CVE-2025-1974
Kubernetes Ingress NGINX 存在远程代码执行漏洞,未认证攻击者可在特定条件下利用此漏洞在 ingress-nginx 控制器上下文中执行任意代码,可能导致秘密泄露。建议更新至最新版本、限制网络访问并禁用相关组件以缓解风险。 2025-3-26 20:47:5 Author: www.horizon3.ai(查看原文) 阅读量:44 收藏
Kubernetes Ingress NGINX 存在远程代码执行漏洞,未认证攻击者可在特定条件下利用此漏洞在 ingress-nginx 控制器上下文中执行任意代码,可能导致秘密泄露。建议更新至最新版本、限制网络访问并禁用相关组件以缓解风险。 2025-3-26 20:47:5 Author: www.horizon3.ai(查看原文) 阅读量:44 收藏
Kubernetes Ingress NGINX Remote Code Execution Vulnerability
A security vulnerability in Kubernetes exists under certain conditions where an unauthenticated attacker with access to the pod network can achieve arbitrary code execution in the context of the ingress-nginx controller. This can lead to disclosure of secrets accessible to the controller.
Unauthenticated attackers can exploit this vulnerability to execute arbitrary code leading to system
Mitigations
- Update to the latest version of Ingress NGINX Controller.
- Ensure the admission webhook endpoint is not exposed externally.
- Enforce strict network policies so only the Kubernetes API Server can access the admission controller.
- Temporarily disable the admission controller component of Ingress-NGINX if you cannot upgrade right away.
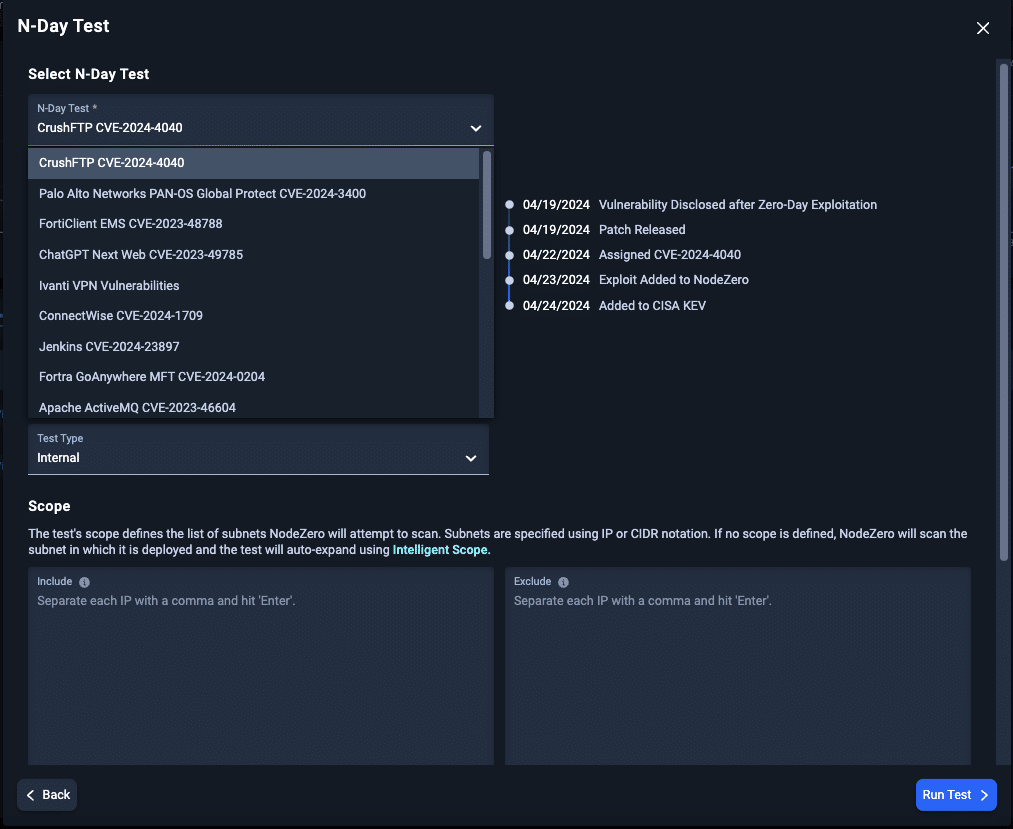
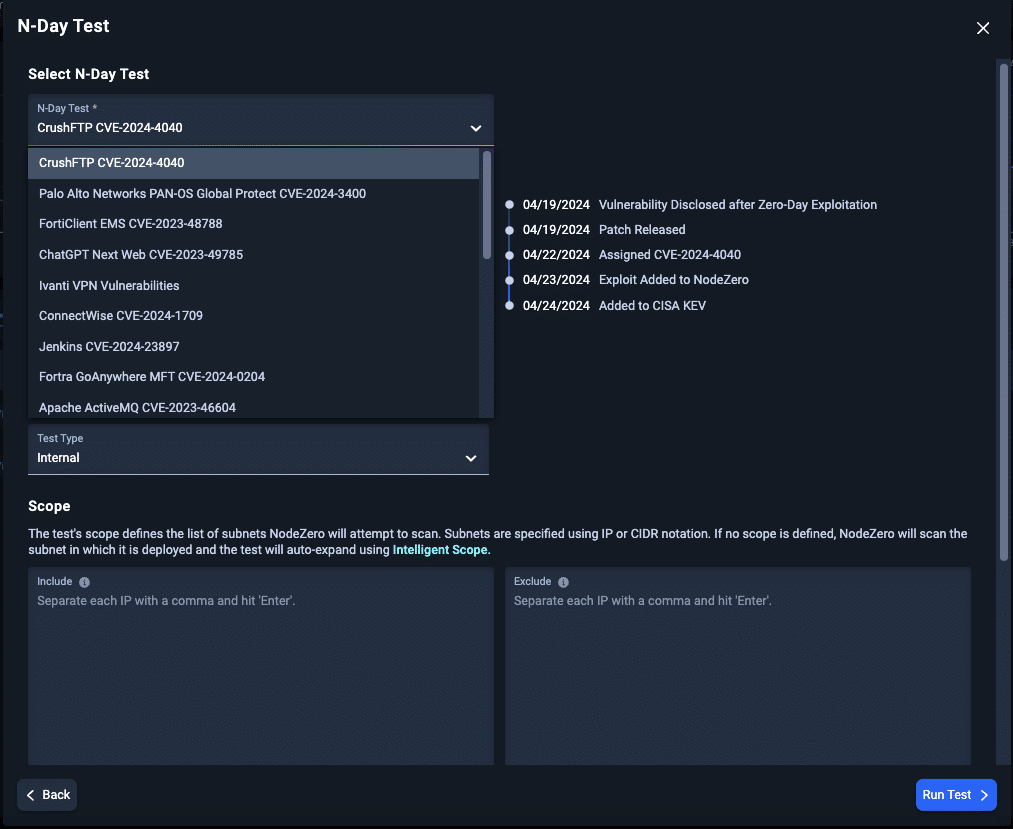
Rapid Response N-Day Testing
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
文章来源: https://www.horizon3.ai/attack-research/vulnerabilities/cve-2025-1974/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
