CISA等机构呼吁组织和DNS提供商应对"Fast Flux"网络犯罪规避技术。该技术通过快速更换DNS记录隐藏恶意活动来源,常用于指挥控制、钓鱼和恶意软件分发。分为Single Flux(频繁更换IP)和Double Flux(同时更换DNS服务器)两种类型。CISA建议通过分析DNS日志、集成威胁情报等手段检测并缓解此类攻击。 2025-4-3 19:45:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:33 收藏

CISA, the FBI, the NSA, and international cybersecurity agencies are calling on organizations and DNS providers to mitigate the "Fast Flux" cybercrime evasion technique used by state-sponsored threat actors and ransomware gangs.
Although the technique isn't new, its effectiveness has been documented and proven repeatedly in actual cyberattacks.
How Fast Flux helps with evasion
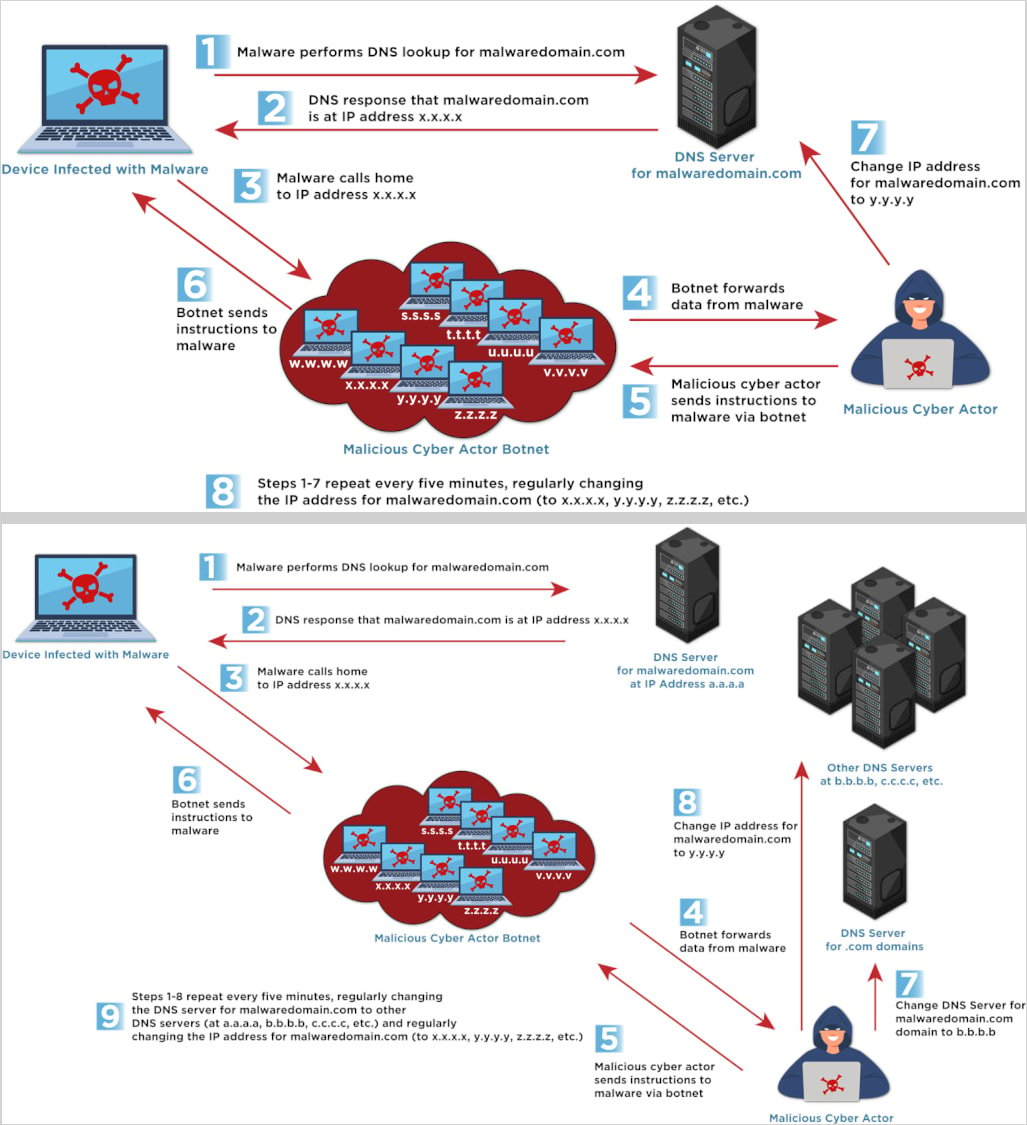
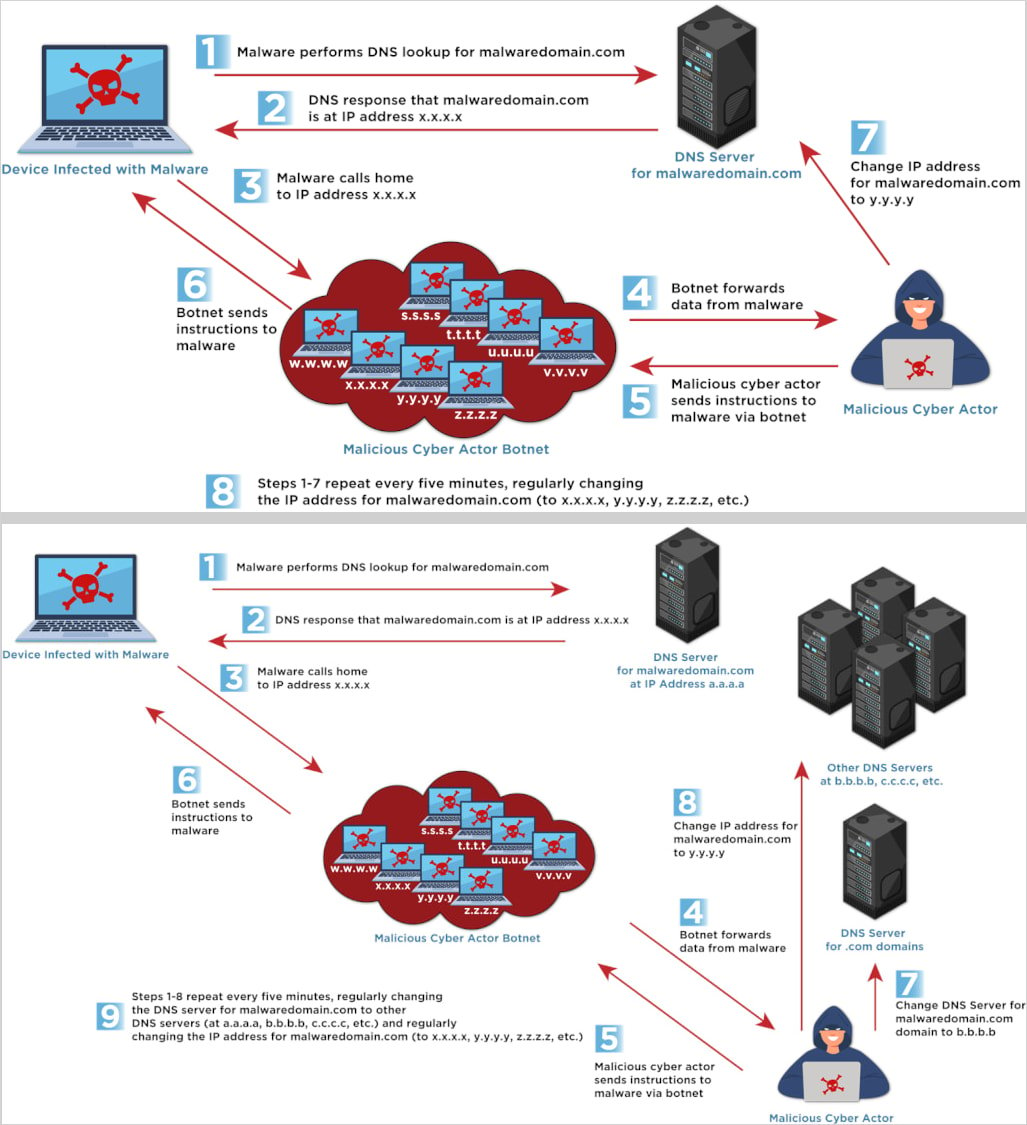
Fast Flux is a DNS technique used for evading detection and maintaining resilient infrastructure used for command and control (C2), phishing, and malware delivery.
It involves rapidly changing DNS records (IP addresses and/or name servers), making it hard for defenders to trace the source of malicious activity and block it.
It is often powered by botnets formed by large networks of compromised systems that act as proxies or relays to facilitate these rapid switches.
CISA's bulletin highlights two main types of the technique, namely Single Flux and Double Flux.
When using Single Flux, attackers will frequently rotate the IP addresses associated with a domain name in DNS responses.
With Double Flux, in addition to rotating IPs for the domain, the DNS name servers themselves also change rapidly, adding an extra layer of obfuscation to make takedown efforts even harder.
Source: CISA
CISA says Fast Flux is widely employed by threat actors of all levels, from low-tier cybercriminals to highly sophisticated nation-state actors.
