现代组织依赖智能AI提升效率和自动化关键业务功能,但内部API安全隐患可能导致数据泄露和业务中断。攻击者可利用API漏洞绕过安全控制, Wallarm通过API发现、业务逻辑识别和实时监控等技术保护企业免受此类威胁。 2025-3-26 11:12:17 Author: lab.wallarm.com(查看原文) 阅读量:14 收藏
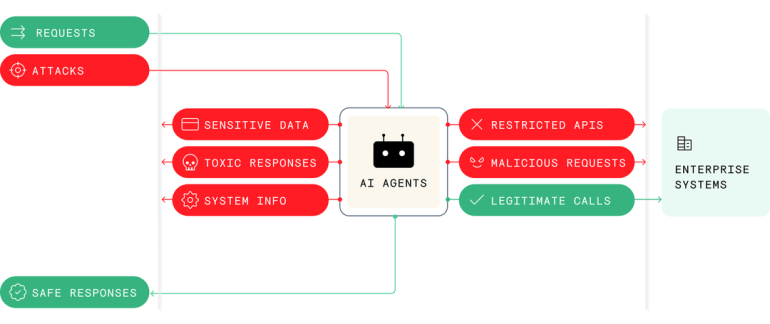
Modern organizations are becoming increasingly reliant on agentic AI, and for good reason: AI agents can dramatically improve efficiency and automate mission-critical functions like customer support, sales, operations, and even security. However, this deep integration into business processes introduces risks that, without proper API security, can compromise sensitive data and decision-making.
Challenging the Myth of Secure Internal APIs
Part of the problem is that far too many organizations assume that internal API communication is inherently secure when this isn’t the case. Even internal APIs can have vulnerabilities that attackers can exploit, especially when accessed by AI agents.
This misconception stems from a broader flaw in how businesses think about the security of their core business logic and functionality. Organizations typically assume that if they have proper authentication and authorization controls, their critical business controls are safe. But, in reality, attackers can bypass these controls by targeting vulnerabilities in the underlying APIs and business logic.
The Risks of Vulnerable Business APIs
AI agents are inherently linked with APIs. While essential, this integration creates a significant risk of exposing sensitive data and critical business functions to malicious actors. API vulnerabilities enable attackers to manipulate core business logic and functionality, allowing them to bypass authentication controls, modify transactions, disrupt operations, or even take full control of an organization’s systems. Some examples of this include:
- Altering Financial Records: Attackers could find a way to exploit a vulnerable API used by an AI-agent-powered accounting bot to alter financial records or even initiate fraudulent transactions.
- Resetting Customer Passwords: Malicious actors could identify weaknesses in an API used by a customer support bot that could reset customer passwords. By crafting malicious requests to the API, attackers could bypass the bot’s authorization checks and trigger password resets for customer accounts.
Sometimes, attackers don’t even need to do anything to wreak havoc. Organizations using AI agents to query internal data are at risk of exposing sensitive information. This is because AI agents often lack contextual awareness, meaning that they can share more information – often confidential information – than is necessary.

Proactive Strategies for Securing Business APIs
So, how can organizations mitigate the hidden risks lurking in the business logic of their APIs? Here’s Wallarm’s approach.
Protection from Business Logic Attacks via APIs
APIs are the front door to an application’s business logic, and attacks abuse the business logic exposed via those APIs. Protection from business logic attacks has to occur at the API layer. Here’s how Wallarm does it:
- Comprehensive API Discovery: Organizations can only protect the APIs they are aware of. Wallarm’s API Discovery feature automatically discovers and catalogs all API endpoints to ensure that no critical logic is overlooked.
- Automated Business Logic Identification: Understanding which endpoints exist is necessary, but not sufficient. Wallarm also automatically identifies which endpoints are connected to key sensitive business flows, like authentication, billing, and AI.
- Context-Aware Analysis: Our platform doesn’t just look at isolated requests; it considers the entire session’s context to detect subtle deviations from normal business logic execution, even when attackers try to blend malicious actions with malicious user behavior. Combined with identifying associated business flows, Wallarm can effectively protect APIs from business logic attacks.
Implement Robust Authorization Mechanisms
Organizations must also implement robust authorization mechanisms. However, that doesn’t mean just implementing basic access validation. Organizations must enforce strict, granular access controls. Wallarm’s platform does just that.
We enable the creation of detailed, role-based policies that determine what actions can be performed at specific authentication endpoints. This ensures that sensitive functions, like financial transactions or administrative actions, are only accessible to users with the right credentials and privileges.
Monitoring for Anomalous Behavior
It’s also important to understand the context of API interactions and detect deviations from normal behavior. Our real-time API monitoring and session tracking features aggregate individual API requests into full sessions, granting visibility into a user's sequence of actions to detect attacks that unfold over multiple steps, like account takeover or complex business logic attacks.
What’s more, Wallarm’s platform uses machine learning (ML) algorithms to establish a baseline of normal API behavior and monitor incoming API calls for deviations from these norms, such as unusual request rates, anomalous query patterns, or atypical access to sensitive endpoints. This helps detect threats before they materialize.

Learn More About How Wallarm Secures Agentic AI
As AI agents become a more important part of everyday business operations, organizations must pay more attention to API security. Wallarm can do that for you.
Wallarm provides API-first security for AI systems by protecting AI agents, AI proxies, and APIs with AI features. It prevents injection attacks and data leakage, controls costs, and ensures secure, compliant operations.
Want to find out more about Wallarm’s approach to securing agentic AI? Book a free AI penetration test today, and you’ll get a hands-on security assessment of your AI-powered APIs, insight into your vulnerabilities, and a detailed security report with actionable insights to strengthen your AI defenses.
What are you waiting for? Book today.
如有侵权请联系:admin#unsafe.sh