文章指出安全控制措施在预期与现实之间存在明显差距。尽管企业部署了先进的安全工具并组建了专业团队,但往往在遭受攻击后才发现这些措施并未按预期工作。传统方法如合规审计和渗透测试无法全面评估所有潜在漏洞,导致盲点长期存在。文章分析了安全控制失败的主要原因,并强调通过持续验证和自动化测试来提升检测和响应能力的重要性。 2025-4-2 14:30:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:20 收藏

There’s a clear gap between expectation and reality when it comes to security controls.
Despite deploying best-in-class security tools and building capable teams, many organizations discover the truth only after a breach: their controls weren’t working as expected.
Think of changing a lightbulb—you turn it on to check if it works. Security controls rarely get the same validation. Instead, success criteria become “don’t break production,” which doesn’t actually test whether the security controls are effective.
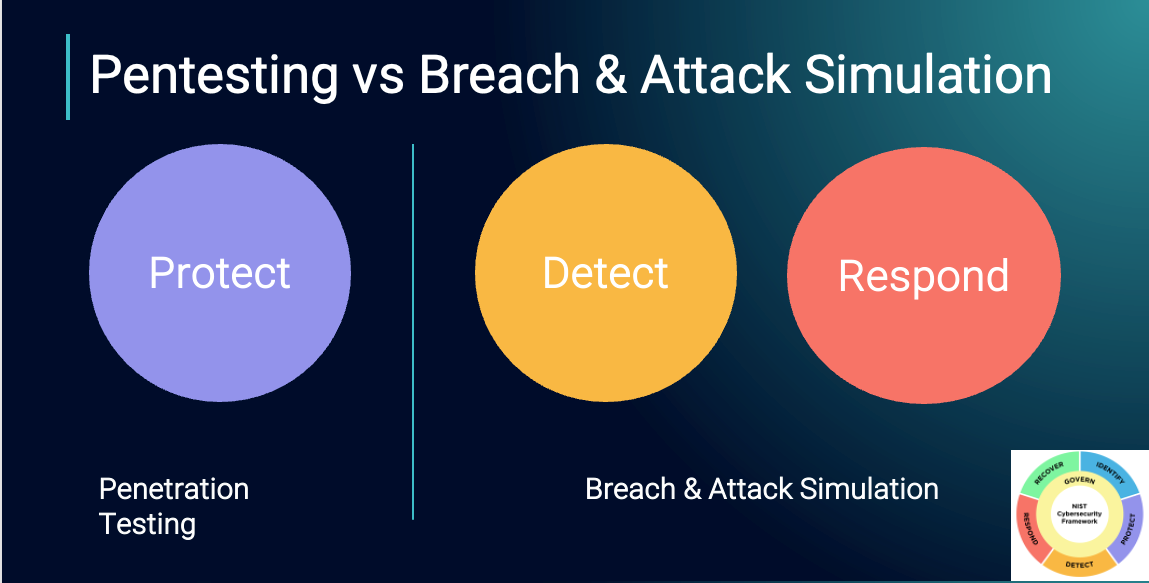
It’s not for lack of trying, but traditional methods—such as compliance audits and penetration tests—don’t fully answer the question, “Would we win?” if attacked.
As a result, blind spots persist.
Traditional Security Testing Falls Short
Compliance audits focus on policy and process but rarely engage in operational assurance testing that confirms, “Does this actually work as expected?”
Answering “Do you have antivirus software?” is very different from “How long does it take for a malicious file to be removed and your team to be alerted?”
Penetration tests can highlight security gaps but often reflect a specific attack path chosen by the testers rather than a comprehensive evaluation of all potential failure points.
The end result? Gaps (or blind spots) that typically aren’t discovered until someone else finds them for you.