The agency highlights the cases of Gamaredon, Hive ransomware, Nefilim ransomware, and bulletproof hosting service providers, all using Fast Flux to evade law enforcement and takedown efforts that would disrupt their operations.
CISA recommendations
CISA has listed multiple measures to help detect and stop Fast Flux and mitigate activity facilitated by the evasion technique.
The proposed detection techniques are summarized as follows:
- Analyze DNS logs for frequent IP address rotations, low TTL values, high IP entropy, and geographically inconsistent resolutions.
- Integrate external threat feeds and DNS/IP reputation services into firewalls, SIEMs, and DNS resolvers to flag known fast flux domains and malicious infrastructure.
- Use network flow data and DNS traffic monitoring to detect large volumes of outbound queries or connections to numerous IPs in short periods.
- Identify suspicious domains or emails and cross-reference with DNS anomalies to detect campaigns using Fast Flux to support phishing, malware delivery, or C2 communication.
- Implement organization-specific detection algorithms based on historical DNS behavior and network baselines, improving detection accuracy over generic rules.
For mitigation, CISA recommends using DNS/IP blocklists and firewall rules to block access to Fast Flux infrastructure and, where possible, sinkhole traffic to internal servers for further analysis.
Using reputational scoring for traffic blocking, implementing centralized logging and real-time alerting for DNS anomalies, and participating in information-sharing networks are also encouraged.
如有侵权请联系:admin#unsafe.sh
