 2025-4-9 14:0:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:6 收藏

Phishing actors are employing a new evasion tactic called 'Precision-Validated Phishing' that only shows fake login forms when a user enters an email address that the threat actors specifically targeted.
Unlike traditional mass-targeting phishing, this new method uses real-time email validation to ensure phishing content is shown only to pre-verified, high-value targets.
Although not overly advanced or particularly sophisticated, the new tactic excludes all non-valid targets from the phishing process, thus blocking their visibility into the operation.
Email security firm Cofense, which documented the rise in adoption of this new tactic, noted that it has created a significant practical problem for them.
When researching phishing sites, it is common for researchers to enter fake email addresses or ones under their control to map the credential theft campaign.
However, with this new technique, invalid or test email addresses inputted by researchers now display an error or redirect them to benign sites. This impacts automated security crawlers and sandboxes used in research, reducing detection rates and prolonging the lifespan of phishing operations.
"Cybersecurity teams traditionally rely on controlled phishing analysis by submitting fake credentials to observe attacker behavior and infrastructure," explains Cofense.
"With precisionvalidated phishing, these tactics become ineffective since any unrecognized email is rejected before phishing content is delivered."
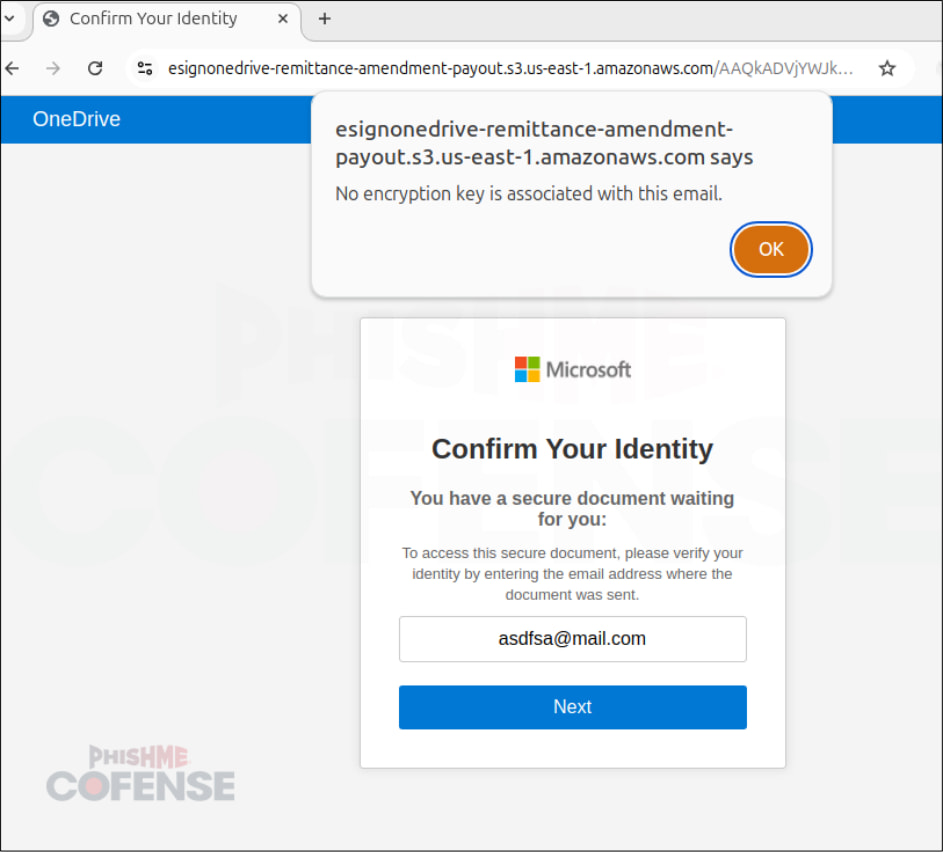
Source: Cofense
According to Cofense, the threat actors use two main techniques to achieve real-time email validation.
The first involves abusing third-party email verification services integrated into the phishing kit, which checks the validity of the victim's address in real time via API calls.
The second method is to deploy custom JavaScript in the phishing page, which pings the attacker's server with the email address victims type on the phishing page to confirm whether it's on the pre-harvested list.
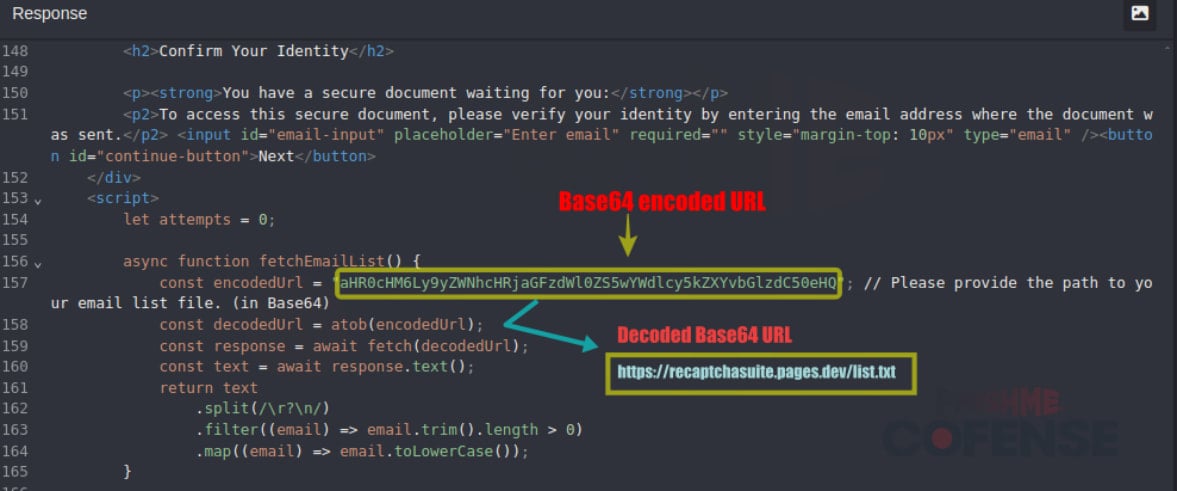
Source: Cofense
If there's no match, the victim is redirected to an innocuous site, like Wikipedia.
Cofense explains that bypassing this by simply entering the email address of the person who reported the phishing attempt to them is often impossible because of usage restrictions imposed by their clients.
Even if they were allowed to use the real target's address, the analysts comment that some campaigns go a step further, sending a validation code or link to the victim's inbox after they enter a valid email on the phishing page.
To proceed with the phishing process, victims need to enter the code they received in their inbox, which is beyond the access of security analysts.
The ramifications of this are serious for email security tools, especially those relying on traditional detection methods, are serious, as they are more likely to fail to alert targets of phishing attempts.
As phishing campaigns adopt dynamic input validation, defenders must adopt new detection strategies that emphasize behavioral fingerprinting and real-time threat intelligence correlation to stay ahead of the threat actors.
如有侵权请联系:admin#unsafe.sh
