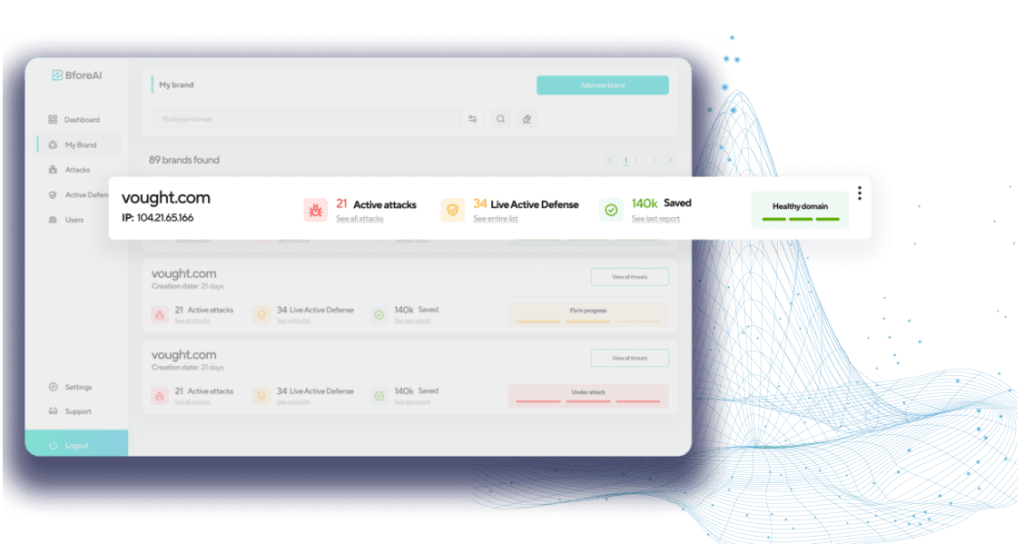
2025年2月21日,Bybit遭受黑客攻击,损失约15亿美元数字资产。朝鲜Lazarus集团被指为幕后黑手。随后出现大量仿冒Bybit的钓鱼网站,利用用户恐慌情绪诱导转账或泄露信息。研究团队发现596个可疑域名中20%为恶意行为。 2025-4-3 07:1:35 Author: bfore.ai(查看原文) 阅读量:28 收藏
Bybit Opportunists: Malicious Infrastructure Attacks Report

On February 21, 2025, global news outlets reported news related to the high-profile Bybit Hack. As one of the biggest thefts the cryptocurrency industry has ever seen, the hack has been blamed for a loss of at least 1.5 billion USD in digital assets. While the specific criminal activity accounted for the hack is being attributed to a North Korean advanced persistent threat (APT), separate cybercriminal groups are using the event to level various phishing campaigns targeting Bybit users. These campaigns, though unrelated to the original breach, exploit the incident to defraud victims and have a common target– Bybit.
The threat research team at BforeAI collected 596 suspicious domains originating from at least 13 different countries in the three weeks following the Bybit breach announcement. The domains reveal a range of methods employed to siphon cryptocurrency assets by targeting Bybit users. Out of the almost 600 suspicious domains, 119 (20%) were confirmed by BforeAI to be malicious actions.
On February 21, 2025, a North Korean state-sponsored APT called the Lazarus Group stole cryptocurrency from the Ethereum coin wallet, followed by a transfer to unidentified accounts. There are claims that these stolen funds are being used to fund North Korea’s military regime.
Threats revolving around the Bybit incident
Cybercriminals leveraged the breach announcement made on the official Bybit website to exploit the sudden surge in withdrawal requests. This activation was the main theme exploited by the cybercriminals in the first week following the announcement.
Statistical analysis of the domains
(A) TLD Distribution
- The domains analyzed use a variety of top-level domains (TLDs), with the most common being:
- .com (33 instances)
- .net (7 instances)
- .dev (6 instances)
- .pages (6 instances)
- Others: .org, .site, .shop, .info, .xyz, .io, .uk, .help, .biz, .nl, .club, .eco, .win, .store
(B) Bybit is the primary target, with over 43 domains mimicking the exchange, using deceptive variations and subdomains. Bitget also appears as a secondary target, indicating that multiple crypto platforms are being impersonated.
