GitHub Actions和Apache Tomcat近期曝出的安全漏洞引发广泛关注。尽管初始评估认为影响重大,但实际分析显示影响范围有限。GitHub Actions漏洞(CVE-2025-30066)仅少量仓库受影响且无敏感信息泄露;Apache Tomcat漏洞(CVE-2025-24813)因配置要求高而未造成实质风险。组织应根据实际情况优先处理真正威胁。 2025-3-21 20:9:58 Author: www.horizon3.ai(查看原文) 阅读量:15 收藏
What to know about recent Github Actions and Apache Tomcat vulnerabilities—before you investigate.
Trendy vulnerabilities aren’t always worth the hype—panic-driven responses often lead to wasted time and resources. This is top of mind for us as we’ve researched recent issues regarding Github Actions and Apache Tomcat. Like many vulnerabilities they have the potential to be critical, but after assessing relevant data from across customers’ production environments, Horizon3.ai’s Attack Team found actual impact is not as widespread as the publicity surrounding them may have you believe.
- GitHub Actions vulnerability (CVE-2025-30066) initially appeared to be widespread but Horizon3.ai’s analysis of customer exposure did not reveal any leaked secrets.
- Apache Tomcat vulnerability (CVE-2025-24813) garnered attention regarding the RCE potential, but Horizon3.ai determined that no customer instances are impacted, even those running vulnerable versions.
In an ideal world, immediately applying patches and mitigations for any given security issue is, well, ideal. But in reality that’s not practical. We all face resource constraints and business context that may warrant monitoring a risk vs. applying a patch.
Whenever a new vulnerability surfaces and makes headlines, organizations are left scrambling to determine whether they’re at risk. Failing to do so introduces major exposure if a vulnerability does turn out to be critical. But with a myriad of security products misleading users with claims of hundreds of critical installations, teams are left overwhelmed with what to fix, what to fix first, and most critically, why.
Let’s dive into what we know about these latest examples.
tj-actions/changed-files (CVE-2025-30066)
The popular third-party GitHub Action tj-actions/changed-files—used to track file changes in repositories—was compromised before March 14, 2025. This backdoor introduced malicious code capable of exfiltrating sensitive information, such as API keys, tokens, and credentials, from repositories utilizing this action. Reports suggest that over 23,000 public repositories may have been affected.
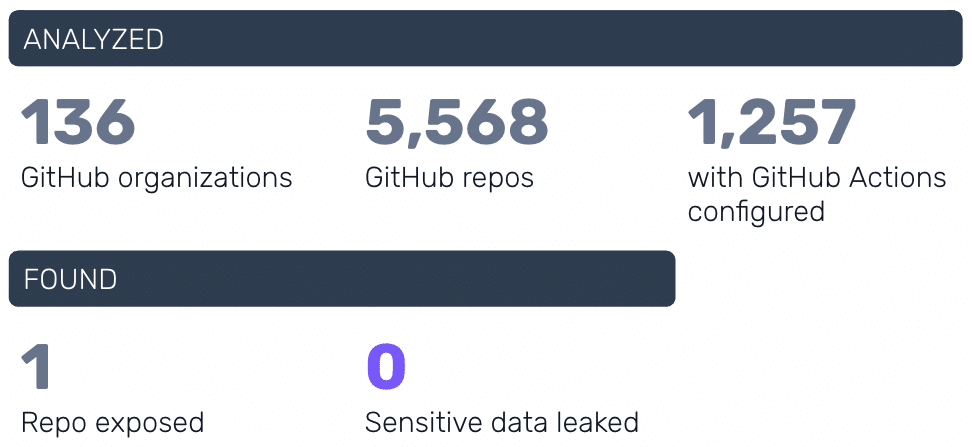
Horizon3.ai’s Attack Team, the experts behind NodeZero Rapid Response, conducted an in-depth analysis of this vulnerability to assess its potential impact on customers. We identified 136 GitHub organizations of interest, containing over 5,000 repositories. Of these, roughly 1,200 had GitHub Actions configured. After thorough investigation of the workflows, logs, and other configurations of these repositories, we located just one public repository that was exposed to the tj-actions/changed-files compromise. Despite the exposure, no sensitive information was found to have been leaked or exfiltrated from the affected repository.

This aligns with broader research suggesting that while this compromise had the potential for significant impact, actual exploitation was highly dependent on repository configurations, workflow permissions, and the presence of long-lived secrets.
At your disposal
Our expert Attack Team’s mission is to take the burden of wading through the noise and hype off of security teams. We’re uniquely equipped to do this given the amount of data we have from the NodeZero platform which customers have used to run >100K pentests.
We combine our research expertise with this data to understand who among our user base is exploitable, and with NodeZero Rapid Response, proactively alert them and provide the information they need to fix the vulnerabilities that are actually exploitable.
Apache Tomcat (CVE-2025-24813)
On March 10, 2025, an unauthenticated remote code execution (RCE) vulnerability affecting Apache Tomcat was publicly disclosed. Many reports claimed active exploitation in the wild, fueling widespread concern.
While rated Critical by typical vulnerability scoring mechanisms such as CVSS, successful exploitation requires a combination of non-default configurations that are unlikely to be found in most real-world deployments:
- Tomcat’s default servlet must be in use with the readonly attribute set to false. This configuration is disabled by default and rarely enabled in production environments.
- File-based session persistence must be in use. This is also a non-default configuration that few organizations make use of.
Despite the claims of active exploitation, the combination of these prerequisites means that most organizations are not at immediate risk. Even if scanning activity or exploitation attempts are detected, successful exploitation remains improbable in standard configurations.
The Horizon3.ai attack team analyzed over 10,000 publicly accessible Apache Tomcat customers endpoints and determined that none of these endpoints contained a vulnerable configuration.

Worth the Hype?
If your organization uses tj-actions/changed-files or Apache Tomcat, the ideal solution would be to take the time to patch and apply any necessary mitigations. But in the face of real-world capacity constraints and competing priorities, this likely doesn’t warrant going to the top of your priority list. As a recap after a thorough audit of our customers for both issues:
- Only one customer was found to be exposed to the Github Actions issue, though no information was leaked. This customer was promptly notified by NodeZero Rapid Response..
- Horizon3.ai has seen no evidence of customers using vulnerable configurations of Apache Tomcat, even if the versions in use are within the vulnerable range.
Conclusion
Security reports often state that vulnerabilities are being exploited “in the wild,” but this is ambiguous and can be misleading. Many outlets err on the side of caution, labeling any observed exploitation attempts—successful or not—as active exploitation.
It’s highly probable that both of these vulnerabilities have been and will continue to be scanned and probed by threat actors, but these probing attempts don’t necessarily equate to widespread, real-world impact.
While it’s important to stay informed and patch vulnerabilities, panic-driven responses can lead to wasted time and resources. Horizon3.ai equips customers with the information and results they need to appropriately prioritize security issues based on proven impact to their environments. This empowers them to focus on issues that genuinely carry risk to their infrastructure, not headline clickbait.
如有侵权请联系:admin#unsafe.sh