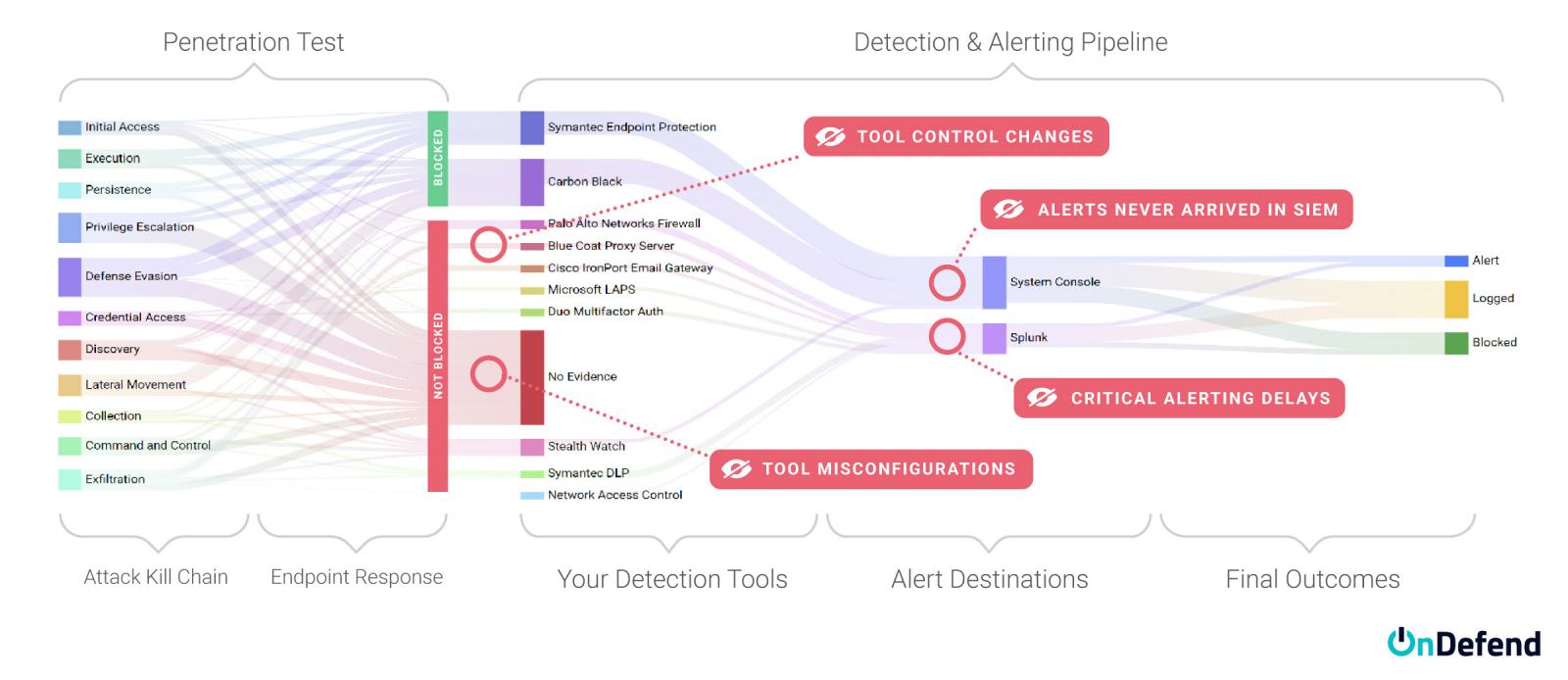
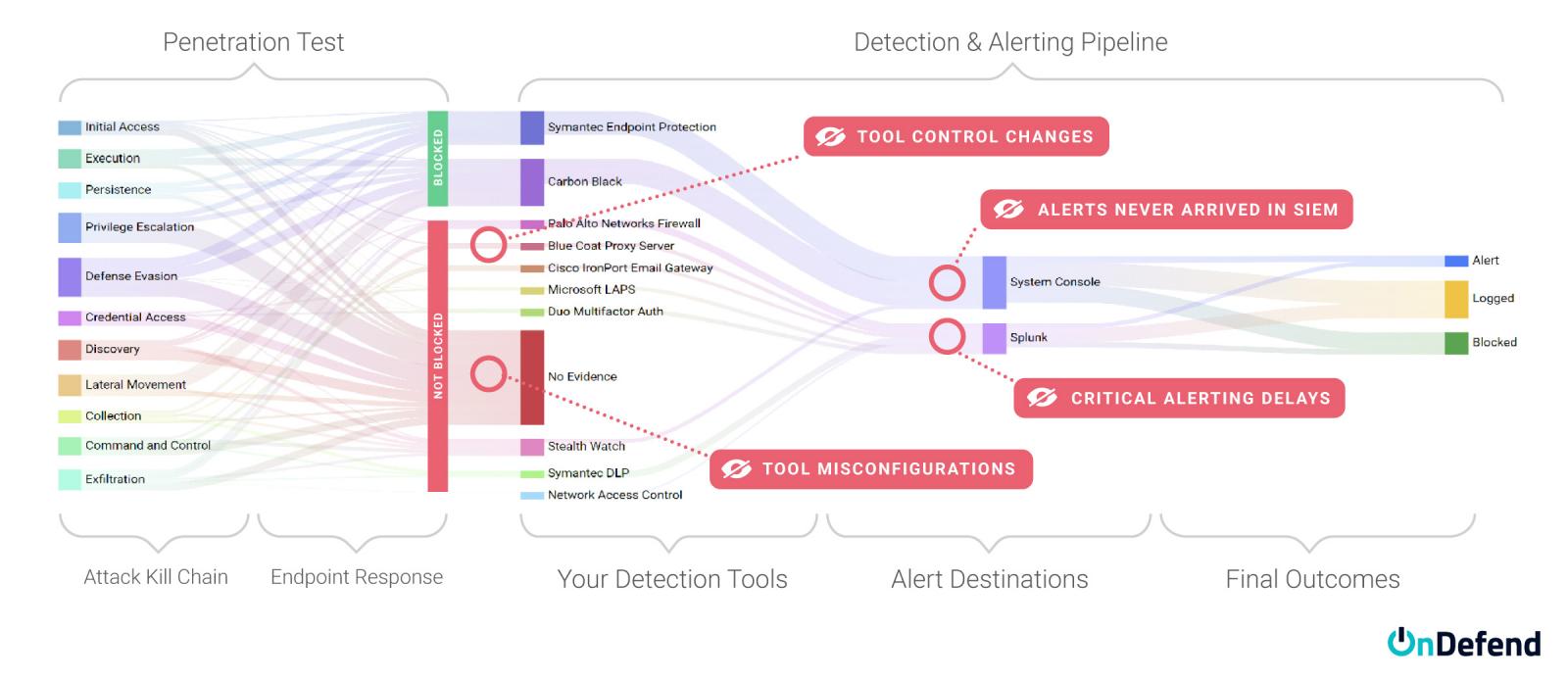
Five Most Common Reasons Security Controls Fail
Failures occur in both security tools—such as Secure Email Gateways (SEGs), Endpoint Detection and Response (EDR), and Security Information and Event Management (SIEM) systems—and in security teams, whether in-house or managed detection and response (MDR) providers.