(C) The team observed typosquatted versions of Bybit, with minimal spelling errors. There were also some string patterns combining the targeted crypto platform with keywords such as “refund”, “wallet”, “information”, “check”, “recovery”, etc., reflecting the many possible actions an individual could take following the incident.
(D) There were instances of popular crypto keywords such as “metaconnect”, “mining”, and “airdrop”, as well as the use of free hosting and subdomain registration services such as Netlify, Vercel, and Pages.dev. The use of free hosting services and dynamic subdomains is a widely-used tactic in this dataset. Many phishing pages are hosted on platforms that provide fast, anonymous deployment without requiring domain purchases.
(E) By country, the largest number of domains registered were observed to originate in the United Kingdom (36), followed by the United States (17), Japan (4), Singapore (3), and Iceland (2).
The threat research team documented various websites designed to resemble Bybit funds recovery. The websites highlighted the term “unauthorized activities”, creating a sense of urgency around the recent incident and the fear of financial loss to psychologically trigger a victim to take immediate action without considering the source.
Figure 1: Phishing campaign offering Bybit funds recovery to affected victims
Another website managed to mimic the “Help Center” theme of the official website, anticipating it would be a highly searched resource post-breach. Notably, many of these fake sites shared the exact page title “Bybit Help Center”.
Figure 2: Phishing theme leveraging the help center feature amidst the Bybit incident
Following the event, threat actors created “Bybit coin”, in other words, a crypto coin of a cryptocurrency platform. Presumably this would be used to attract users seeking recovery options after the incident through brand recognition.
Figure 3: Bybit-named crypto token entering the ecosystem right after the hack was announced
Various websites were created as exact replicas of the official website, in which different tokens were featured for investment. This would likely be done to lure victims to enter login information in order to steal passwords and then offer a fake “help” feature to obtain supposed refunds and withdrawals.
Figure 4: Phishing campaign replicating Bybit’s homepage to lure investors
Several websites in multiple languages were created to target regional victims who likely invested in the Bybit crypto platform, as well as to lure investors by announcing new solutions.
Figure 5: New announcement on phished instance of a Bybit page, suggesting chaining to a new campaign
A few weeks post-incident
A few weeks later after the news and shock of the Bybit incident settled, the phishing themes transitioned away from withdrawals, information, and refunds via replicas of the legitimate site. New campaigns pivoted from exploiting urgency to a more sustained, training-focused strategy.
Figure 6: Crypto learning and guides being offered to investing enthusiasts on phished instances of Bybit page
Following the breach, phishing websites attracted victims with “crypto and training guides” and exclusive rewards intended for curious enthusiasts planning to enter the crypto ecosystem. This is a hook with the potential to make the phishing campaign successful by incentivizing users to get free coins.
Despite the shift to these “crypto and training guides”, the campaigns maintained a connection to the earlier withdrawal scams by including “how to withdraw from Bybit guides”. This creates a flow of traffic between learning resources fakes and withdrawal phishing attempts.
The research team also noted an automated strategy for rapid deployment of domains. Ordered “-a”, “-b”, “-c”, “-d”, “-e”, and “-f” suffixes indicate variations of the main domain likely made for phishing attacks, while maintaining a naming convention for legitimacy.
Truncating short forms of Bybit to avoid detection
While most Bybit-related domains were successfully detected and mitigated, researchers observed a new evasion tactic: truncated domains using ‘bb’, which allowed phishing campaigns to remain undetected and active.
As a general rule, users should exercise caution when visiting and engaging with domains related to financial activities. In the case of the Bybit incident, make sure to stay updated with the latest information to avoid inadvertently stumbling into a scam. Avoid engaging with domains (URLS) that contain “bybit” keywords with random strings of prefixes or suffixes. Monitor your ledger activity for any anomalies and harden your account security by leveraging multi factor authentication measures.
From an organizational perspective, it is essential to preemptively report related malicious domains through engagement with registrars, hosting providers, and abuse teams. Since Bybit has a massive customer base, it is essential to continuously track Bybit-related domain registrations and social media accounts.
Organizations can utilize predictive models to detect Bybit and Bitget-related malicious infrastructures before they launch.
Ready to see BforeAI in action?
Get a personalized demo
Talk to one of our experts and deploy in minutes.
No implementation needed. Works right out of the box!
如有侵权请联系:admin#unsafe.sh
