Cloak 勒索软件团伙声称对 2 月针对弗吉尼亚州总检察长办公室的网络攻击负责,导致 IT 系统关闭和 134GB 敏感数据泄露。调查仍在进行中以确定影响和来源。该团伙自 2023 年起活跃,主要针对欧洲小中型企业,并通过多种手段获取网络访问权限。 2025-3-24 07:22:44 Author: securityaffairs.com(查看原文) 阅读量:26 收藏
Cloak ransomware group hacked the Virginia Attorney General’s Office

The Cloak ransomware group claims responsibility for a cyberattack on the Virginia Attorney General’s Office that occurred in February.
The ransomware group Cloak has claimed responsibility for a February cyberattack on the Virginia Attorney General Office.
A cyberattack on the Virginia Attorney General’s Office forced officials to shut down IT systems, including email and VPN, and revert to paper filings. Chief Deputy AG Steven Popps called it a “sophisticated attack.” The breach was detected in February, leading to notifications to the FBI, Virginia State Police, and the Virginia Information Technologies Agency. Investigations are ongoing to assess the impact and source of the attack.
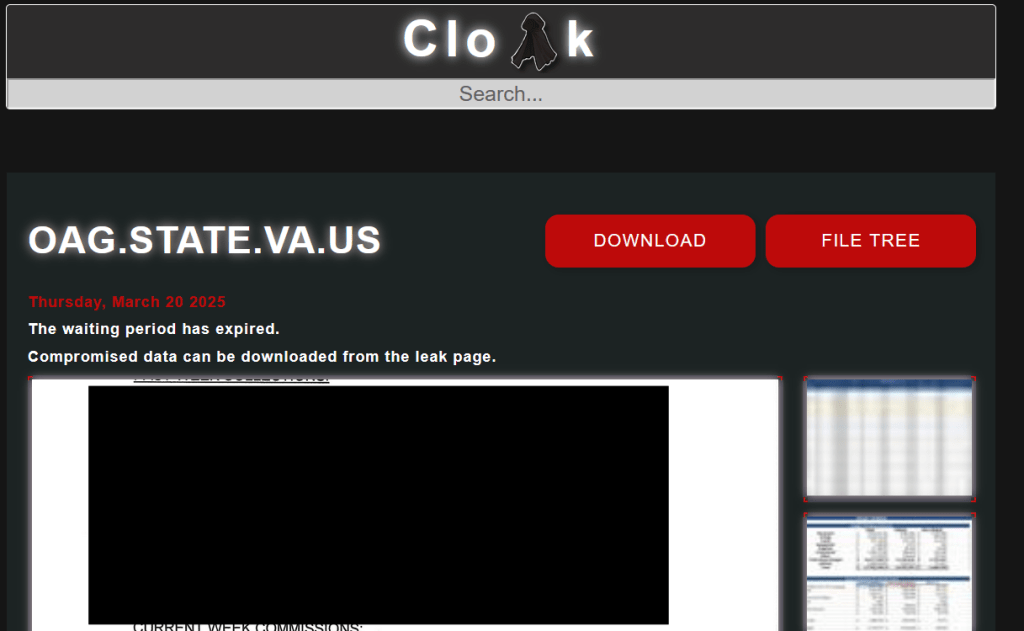
The Virginia Attorney General’s Office did not share details about the attack. On March 20, 2025, the group added the VA General’s Office to the list of victims on its Tor leak site.

The group said that the waiting period had expired and claimed the theft of 134GB of sensitive data.
Initially, the group published screenshots of stolen data as proof of the attack, now the whole archive can be downloaded from the leak page.
The Cloak ransowmare group has been active since at least 2023 and breached more than one hundred organizations across the years.
“Cloak primarily targets small to medium-sized businesses in Europe, with Germany as a key focus. The group has extended its operations to countries in Asia and targets various sectors, including healthcare, real estate, construction, IT, food, and manufacturing.” reads a report published by Halcyon. “Cloak’s attack strategy involves acquiring network access through Initial Access Brokers (IABs) or social engineering methods such as phishing, malvertising, exploit kits, and drive-by downloads disguised as legitimate updates like Microsoft Windows installers.”
The group uses an ARCrypter ransomware variant, derived from Babuk’s leaked code, to encrypt files after infiltrating a network.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)
如有侵权请联系:admin#unsafe.sh