We can categorize these into organizations threat prevention, detection, and response investments.
Top Five Causes of Threat Prevention, Detection, and Response Failures
- Policy Sprawl – Often the ideal policy from a security perspective clashes with the needs for authorized activity. This means your population within the security tool gets spread across a variety of policies with different settings and rules, often with significant differences to the overall performance. We often see organizations develop very well-crafted policies for their EDR tools and then realize that the majority of the fleet population is in the default policy, missing the opportunity to capitalize on the work performed by the team.
- Unintended Config Changes – False positive alerts consume most of a SOC analysts time. What if the configuration changes to reduce this noise accidentally silences true positive events as well? Errors in the alert query or accidentally applying the exception to all systems happen frequently.
- Ability to Execute the Playbook – Most organizations have done an excellent job building their threat hunting and incident response playbooks. But do the analysts ever get a chance to execute those activities in production? If you have an expectation that a SOC analyst can execute a fleet-wide hunt for a file with a given hash value, chances are not everyone on the team can do that correctly without ongoing training.
- Undersized Deployment –The security tool deployment fit initially, but as the environment grows, do they have the capacity and licensing to keep up? It’s not uncommon for undersized deployments to result in very long processing times, which translates to delays in your team being alerted to malicious activity, sometimes hours.
Real-World Example
A customer had added some new data sources to the collected telemetry, these new logs coming from end-user devices across the fleet. The sudden increase in logging overwhelmed the SIEM (Security Information and Event Management) system they had, creating a massive backlog of logs to be processed. The alerts they were looking for would arrive – 6 hours after the event had occurred. It was only when automated testing was introduced that this issue was discovered.
- Changes around the Tools – Often the security tool itself works great – but the environment around the tooling has changed to the point that the tool is no longer effective.
Real-World Example
An organization hired a third party for security monitoring, including a network IDS analyzing traffic from core routers. After an attack went undetected, they asked the vendor why—only to learn a network change months earlier had cut off traffic to the IDS. Despite receiving no data for months, it never triggered an alert or error.
The Need for Continuous Validation
The only way to combat these failures is by regularly testing security detection processes. To scale this effectively, control tests must be automated pointing out defects while cataloging successes and calculating key metrics such as Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Transitioning Continuous Testing Mindset
Managed Breach & Attack Simulation (BAS) services provide ongoing assurance without adding operational burden. When combined with penetration testing, BAS ensures a more comprehensive security strategy.
Holding vendors accountable is another key step—continuous testing provides data-driven evidence to measure vendor performance against SLAs, helping organizations demand better service, renegotiate contracts, or compare solutions before making purchasing decisions. Lastly, security leaders must communicate their effectiveness in business terms, using metrics like detection rates, response times, and financial risk reduction to quantify security’s value and in some cases leverage that data to lower cyber insurance premiums.
Trust but Verify Your Security Investments Will Work
Security leaders have always sought assurance that their cybersecurity investments perform as intended. With corporate stakeholders demanding measurable proof, continuous security validation bridges security, risk reduction, and business objectives—turning cybersecurity from a cost center into a strategic enabler.
OnDefend’s Ransomware Defense Validation managed service enables security teams to continuously test and validate their security controls, ensuring real-time visibility into potential blind spots.
Don’t let the bad guys do the validating for you. Stop assuming your controls will work—prove it.
See the difference continuous validation can make within your security program.
Learn More About a Customized Defense Validation Program.
Sponsored and written by OnDefend.
如有侵权请联系:admin#unsafe.sh